
Now before we dive in, lets explain what we are doing, and why we are using this method.
DISA STIGS are DOD IA configuration standards used for systems that play a critical role in providing government services. Based the the capabilities of the system, these configuration changes will harden a system and reduce the attack surface. Least privilege and defense in depth are some of the essential concepts of security, and deploying a system that is fully STIG(ed) provides a solid foundation to a secure system. Learn more about DISA STIGs here.
As you can imagine, configuring a system with over 430 secure configurations can be a daunting and time consuming task. That’s where we bring in Ansible to fill in the gap. Ansible has a strong community of contributors that automate redundant tasks and post their code to Ansible Galaxy. We will be taking advantage DISA STIG RHEL 7 Ansible script by MindPointGroup. Check it out here.
Installing Ansible
Lets start by adding the needed repository and ensure all repositories are up to date.
[root@trenchesofit ~]# yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
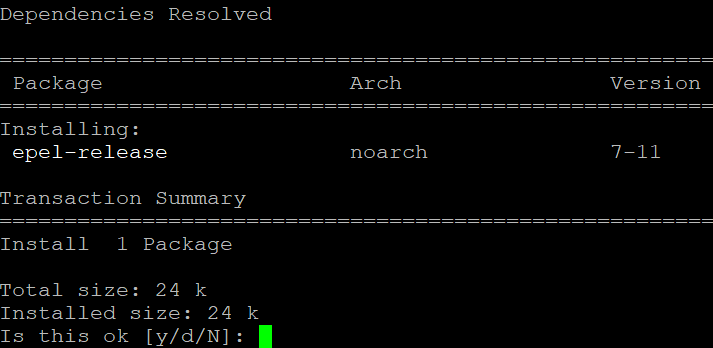
[root@trenchesofit ~]# yum update
Install Ansible.
[root@trenchesofit ~]# yum install ansible

Pulling Red Hat DISA STIG template for RHEL 7
[root@trenchesofit ~]# ansible-galaxy install RedHatOfficial.rhel7_disa_stig
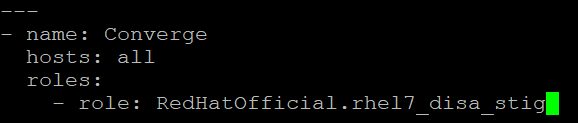
Edit the playbook with the correct role name RedHatOfficial.rhel7_disa_stig
[root@trenchesofit ~]# vi /root/.ansible/roles/RedHatOfficial.rhel7_disa_stig/molecule/docker/playbook.yml
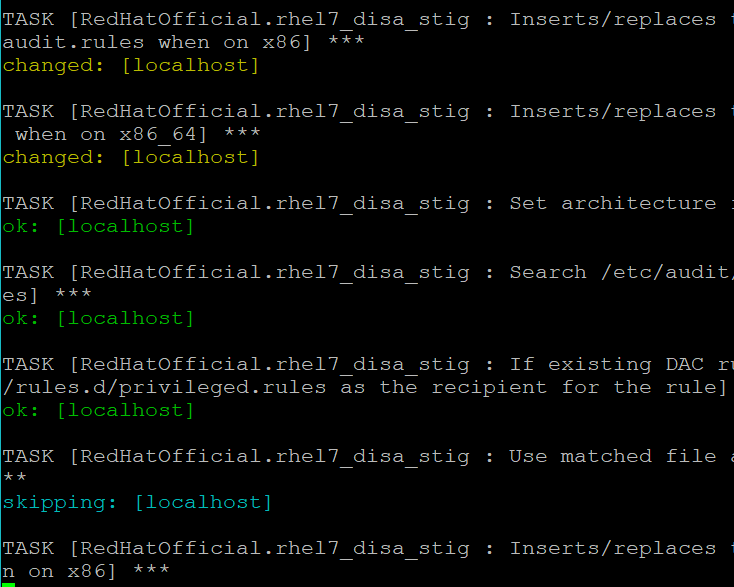
Execute the playbook with the following command
[root@trenchesofit ~]# sudo ansible-playbook -i "localhost," -c local playbook.yml
This will take a few minutes. Once complete you will receive a recap showing a summary of changes the playbook made to the system.
PLAY RECAP *
trenchesofit : ok=432 changed=236 unreachable=0 failed=0
Cleanup
[root@trenchesofit ~]# yum remove ansible
[root@trenchesofit ~]# rpm -qa | grep epel
[root@trenchesofit ~]# rpm -e epel-release-7-11.noarch
Once this is complete you can then do a quick check to see if changes have been made. I recommend doing a more thorough check using a compliance auditor such as Nessus. Keep in mind that the Red Hat ansible DISA STIG playbook may be a version or two behind, so some additional changes may need to be made to meet compliance requirements.
Let me know if you have any questions or concerns, and until next time…..stay safe in the Trenches of IT!