Zoneminder is an open-source surveillance solution that started before 2006. Since then the project has grown to be a fully featured solution for those looking to take physical security seriously. You can find the project on Github: https://github.com/ZoneMinder/zoneminder I decided to spend a bit of time testing the web application to see if I could …
Read More “Zoneminder – Web App Testing – Oct 2022”
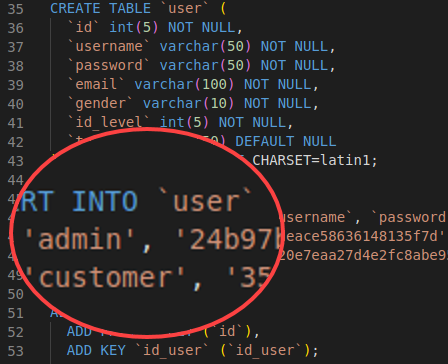
Vulnhub started hosting a machine named SecureCode: 1 on February 23rd, 2021. This machine was created by the user sud0root with a description of “OSWE-like machine”. Overall the machine was simple, but it did provide some good practice reviewing code and writing a proof of concept exploit script. Reconnaissance To begin, I executed a Nmap …
Read More “OSWE Prep – SecureCode: 1”
Hack the box released a machine named Falafel in 2018. The difficulty set by the community and HTB is Hard, and I can see why considering the machine required quite a few different attack types including blind SQL injection, password cracking, type juggling, file upload bypass, and abusing Linux permissions and group misconfigurations to finally …
Read More “OSWE Prep – HTB Falafel – No SQLMap”
The security community has compiled a well-known list of machines available outside of the PEN-200 Labs to help prepare for the OSCP exam, but few know that an OSWE list is in its infancy as well. The OSWE list can be found here. At the top of the Vulnhub list was Silky-CTF: 0x02. Though the …
Read More “OSWE Prep – VulnHub – Silky 0x02”
Burp Suite is a great tool not because it contains all the needed features to test a service, but because it can be customized to perfectly fit the needs of each engagement. A common issue with my day-to-day when testing APIs is the need to pull a dynamic parameter from an initial request to then …
Read More “Burp Suite – Custom Parameter Handler”
I ran across Deloitte’s CTF on ctftime.org while looking for some challenges to keep myself busy. The CTF timeframe was a bit longer than I was expecting, but I could just attempt the challenges as I have time. Let’s dig into some details about the CTF. Duration: July 2nd – July 26th “Hackazon is a …
Read More “Hacky Holidays – Space Race – CTF”
The bug bounty community has finally caught my attention and it’s time for me to take a stab at finding some web application vulnerabilities in the wild. Before I started this process I took a few weeks to get accustomed to the current toolset being used and how they work. So basically it comes down …
Read More “Bug Bounty VPS Build”
Recently I had the opportunity to take the PWK course offered by Offensive Security. Given how helpful the community has been during my journey, I felt it was my duty to provide a helpful write-up for all those pursuing the OSCP. The most useful questions I enjoyed reading were: What experience did you have before …
Read More “How I Passed the OSCP”
Offensive Security released the Linux machine Fail on January 28th 2021. The machine is rated intermediate by OffSec and hard by the community. I felt the box was more towards the easy end of intermediate. The machine requires a bit of knowledge using ssh keys for authentication and an application called fail2ban. For those unfamiliar …
Read More “Offensive Security – Proving Grounds – Fail Write-up”
Offensive Security’s ZenPhoto is a Linux machine within their Proving Grounds – Practice section of the lab. This machine is rated intermediate from both Offensive Security and the community. I feel that rating is accurate. Keep in mind that the IP will change throughout the screenshots and cli output due to working on the box …
Read More “Offensive Security – Proving Grounds – ZenPhoto Write-up – No Metasploit”