Malware analysis, like many other areas of information security, has an overload of tools and custom scripts. With so many options it is difficult to stay on top of the most current useful tools for doing static/dynamic malware analysis. I stumbled across a great resource recently and wanted to share. Check out FireEye’s flare-vm. This script is being updated regularly with the newest tools of the trade for Reverse Engineering and Malware Analysis.
I am setting this up using a Windows 7 VM.
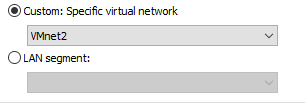
As with all malware analysis vm’s ensure that your network adapter is using a separate VLAN than your production machines.
Next, visit https://github.com/fireeye/flare-vm
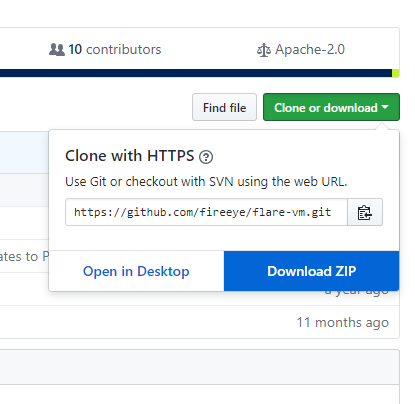
Download and extract the zip which will include: LICENSE.txt, README.md, flarevm_malware.ps1, install.bat, and install.ps1
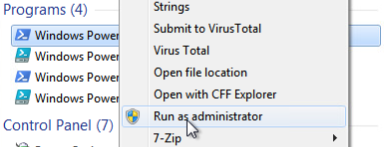
Run Powershell as administrator
Navigate to the download location and run install.ps1
The downloads/installs take a very long time so I spread the setup over a few nights. The script auto runs on boot and checks for any packages that are already installed on the machine so this caused no issues.
You will eventually receive a message in the terminal that will say “Installation has finished. Press enter to close:”
Side Note: The downloads will trigger IDS alerts.
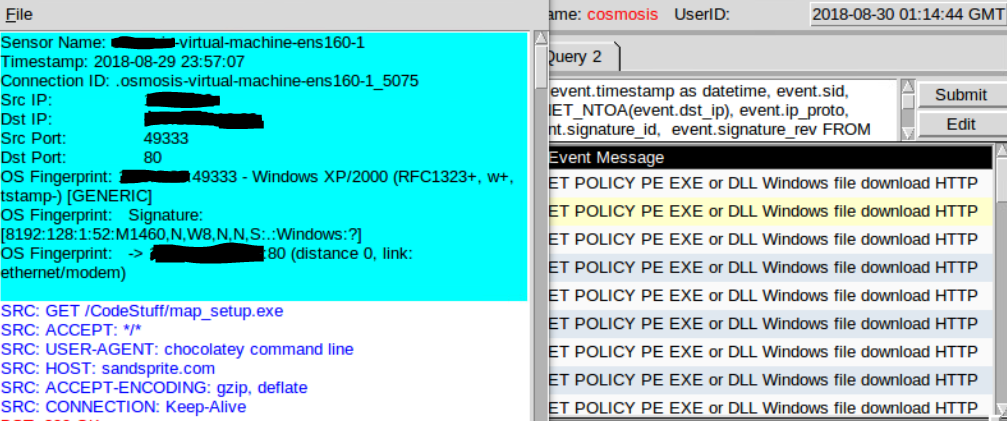
Now create a golden snapshot of the VM and your ready to install some malware.
I will be using this VM for malware analysis in future articles so until next time, Stay safe in the Trenches of IT.