
IDA has been the standard for reverse engineering for many years, but the price of licensing for the software has kept the product from the reach of many small to medium size IT departments. This changes with the introduction of GHIDRA. GHIDRA is a set of open source tools released by the NSA that will allow security engineers to analyze and reverse engineer code for……yes FREE!
GHIDRA has been in development for many years and is now available to the public.
In this guide I will be adding the GHIDRA framework to our previous install of FLARE found here.
Navigate to https://ghidra-sre.org/ download and extract Ghidra
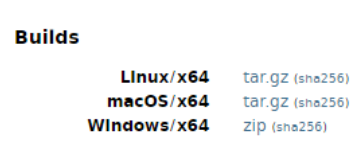
Install the needed JDK 11.0.2 from https://jdk.java.net/11 Windows/x64 zip. Extract.
Start -> Right-Click on Computer -> Properties -> Advanced Settings. Environment Variables…
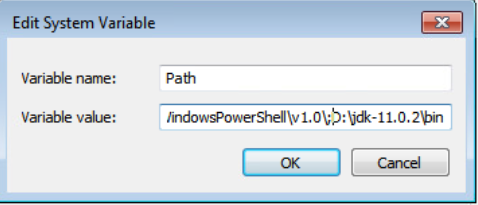
System Variables -> Path -> Add the path to JDK starting with semicolon ;D:\jdk-11.0.2\bin
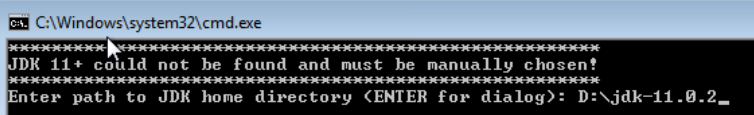
Navigate to extracted ghidra_9.0 directory and run the ghidraRun.bat. Enter the path to JDK D:\jdk-11.0.2
“Read” through Ghidra User Agreement -> I Agree
Create a snapshot of the VM before moving malware to the machine for analysis.

I will be grabbing malware from https://github.com/ytisf/theZoo. Once the file is pulled down I remove the interfaces from the virtual machine to eliminate any possible communication as a precaution during analysis.
Back in Ghidra -> File -> New Project…
Non-Shared Project -> Next – > Directory for Project -> Project Name -> Finish
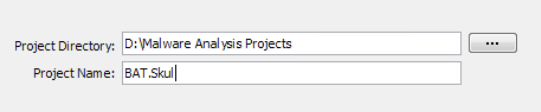
Drag over the desired malware and drop into the Active Project white space
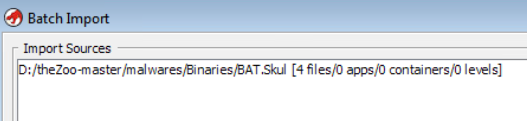
Select the Code Browser
File -> Open -> Select the imported PE file -> OK. At this point I also created another snapshot in VMware to allow dynamic analysis with the code already loaded into Ghidra.
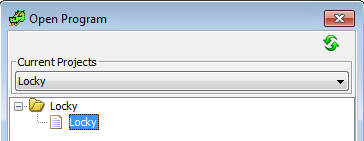
Allow Ghidra to analyze the code
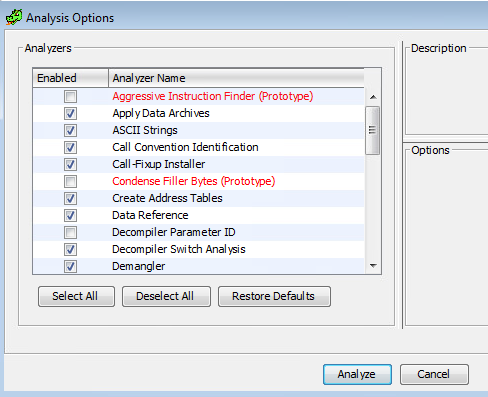
Default analyze options -> Analyze
We can now analyze the code in assembly:
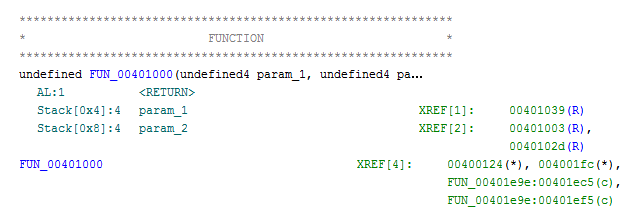
And the decompiled code:
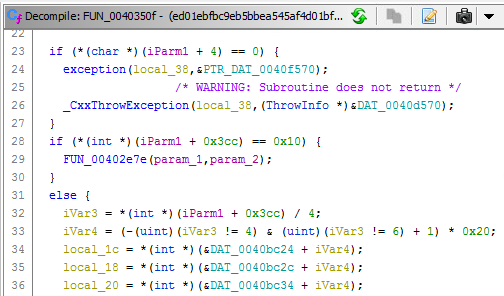
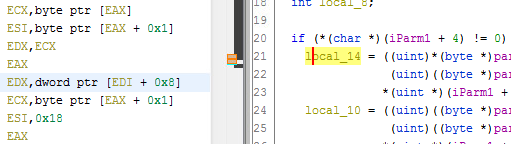
When clicking on the assembly code in the left pane, the right pane will show the decompiled code and visa versa.
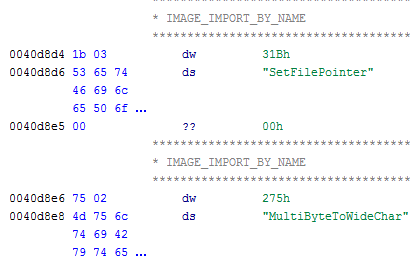
We can also see that analyzing strings in the software is easy and straight forward.
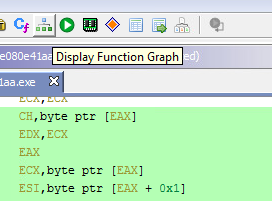
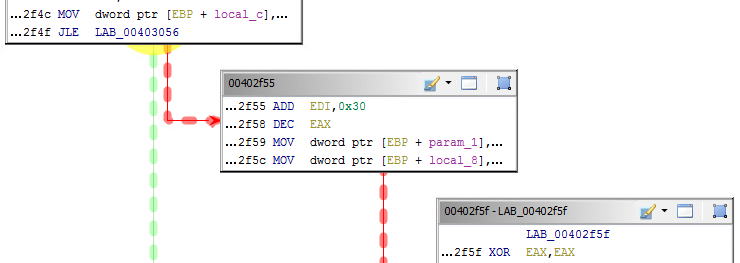
The function graph feature allows visual flow. Highlight the interesting code you would like to visualize and press the Display Function Icon.
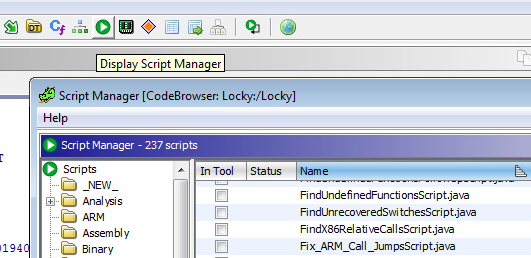
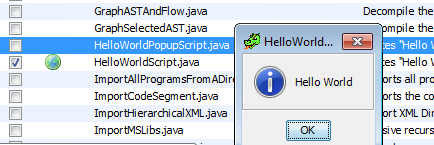
Ghidra also allows the user to create scripts in Java using the Ghidra Script Manager.
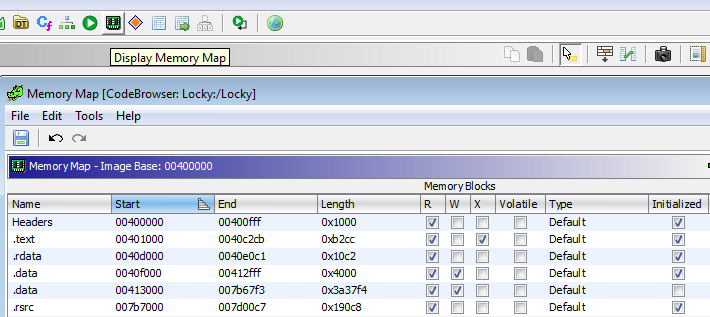
Memory map shows and allows configuration of the memory blocks that make up the memory structure of the file being analyzed.
Wow! Ghidra looks to be a great framework to build from. I will be using Ghidra moving forward for my reverse engineering projects and CTF challenges. Ghidra is powerful and opensource which is my preference when looking for security tools.
Be on the lookout for more blogs on how to use Ghidra in the future! Until next time, stay safe in the Trenches of IT!