This weekend I decided to check out the TUCTF Capture the Flag event. The event started on Nov. 23rd 2018 in the evening.
Location – Online: https://tuctf.com/challenges
The rules were simple:
- ABSOLUTELY no sharing flags
- There is no limit to team members
- Prizes are given to the top 3 placing collegiate and high school teams
- Prizes are limited to those participating in the United States
- Be a human being.
I will be participating solo. Lets get started.
Challenge #1: Welcome
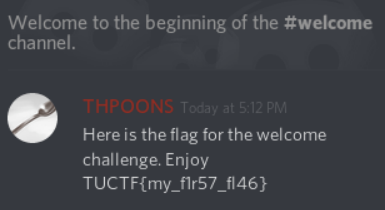
Easy enough. Next
Challenge #2: Mrs. White’s Messy Maids
Immediately saved the jpeg to the desktop expecting some steganography goodness. Then inspected the page and found this fella.
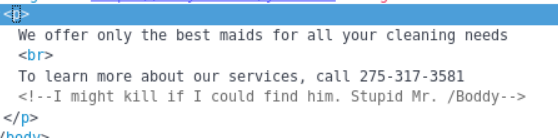
The slash is a dead giveaway.
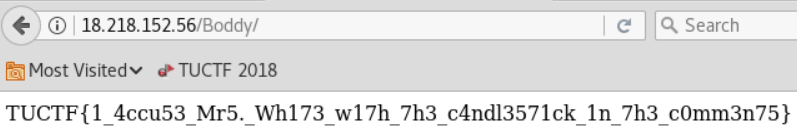
Challenge #3: Mr. Green’s Weird Website
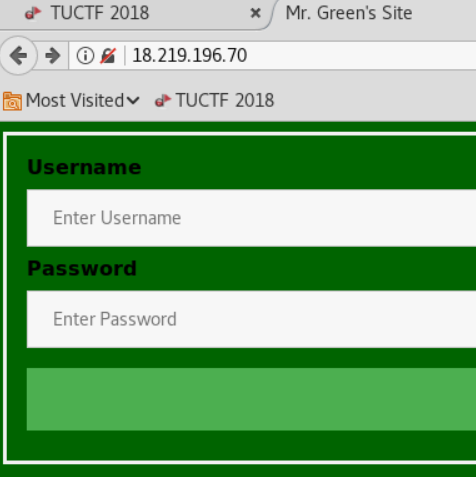
Login page with no odd findings in the source code, however when I entered a value, submitted then backed up to the original page. I found a new entry in the history dropdown.
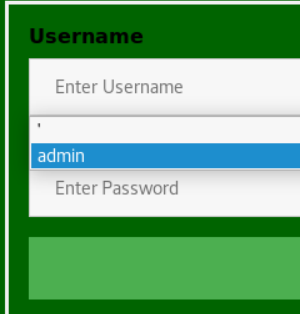
Decided to try admin/admin.
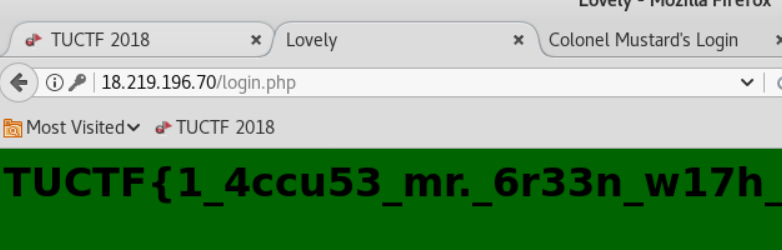
Lucky.
Challenge #4: Easter Egg: Copper Gate
Source looked normal, so decided to go straight to BurpSuite for a spider.
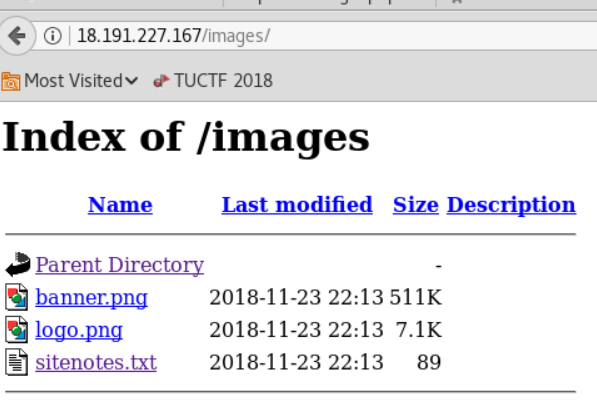
Visited the /images directory and seen sitenotes.txt (Looks interesting)
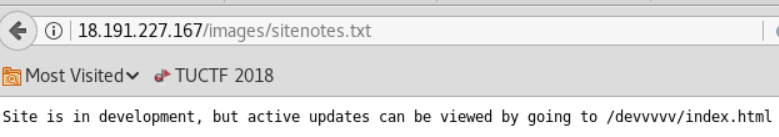


From the original spider you can see a directory for copper gate. Lets check that out.
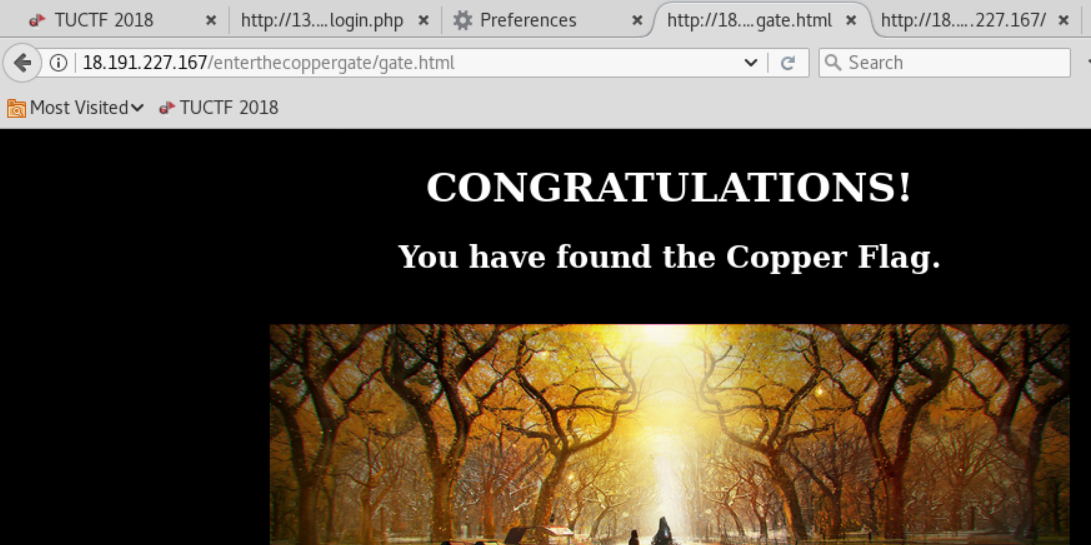
Included string. Looks like base64 encoding. Pasted the string into file named base.txt.
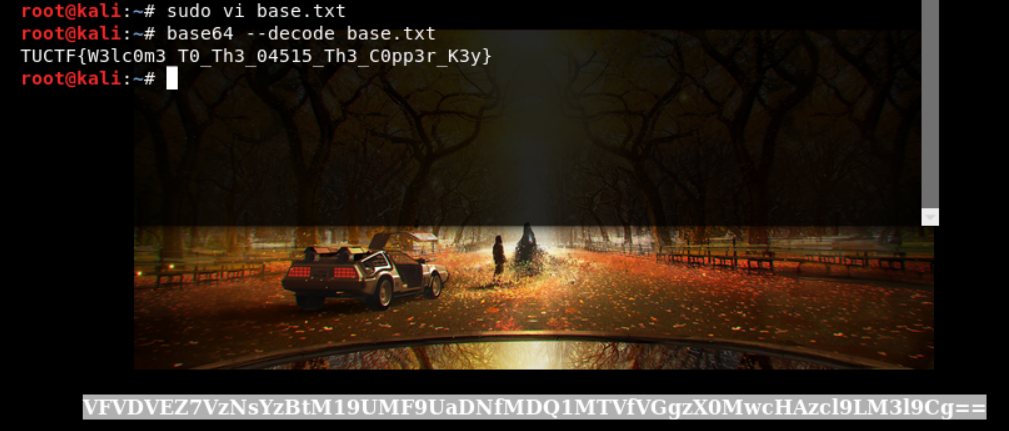
Indeed it was! Challenge complete.
Challenge #5: Danger Zone
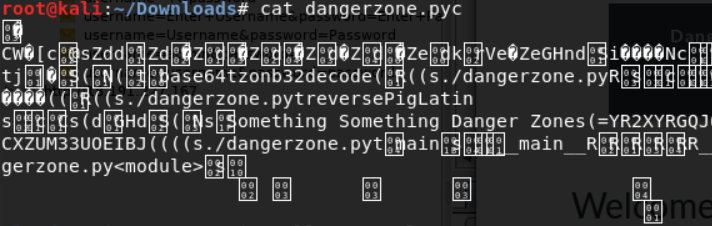
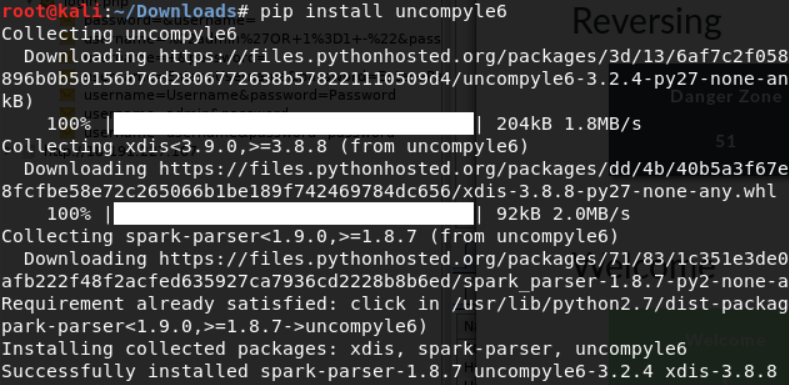
First we will need to uncompile the .pyc using uncompyle6
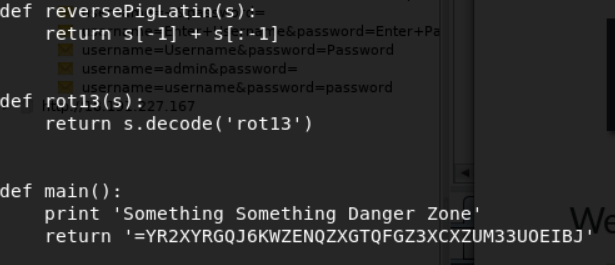
The .py includes many functions to decode messages, but the main function returns a base64 value.
So after running through the decoding process the order to decode the message was reverse > base64 > rot13 > lastchar to front. I modified the code in the main function for simplicity.
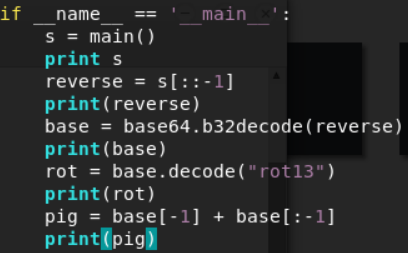
Now lets run this.
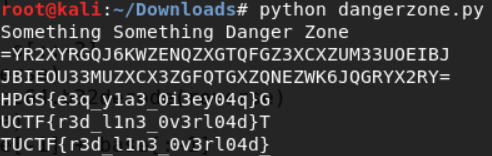
Ahh Haa. Challenge complete.
Results:
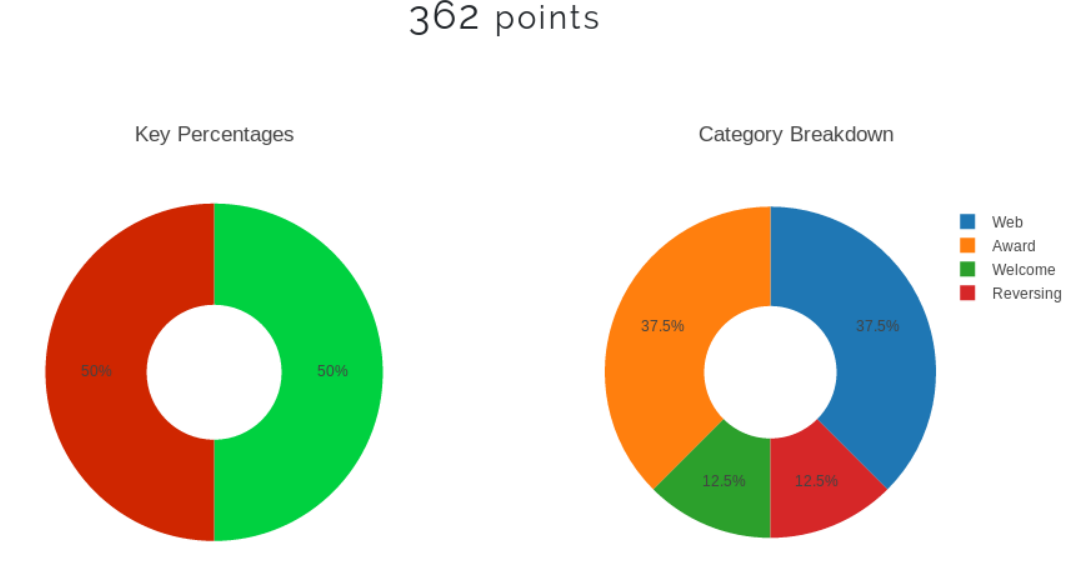
Lessons Learned:
Throughout the CTF I have picked up a few new skills including using the Repeater and Sequencer functions within BurpSuite. The CTF also pushed for additional research on the following header values and how they could be exploited: Cache-Control, If-None-Match, and If-Modified-Since.
Look for more posts on CTF challenges in the future, and until next time, stay safe in the Trenches of IT!