NMAP is a very useful tool used for discovering more information about a target host/network. This will normally be used in the early stages of penetration testing to find interesting targets that may be vulnerable. NMAP is also very useful for network administration and troubleshooting. NMAP has many more useful purposes and having it in your IT tool-belt will provide useful.
Tip: To build a virtual machine for testing click here.
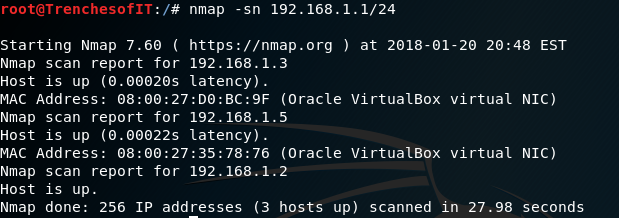
This command will allow you to scan an entire network range for live hosts.(The -sn will allow the scan to ignore port scanning for a faster scan result)
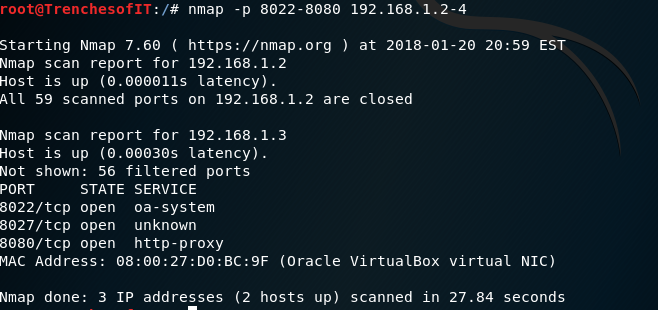
To Scan to see if specific ports are open you may use -p PORT NUMBER or RANGE. This command will scan ports 8022-8080 on hosts 192.168.1.2 through 192.168.1.4
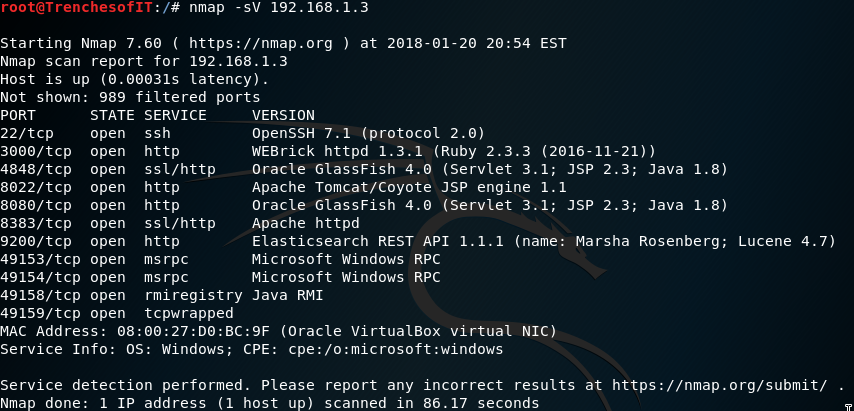
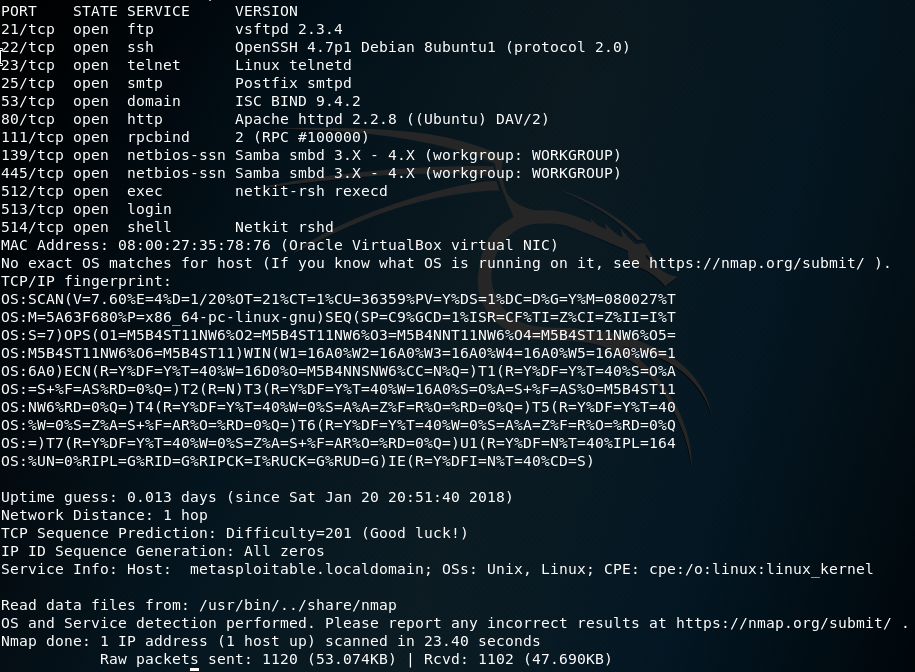
Next you want to probe open ports and determine what services and versions are running on the targets. To perform this you will use the nmap -sV (IP ADDRESS)
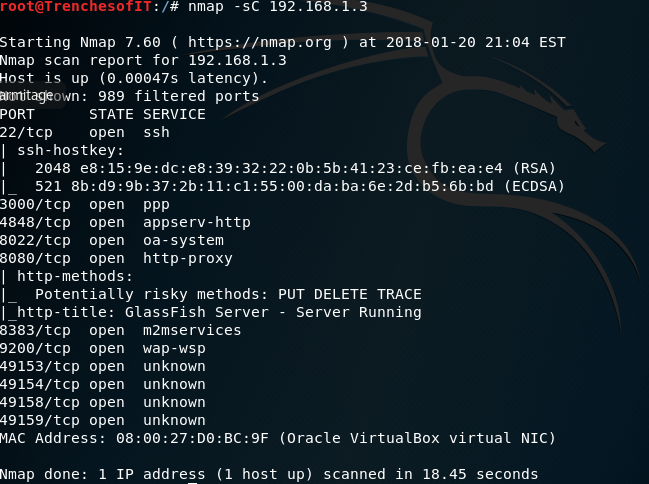
There are multiple scripts build into the NMAP framework that will probe deeper into the applications running on the host.
To run the default scripts provided by nmap use the -sC option. This option is very noisy and shows many alerts on IDS/IPS.
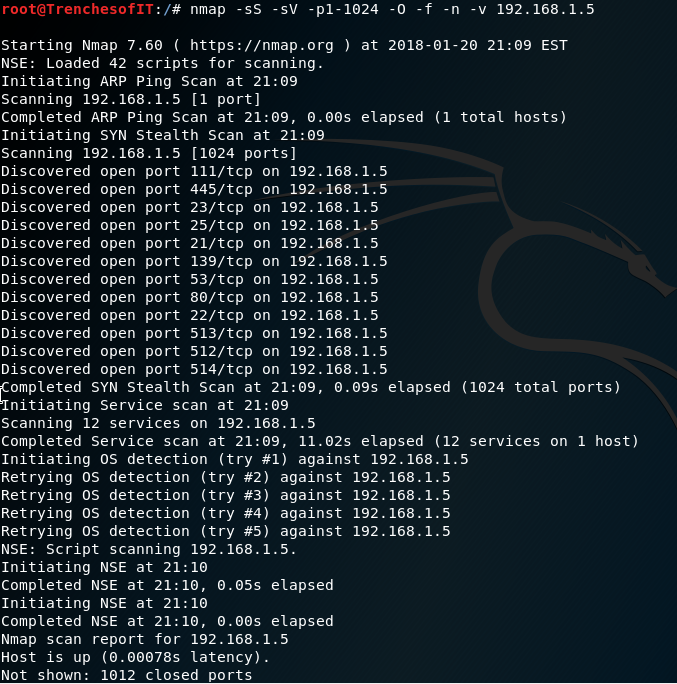
Running a more stealthy scan may be more preferred. Lets run through a common stealth scan using nmap. -sS = SYN Scan,
-sV = Probe open ports to determine service/version info, -p = Range of ports, -O = Enable OS detection, -f = fragment packets,
-n = Never do DNS resolution, -v = Increase verbosity level
For more details on NMAP check the man page (#man nmap)